- November 16, 2025
- Pankaj Kumar
- 1
A few weeks ago, my manager assigned me the responsibility of deploying Microsoft Extended Security Updates (ESU) for one of our enterprise customers. Their Microsoft Intune environment included nearly 5,000 devices, and while most had already upgraded to Windows 11, around 400 production devices were still running Windows 10 due to dependencies on older line-of-business (LOB) applications.
Upgrading these devices wasn’t immediately possible, and manually deploying ESU to each system would have taken weeks. Since all devices were already enrolled in Intune, using it for automated ESU deployment became the most effective option.
I researched various community blogs and Microsoft documentation — some recommended PowerShell scripts, others suggested packaging ESU as a Win32 app. However, in this customer’s environment, none of those methods worked reliably. After multiple rounds of testing and troubleshooting, I created my own PowerShell script and deployed it directly through Intune.
This finally produced consistent, successful activation across all Windows 10 devices.
In this guide, I’ll walk you through everything I learned so you can deploy Microsoft Extended Security Updates smoothly in your environment.
What Are Microsoft Extended Security Updates (ESU)?
Microsoft Extended Security Updates is a paid program that provides critical and important security patches for Windows operating systems that have reached their End of Support (EOS).
This program gives organizations additional time to migrate while remaining secure — especially when:
- Line-of-business apps require Windows 10
- Hardware isn’t ready for upgrade
- Vendor certification for Windows 11 is still pending
Microsoft officially announced that Windows 10 support ends on 14 October 2025, which immediately raised concerns for organizations that depend on older systems.
To help bridge this gap between modernization and security, Microsoft introduced ESU — ensuring Windows 10 devices continue to receive essential security updates during the transition.
The Role of Microsoft Intune in ESU Deployment
Intune turned out to be the most reliable, scalable, and automated approach for deploying Microsoft Extended Security Updates.
Using Intune, you can:
- Distribute ESU activation scripts
- Monitor compliance and license status
- Track update installation
- Automatically deploy changes without device touch
Instead of logging into each device or running local scripts, Intune handles ESU activation remotely with full visibility.
Deploying Microsoft Extended Security Updates Using Intune
Here’s the exact process that worked for me:
1. Purchase and Verify ESU Licenses
Buy ESU licenses through:
- Volume Licensing
Confirm they are successfully assigned to the tenant.
2. Ensure All Devices Are Synced With Intune
Verify that all Windows 10 devices are:
- Enrolled
- Reporting to Intune
- Healthy (no MDM issues)
3. Deploy the ESU PowerShell Script with Intune
Push your ESU activation script via:
Login to the Intune Admin Center.
In the left navigation pane, select Devices.
Under Manage Devices, click Scripts and Remediations.
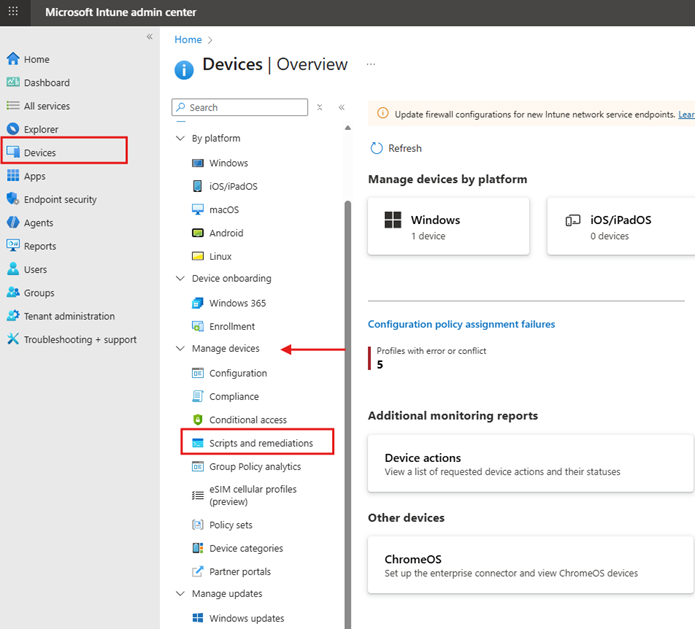
If you have Microsoft 365 E5 or add-on licenses, you can use Remediations for detection and remediation scripts.
Since our customer did not have Remediation support, we used the Platform Scripts option instead.
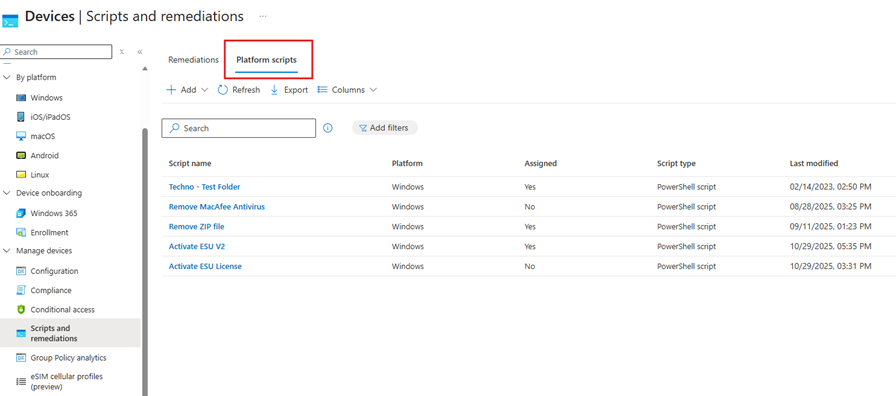
- Click Add and select Windows 10 and later.
- Provide a Name and Description for the script profile.
Before uploading your script to Intune, prepare it using the code below:
4. Windows 10 ESU Activation Script (PowerShell)
# =============================
# Windows 10 ESU Activation Script
# =============================
# Enter your ESU key
$ESUKey = "9QBXX-00xx-XXXX-0000-3GTR8" # Replace with your real key
Write-Host "Installing Windows 10 ESU Key..."
slmgr /ipk $ESUKey
Start-Sleep -Seconds 5
Write-Host "Activating ESU Key..."
slmgr /ato
Start-Sleep -Seconds 10
# Verify activation
$ESU = Get-CimInstance SoftwareLicensingProduct | Where-Object { $_.Name -like "*Extended Security Updates*" -and $_.LicenseStatus -eq 1 }
if ($ESU) {
Write-Host "ESU successfully activated."
exit 0
} else {
Write-Host "ESU activation failed."
exit 1
}
Configure the remaining options according to your environment or choose the similar below.
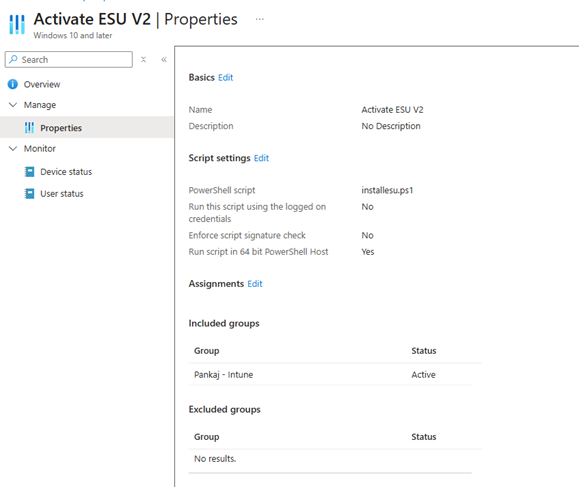
Assign the script to the appropriate Azure AD group.
You can create a Azure AD Dynamic device group for Windows 10 devices using the following rule:
(device.deviceOSType -eq "Windows") -and (device.deviceOSVersion -startsWith "10")This ensures that only Windows 10 devices receive the ESU activation script.
Verify Windows 10 ESU Activation
1. Windows PowerShell
- You can verify ESU activation on a device using one of the following methods:
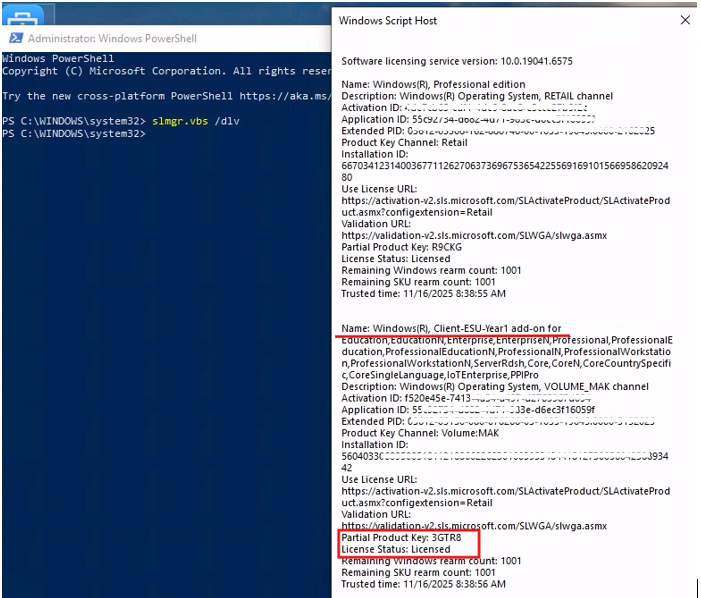
- Open PowerShell on the Windows 10 device and run the following command:
slmgr /dlvThis will display detailed licensing information, including the ESU activation status.
2. Windows Settings
You can also confirm activation by navigating to: Settings → Update & Security → Activation
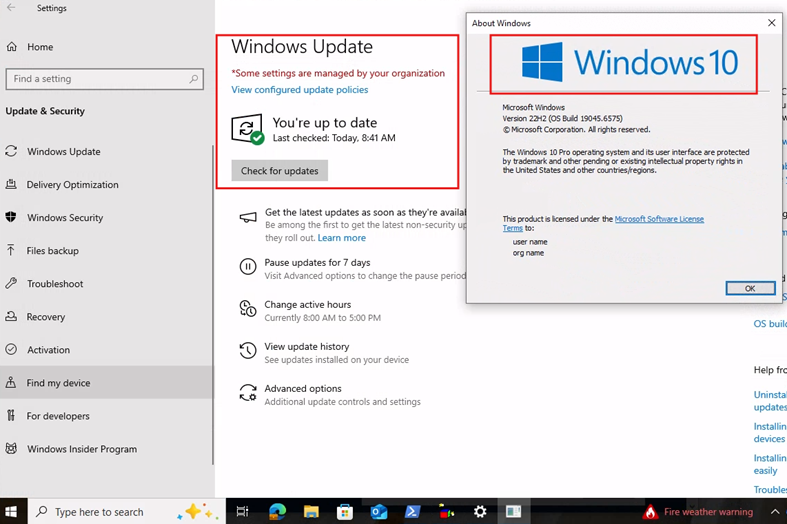
If the ESU key is applied correctly, the device will show activation details under the licensing section.
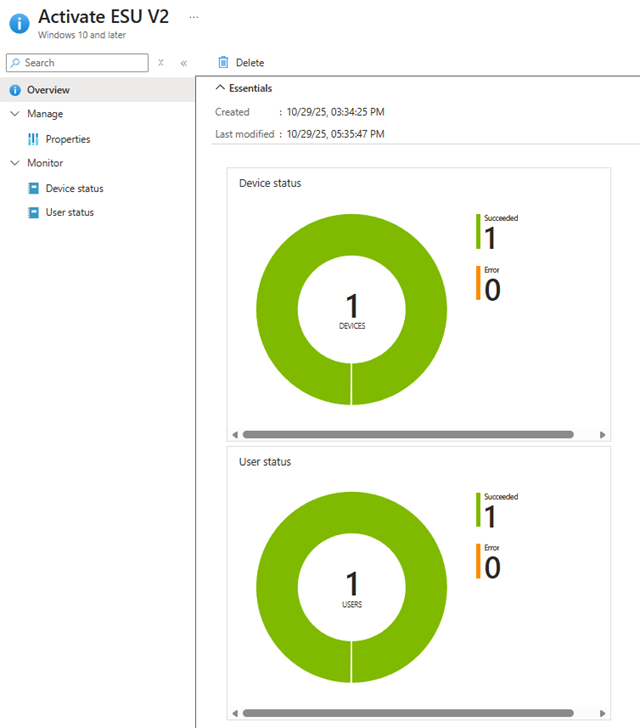
3. Intune Reports
Intune provides centralized reporting where you can track ESU activation status for all targeted devices.
Go to: Intune Admin Center → Devices → Script → Overview
Once everything is configured and you’ve verified that the script works correctly on a test device, you can safely roll it out to all remaining Windows 10 devices in your environment.
Licensing & Activation Options for ESU
Microsoft offers two activation paths:
1. Volume Licensing (VL)
Ideal for large enterprises needing centralized key management.
2. Cloud-Based Activation
Best for Azure AD–joined cloud-first organizations.
Once activated, devices automatically download ESU security updates during normal update cycles.
When Should You Use Microsoft Extended Security Updates?
ESU is typically needed when:
- Applications or hardware are not compatible with newer OS versions
- Vendors require time to certify their software for Windows 11
- You maintain secure remote or air-gapped systems
- Migration planning requires additional time
In my customer’s case, multiple critical business applications were still incompatible with Windows 11, forcing them to stay on Windows 10 for a few more months.
Industry Use Cases for ESU
Common industries relying on Microsoft Extended Security Updates include:
- Healthcare – Imaging, diagnostic, and certified medical devices
- Manufacturing – Systems tied to older firmware or automation
- Government – Long-term compliance requirements
- Finance – Core systems running on older OS versions
Cost and Subscription Options for ESU
Microsoft uses a year-by-year pricing model, with prices increasing each year:
- Year 1: $61 USD per device
- Year 2: $122 USD per device (cost doubles from Year 1)
- Year 3: $244 USD per device (cost doubles from Year 2)
This model encourages organizations to migrate sooner, while still providing a secure transition period.
💼 Need ESU licensing or deployment support?
If your organization is looking for ESU consulting, deployment assistance, or discounted license pricing — reach out to us. We can help you plan, deploy, and manage ESU end-to-end.
Security and Compliance Benefits
With Microsoft Extended Security Updates, organizations continue receiving:
- Critical security fixes
- Important patches
- Protection from active vulnerabilities
These updates are essential for organizations that must maintain compliance (ISO 27001, HIPAA, PCI-DSS) even after Windows 10’s EOS.
Transitioning from ESU to a Modern Platform
ESU is a temporary bridge — not the endpoint.
Use your ESU window to plan a migration to:
- Windows 11
- Azure Virtual Desktop (AVD)
- Windows 365 Cloud PCs
Tools like Intune Endpoint Analytics and Windows 11 readiness reports make this process much easier.
ESU Eligibility for Windows 365 Devices
Windows 10 devices accessing:
- Windows 365 Enterprise Cloud PCs
- Windows 365 Frontline (Dedicated) Cloud PCs
are automatically eligible for Microsoft Extended Security Updates, provided all licensing requirements are met.
The best part? All ESU updates can be managed directly from Intune, offering full control and visibility.
Common Challenges and How to Fix Them
1. ESU Activation Fails
Check that the ESU key matches the edition (Enterprise / Education).
2. Script Deployment Issues
Always test with a pilot group before broad rollout.
3. Reporting Errors
Connect Intune with Log Analytics for better reporting.
4. False End-of-Support Notifications
Microsoft has acknowledged a known issue where some ESU-enabled devices still show “End of Support.”
These devices continue to receive ESU updates without any problem.
Best Practices for Managing ESU with Intune
- Maintain a device inventory including ESU status
- Use Intune compliance policies to track update coverage
- Automate notifications before ESU expiration
- Document each step for auditing and governance
- Regularly monitor devices through Intune + Update Compliance
Conclusion
The Microsoft Extended Security Updates program is essential for organizations still relying on Windows 10. My experience — from failed attempts to a fully automated Intune deployment — shows that success relies on automation, testing, and accurate reporting.
When you combine ESU with the power of Microsoft Intune, deployment becomes predictable, scalable, and efficient.
If you’re planning an ESU rollout, this guide will help you get started with confidence — and Intune will handle the heavy lifting once things are configured correctly.
FAQs
- How long does ESU last?
Up to 3 years after Windows 10’s EOS date. - Can ESU be deployed using Intune only?
Yes — Intune fully supports ESU deployment via scripts or Win32 apps. - Is ESU available for Windows 10 after 2025?
Yes, Microsoft provides ESU for Enterprise and Education editions. - Do ESU updates include new features?
No — ESU provides only security updates. - What happens when ESU expires?
Devices will stop receiving security patches, increasing risk exposure.
Explore More From MS Cloud Explorers
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!
1 comment on “How to Deploy Microsoft Extended Security Updates (ESU) Using Intune: Step-by-Step Guide”