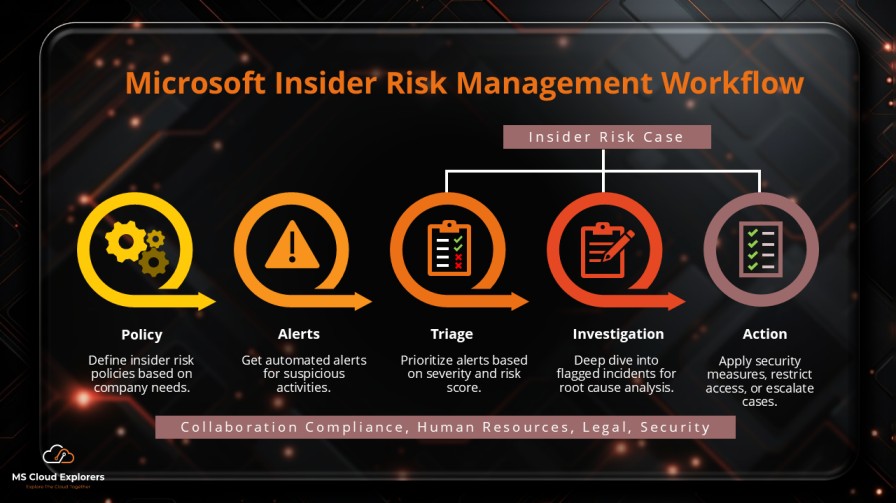
In today’s digital world, cybersecurity risks are no longer just about external threats. Insider risks, often from employees, contractors, or partners, can lead to significant harm—whether it’s from negligence or intentional malicious actions. Preventing these risks is crucial for safeguarding sensitive data and maintaining organizational trust.
What is Microsoft Insider Risk Management?
Microsoft Insider Risk Management is a tool in the Microsoft Purview compliance portal. It helps organizations identify and mitigate internal risks using machine learning, behavioral analytics, and integration with Microsoft 365 services. It offers a robust way to protect sensitive information from insider threats, both accidental and malicious.
Types of Insider Risks
- Malicious Insiders – Individuals who intentionally leak or misuse company data.
- Negligent Insiders – Employees who accidentally mishandle sensitive information.
- Compromised Insiders – Users whose credentials are stolen and exploited by attackers.
Key Benefits of Microsoft Insider Risk Management
✅ Automated Risk Detection – Uses AI to detect abnormal activities.
✅ Real-Time Alerts – Notifies admins of suspicious behavior immediately.
✅ Customizable Policies – Tailor-made for various industries and use cases.
✅ Integration with Microsoft 365 – Seamlessly connects with DLP, Defender, and Communication Compliance.
Key Features of Microsoft Insider Risk Management
1. Policy Templates
Choose from ready-to-use templates for common risk scenarios like data leaks or departing employees.
2. Risk Indicators
Detects abnormal activities like:
- Large file transfers
- Unusual login locations
- Suspicious external data sharing
3. AI-Driven Behavioral Analytics
Uses machine learning to track user activities and assign risk scores based on behavior patterns.
4. Automated Actions & Security Responses
- Restrict access
- Trigger security investigations
- Send alerts to security teams
Step-by-Step: How to Implement Microsoft Insider Risk Management
Step 1: Meet Prerequisites
Before setting up:
- Ensure users have Microsoft 365 E5 Compliance licenses.
- Turn on Audit Logging (Microsoft Purview > Audit > Start recording).
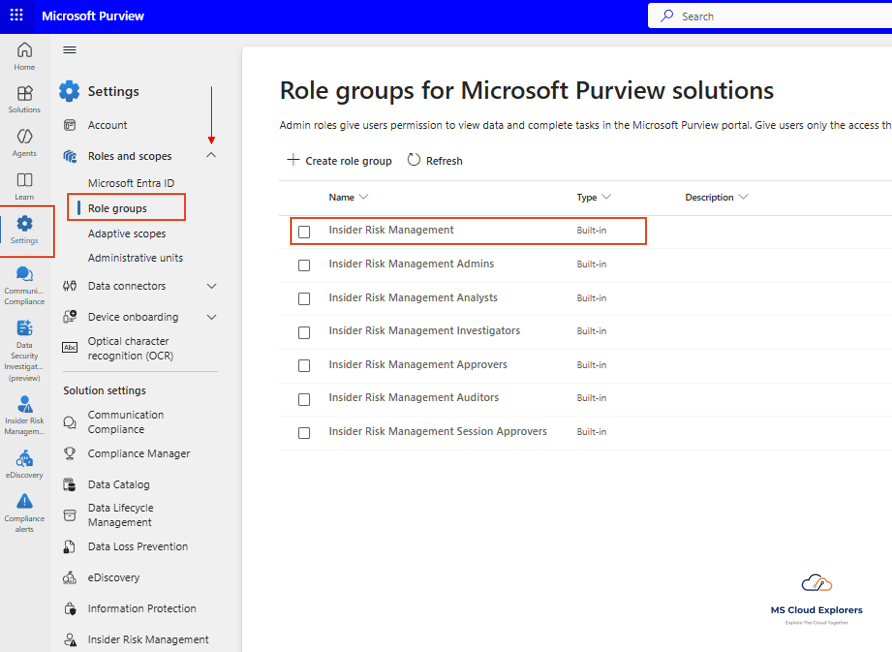
- Assign roles under Permissions in Microsoft Purview:
- Insider Risk Management
- Investigator
- Reviewer
- Analyst
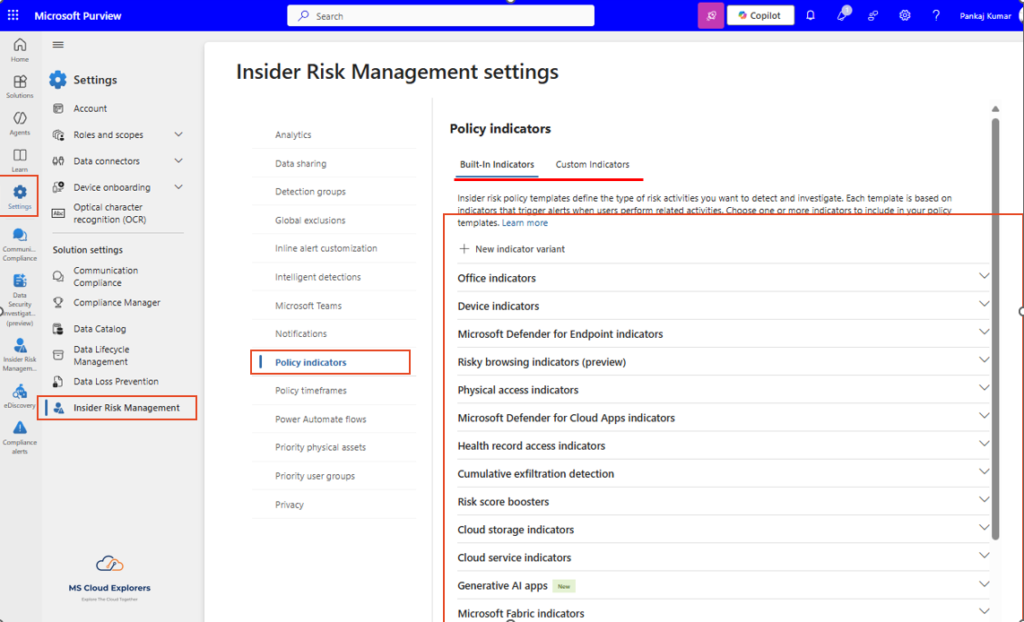
Step 2: Configure Risk Indicators
Navigate to Settings > Insider Risk Management > Policy Indicators.
Enable relevant indicators such as:
- Office indicators – Enable based on your organizational needs.
- Device indicators – Only available if your devices are onboarded to Microsoft Defender for Endpoint (MDE).
- Microsoft Defender for Endpoint indicators
You can enable all applicable indicators based on organizational requirements.
Optionally, create custom indicators for unique risk detection scenarios not covered by built-in options.
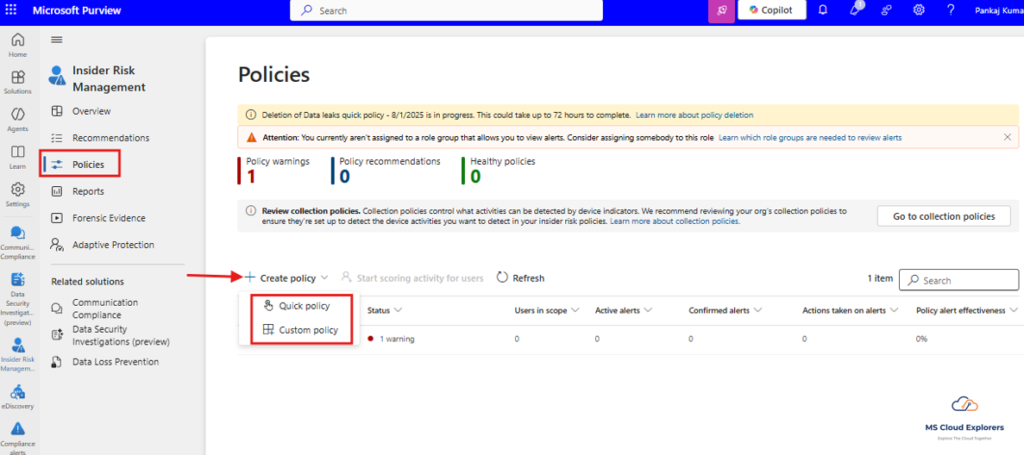
Step 3: Create a New Insider Risk Policy
- Under the Solutions > Click on Insider Risk Management
- Navigate to Policies > + Create policy
- Choose a policy template:
- Quick Policy – Create policies using built-in templates.
- Custom Policy – Build policies with advanced, custom settings.
Quick Policy Creation Steps:
- Select a template from Quick Policies, then click Get Started.
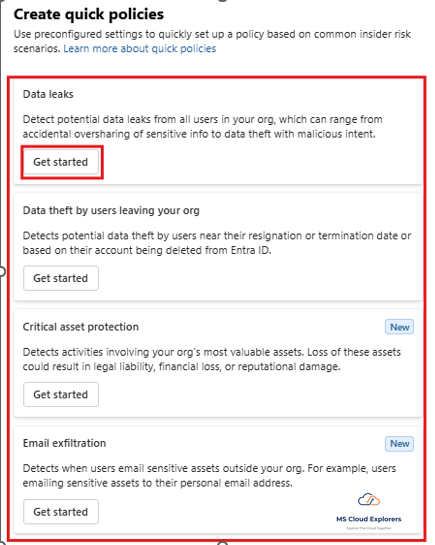
Custom Policy Creation Steps:
- Policy Template – Select a relevant template (e.g., Data Leaks).
- Name and Description – Enter a meaningful name and description.
- Admin Unit – Leave blank unless you use administrative units.
- Users and Groups – Select the users or groups to apply the policy to.
- Exclusions (Optional) – Exclude specific users or groups if needed. Best practice: use dynamic groups for flexibility.
- Content to Prioritize – Choose content prioritization or select I don’t want to prioritize content.
- Triggering Events – Add relevant DLP signals and indicators configured earlier. Note: The interface may vary if prioritized content is selected.
- Indicators – Add or refine policy indicators.
- Detection Options – Leave defaults unless you have specific requirements.
- Thresholds – Use Microsoft’s recommended thresholds.
- Review and Submit – Finalize and submit your policy.
After successful creation, you will see the new policy listed under IRM > Policies.
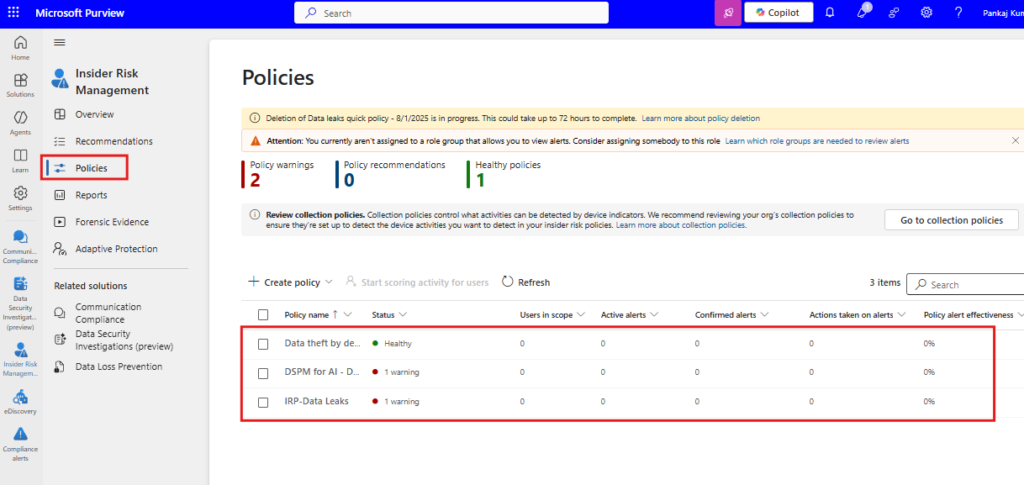
Detecting and Investigating Insider Threats
📈 Risk Score Analysis
Each user is assigned a risk score to prioritize investigations.
🧠 AI Behavioral Analytics
Machine learning identifies anomalies in file access, sharing, and communication.
🔐 Automated Security Actions
- Auto-revoke access
- Notify security team
- Trigger compliance workflow via Microsoft Purview
Best Practices for Using Microsoft Insider Risk Management
- Regularly review and update policies
- Train employees on safe data handling
- Limit access based on the principle of least privilege
- Integrate with Microsoft Defender, DLP, and Communication Compliance
Integration with Microsoft Purview Tools
Microsoft Insider Risk Management works seamlessly with:
- Data Loss Prevention (DLP) – Stop data from leaving the org
- Communication Compliance – Monitor Teams, emails, etc., for violations
- Information Protection – Classify and protect sensitive content
Case Studies: Real-World Applications
Example 1: A financial firm prevented a data breach after detecting an employee transferring sensitive customer data to personal email.
Example 2: A healthcare organization reduced internal fraud by monitoring user access to patient records.
Common Challenges & Solutions
False Positives
❌ Challenge: Too many alerts causing security fatigue.
✅ Solution: Fine-tune policies to reduce unnecessary warnings.
Privacy Concerns
❌ Challenge: Employees worried about excessive monitoring.
✅ Solution: Implement ethical monitoring policies that balance security with privacy.
Employee Resistance
❌ Challenge: Users reluctant to accept security measures.
✅ Solution: Educate employees on insider threats and security best practices.
Future of Insider Risk Management: AI & Automation
As AI advances, automated risk detection will become smarter, helping security teams respond faster and more accurately to insider threats.
FAQs
1. What is Microsoft Insider Risk Management?
A security solution within Microsoft Purview that detects, investigates, and mitigates insider threats using AI-driven analytics.
2. How does it detect insider threats?
By analyzing user behavior and detecting abnormal activity patterns using AI and risk indicators.
3. What Microsoft 365 license is required?
Requires Microsoft 365 E5 Compliance or an Insider Risk Management add-on.
4. Can it be integrated with other Microsoft security tools?
Yes, it integrates with DLP, Communication Compliance, and Information Protection.
5. How can organizations implement it effectively?
- Define clear policies
- Monitor security alerts regularly
- Train employees on best cybersecurity practices
Final Thoughts
Microsoft Insider Risk Management empowers organizations to proactively detect, investigate, and mitigate insider threats before they cause real damage. With AI-powered insights, automated responses, and deep integration into Microsoft 365, it is an essential tool in any modern cybersecurity strategy.
Explore More from MS Cloud Explorers: –
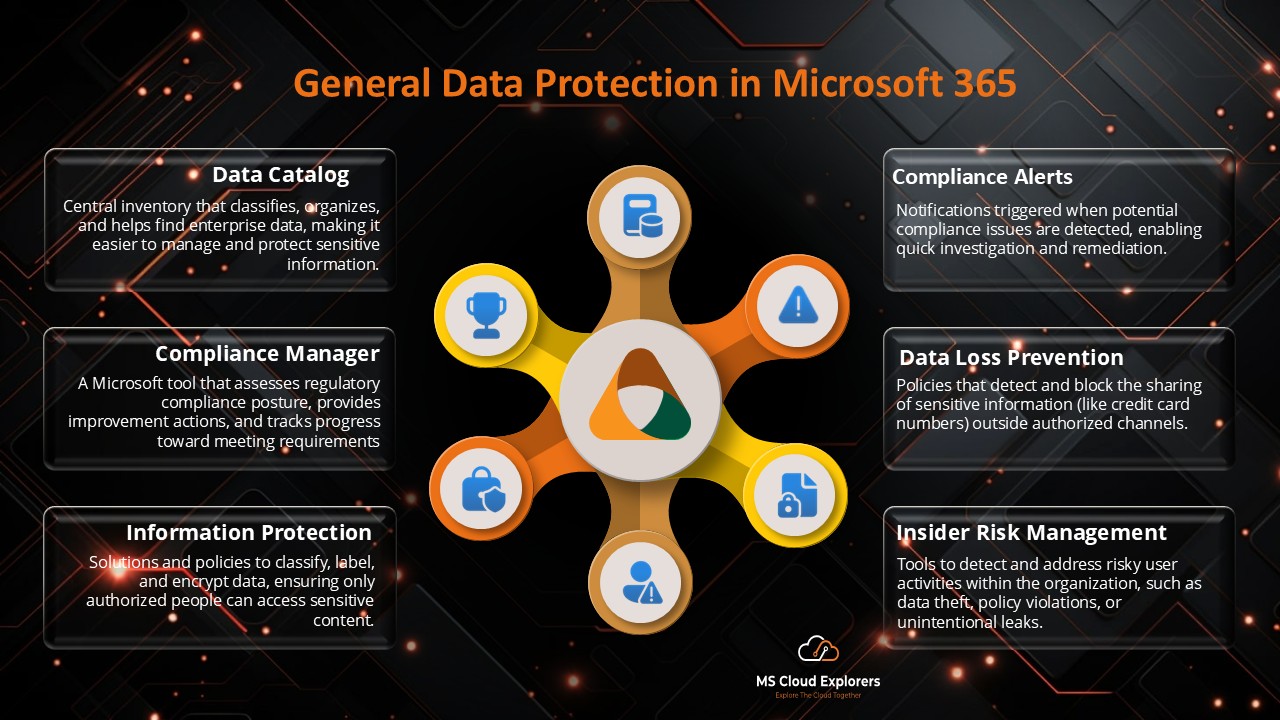
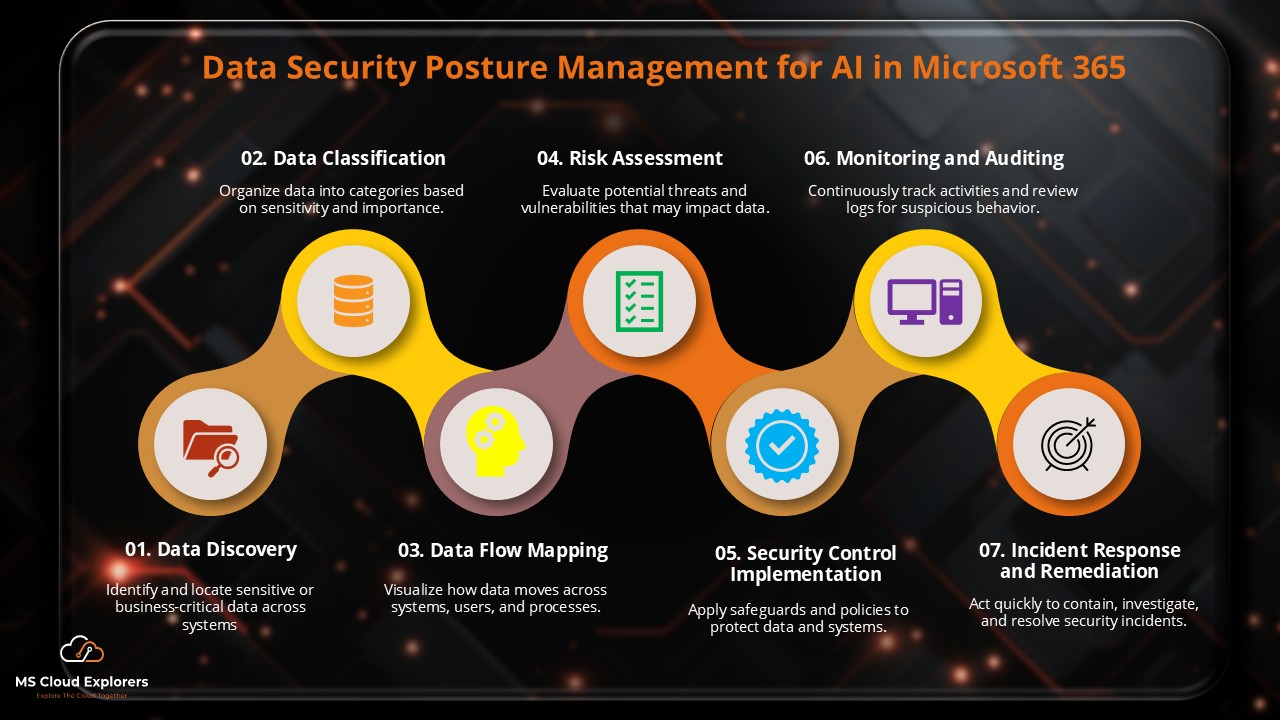
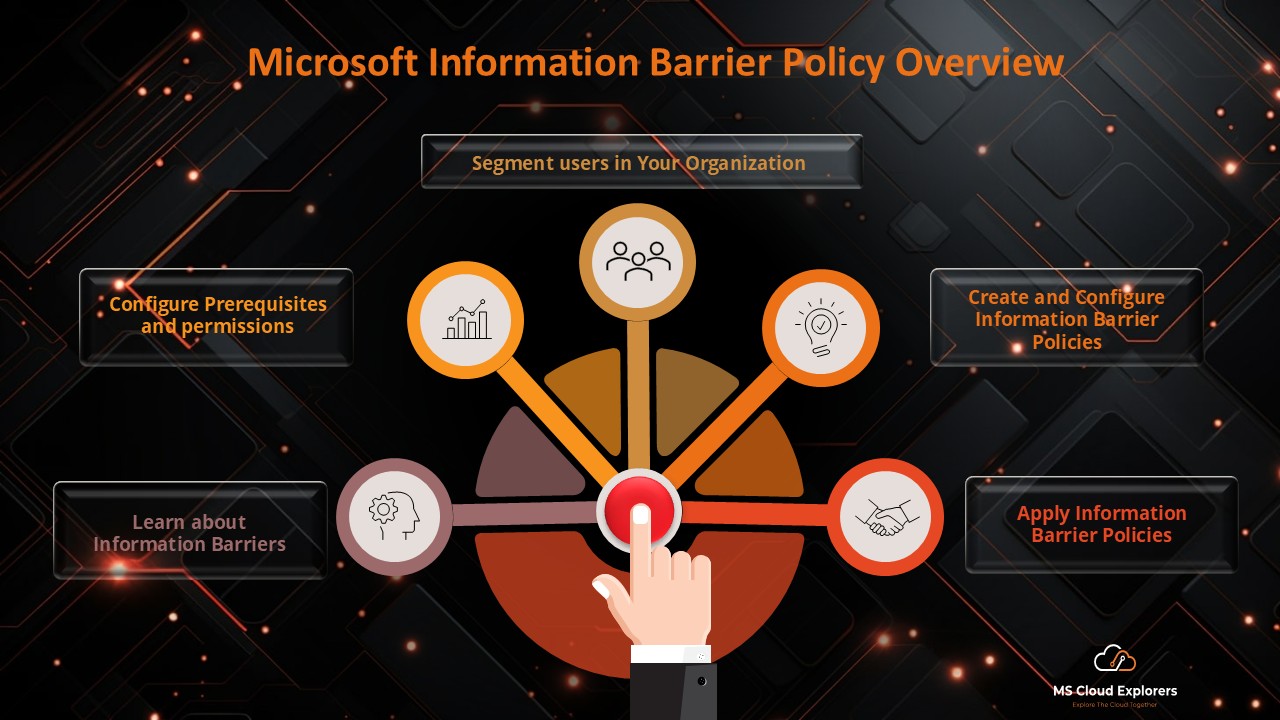
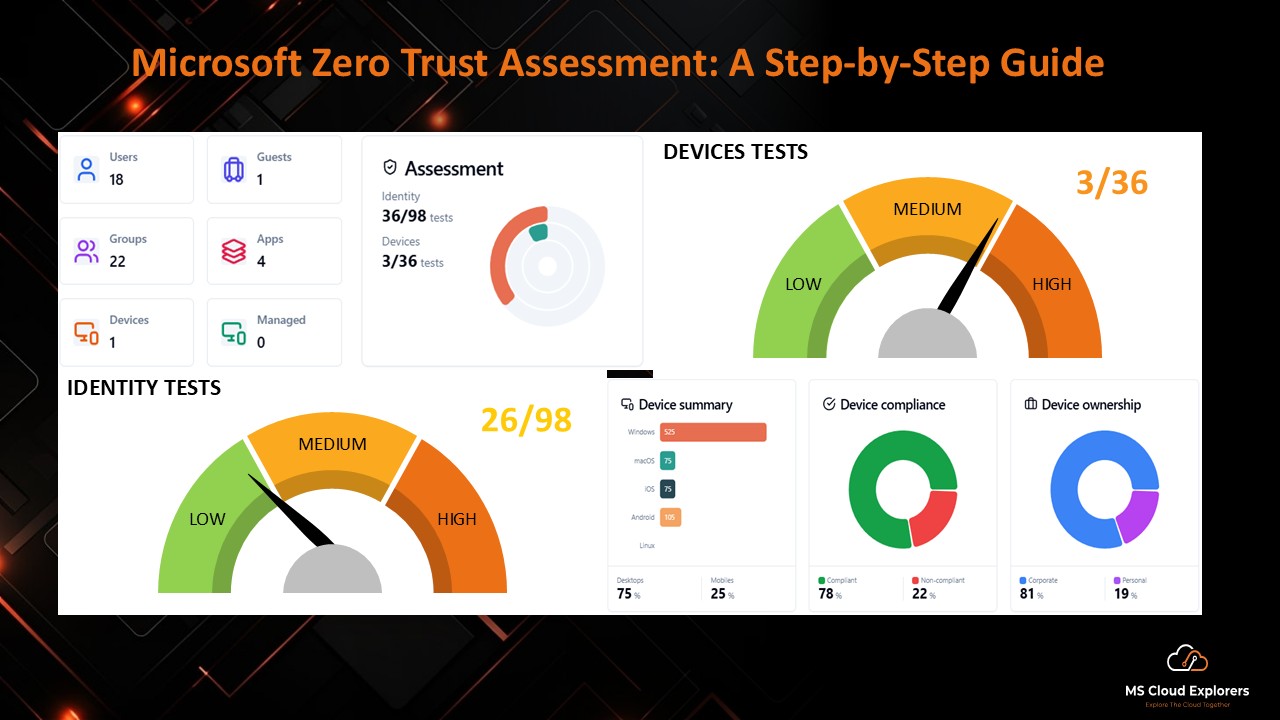
- General Data Protection in Microsoft 365: Ensuring Data Privacy and Security
- Secure Sensitive Documents in SharePoint Online Using IRM: A Step-by-Step Guide
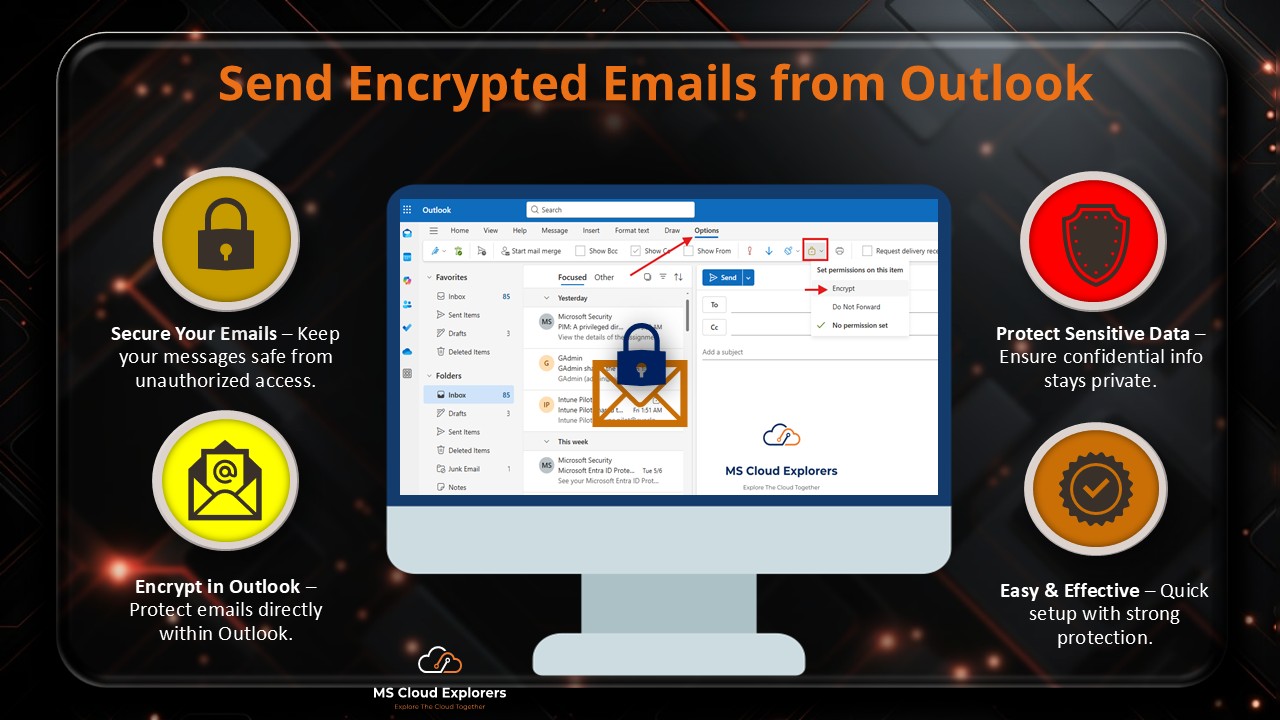
- How to Send Encrypted Email in Outlook: A Step-by-Step Guide for Beginners
- How to Setup Microsoft 365 Data Loss Prevention: A Complete step-by-step Guide
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!







Just enabled insider risk policies last week. The real‑time alerts are awesome, but we did need to refine indicators to avoid chatter overload. Highly recommend starting small!
Exactly—starting small is key. Begin with a pilot group, adjust policies based on initial feedback, and gradually expand. That phased approach really helps balance security and alert fatigue.
Is Insider Risk Management useful even if we already use audit logs and DLP policies? Just wondering if it adds anything new.
Great question! Yes, Insider Risk Management adds another layer by analyzing user behavior over time. Unlike audit logs and DLP, it uses signals like unusual activity patterns, risky user actions, and even resignation timelines to detect potential threats earlier. It’s definitely worth using alongside your current tools.
Great read! I didn’t realize Microsoft had such detailed tools for insider risk. Can this detect things like data being shared to personal emails?
Absolutely — glad you found it useful! Yes, Insider Risk Management can detect risky actions like sharing sensitive data to personal email accounts, uploading to cloud drives, or even unusual file access patterns. With the right policies and DLP integration, it becomes a powerful layer of protection. Let us know if you’d like help setting up those policies!