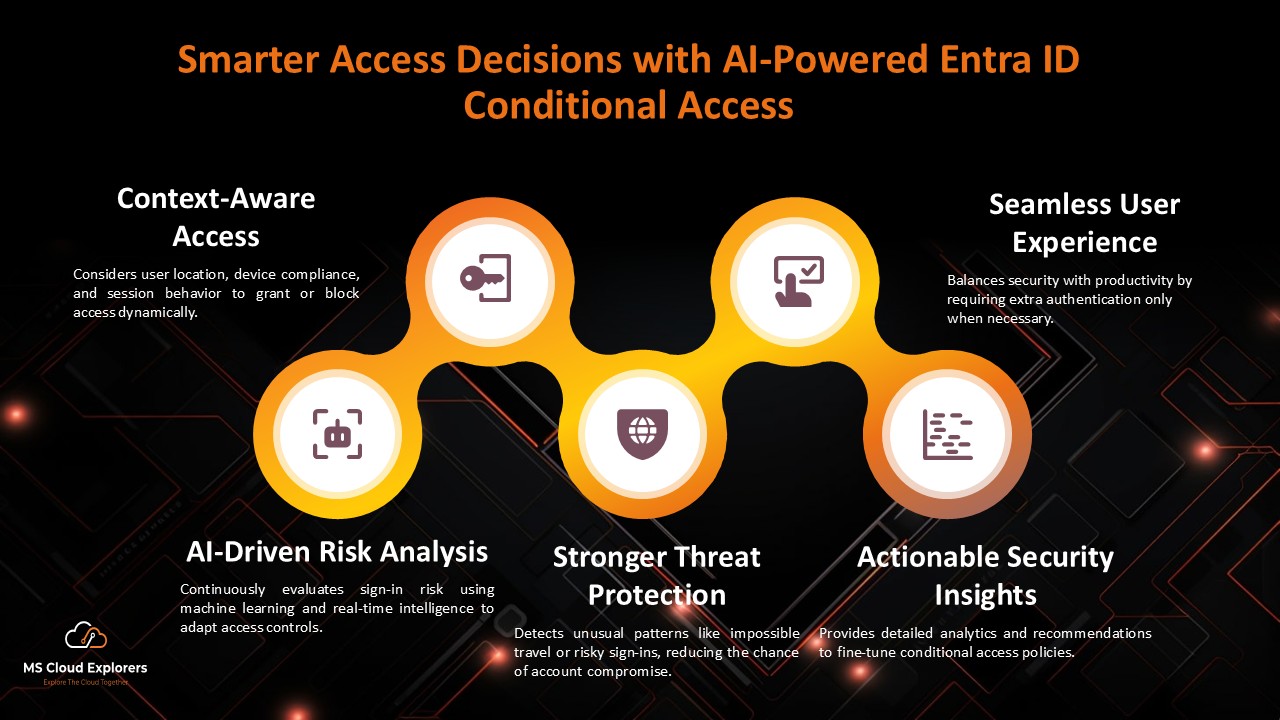
Artificial Intelligence (AI) isn’t just about robots and chatbots—it’s revolutionizing identity security. As hybrid work and cloud adoption accelerate, traditional access controls are no longer sufficient. Enter Artificial Intelligence in Entra ID Conditional Access—a game-changer that enables smarter, real-time decisions to protect identities and data.
What Is Entra ID Conditional Access?
Conditional Access in Microsoft Entra ID (formerly Azure AD) is a policy-based engine that governs how users access cloud apps. Based on user conditions like location, device compliance, or group membership, access can be allowed, blocked, or require MFA.
Think of it as the “if-then” rulebook for identity security.
Why Conditional Access Alone Isn’t Enough
Static rules can’t always detect dynamic threats like compromised credentials or unusual logins. With cyber attackers evolving tactics, there’s a growing need for intelligence that adapts in real time.
What Role Does Artificial Intelligence Play?
AI brings a layer of machine learning and behavioral analysis that helps determine:
- Is this user behavior normal?
- Is this login location risky?
- Is this device secure?
- Has this account shown signs of compromise?
AI answers these questions on the fly.
How AI Elevates Entra ID Conditional Access
1. Risk-Based Access Decisions
AI calculates risk scores for both users and sign-ins. These scores feed into Conditional Access policies to allow or block access dynamically.
2. Real-Time Threat Detection
AI detects anomalies instantly, such as:
- Impossible travel
- Malware-injected sessions
- Token theft
3. Behavioral Analytics
Patterns like unusual sign-in times or locations are flagged, even if traditional policies wouldn’t catch them.
AI Capabilities Integrated into Entra ID
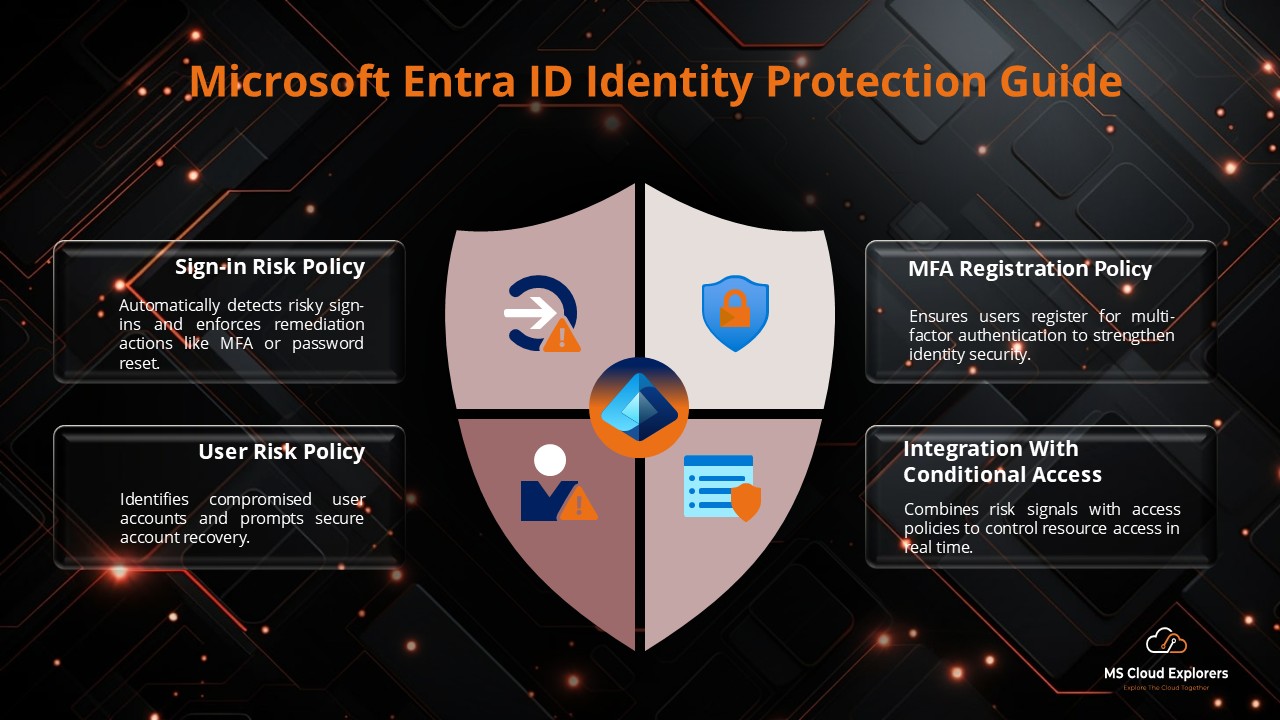
Microsoft Identity Protection
Leverages AI to detect:
- Atypical travel
- Anonymous IP addresses
- Bot traffic
Sign-in Risk & User Risk Detection
Each sign-in or user profile is assigned a risk level: low, medium, or high.
Adaptive Policy Enforcement
If risk is high, force MFA. If medium, allow limited access. If low, proceed normally. This dynamic control improves both security and user experience.
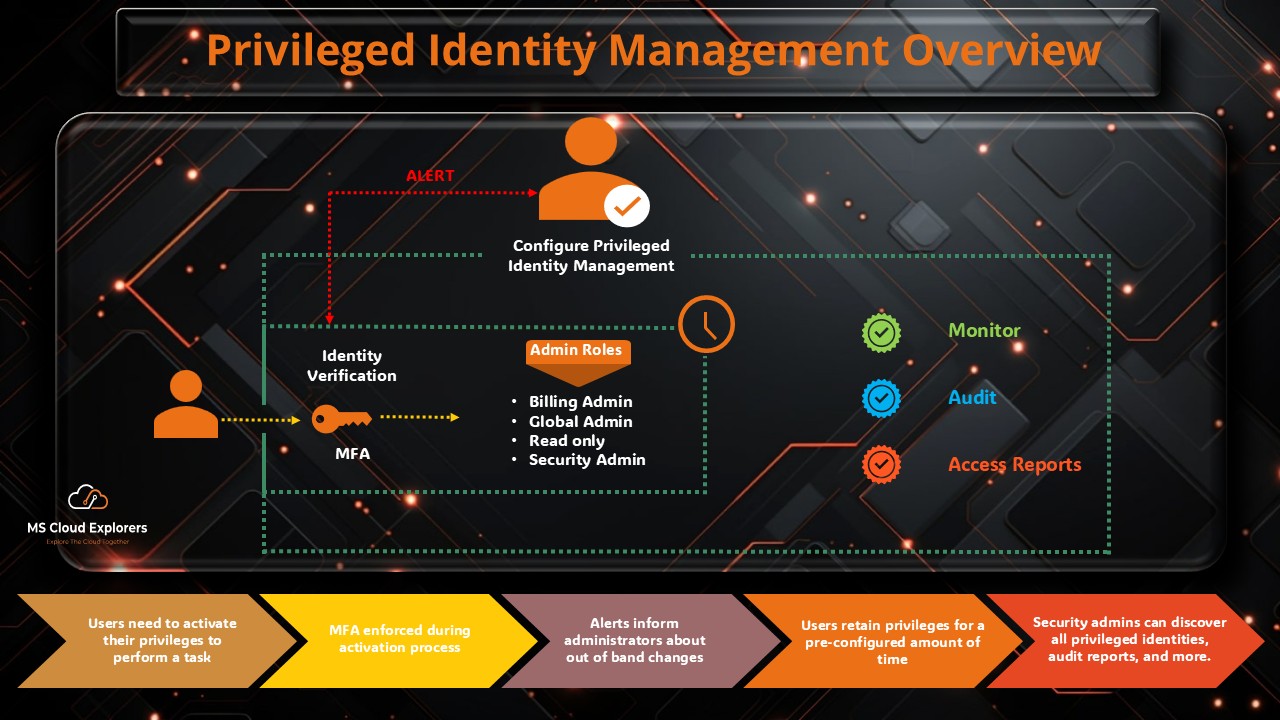
Implementation Steps
Step 1: Enable Microsoft Entra ID Premium P2
Identity Protection is only available in the P2 license tier.
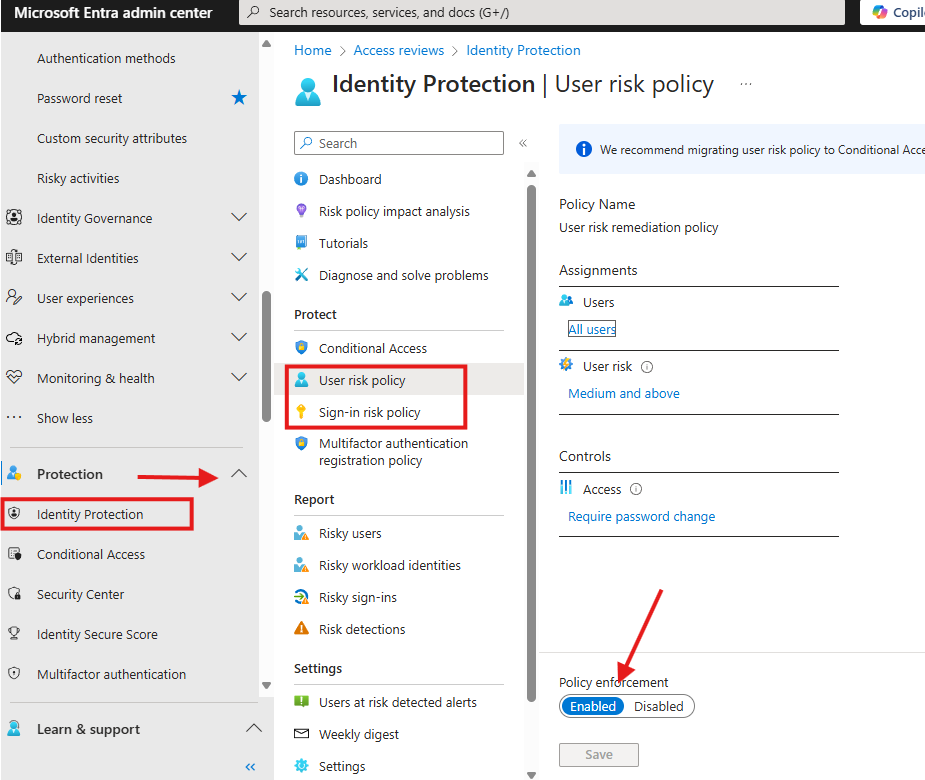
Step 2: Turn On Identity Protection
Go to Entra Admin Center > Protection > Identity Protection and enable sign-in risk and user risk policies.
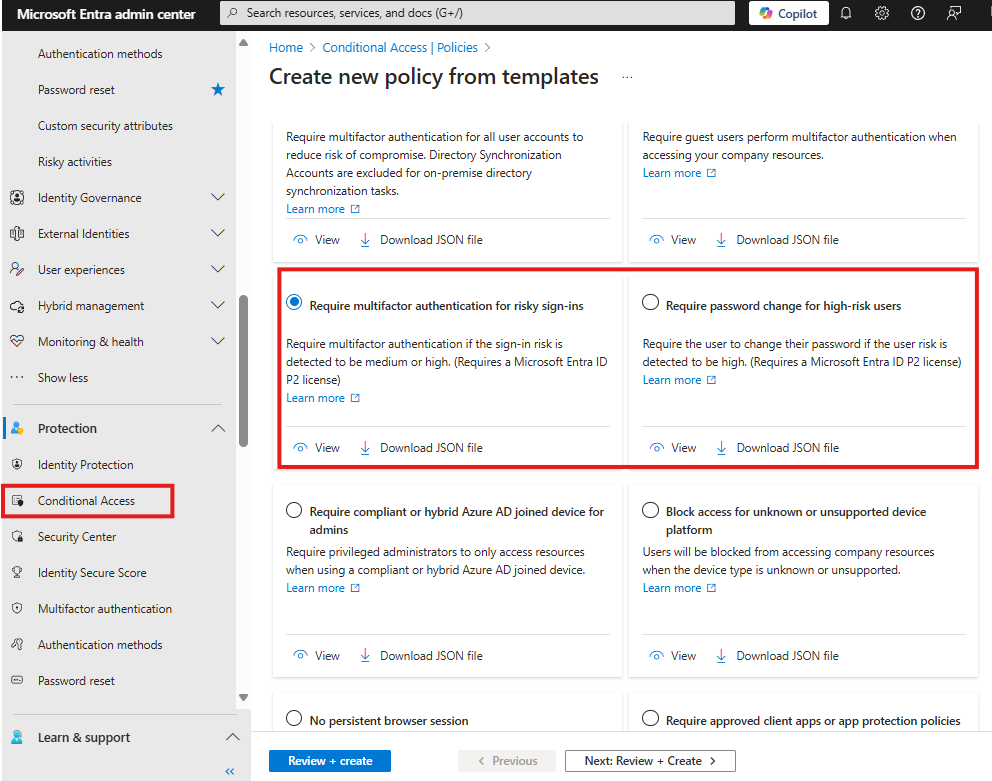
Step 3: Create Conditional Access Policies with Risk Signals
Navigate to:
- Entra Admin Center > Conditional Access
- Create a policy or Create from Templates
- Assign users
- Target cloud apps
- Use conditions like “Sign-in Risk = Medium or Above”
- Grant: Require MFA or Block access
Step 4: Test and Monitor Using Sign-In Logs
Review sign-in logs to understand how policies are behaving.
Step 5: Automate Remediation with Access Reviews
Use Entra’s Access Reviews and Entitlement Management to manage ongoing access intelligently.
Benefits of Using AI in Conditional Access
- Reduced false positives
- Improved detection of credential theft
- Lowered administrative overhead
- Real-time risk management
- Better user experience
Use Cases for AI-Powered Conditional Access
| Use Case | Description |
| Compromised Accounts | Automatically block users with high sign-in risk. |
| Traveling Users | Detect impossible travel and challenge with MFA. |
| Risky Locations | Detect and block logins from anonymizing VPNs. |
| Behavioral Deviations | Flag unusual working hours or location shifts. |
Common Challenges and How to Overcome Them
| Challenge | Solution |
| Policy Misconfiguration | Use templates and test in report-only mode first. |
| End-User Frustration | Explain the purpose of risk-based MFA or access blocks. |
| Data Noise | Rely on Microsoft Defender & Sentinel integrations. |
Security Best Practices with AI in Entra
- Don’t over-rely on a single condition.
- Use MFA + Sign-in Risk + Device Compliance together.
- Regularly review your Conditional Access logs.
- Combine with Defender for Identity for deep insights.
Monitoring & Reporting with AI
Use:
- Workbooks in Microsoft Sentinel
- Identity Protection Reports
- Log Analytics To visualize policy impact, user behavior, and risks in real-time dashboards.
Integration with Microsoft Defender and Sentinel
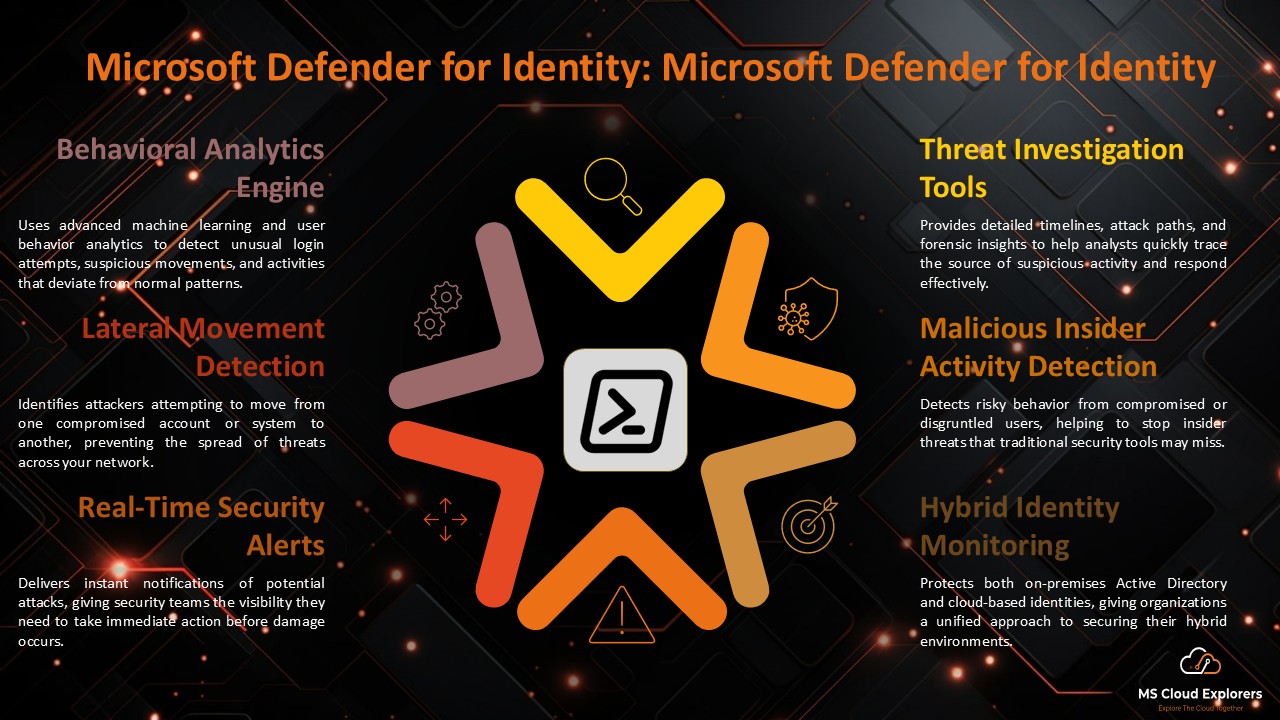
Microsoft Defender for Identity and Sentinel extend AI’s reach:
- Detect lateral movement
- Analyze user behavior
- Correlate risk signals across services
This provides a 360-degree view of identity threats.
Future Outlook: AI and Zero Trust in Identity
AI is at the center of the Zero Trust model. Identity is the new perimeter, and real-time decisions driven by AI will become the new standard for security.
Expect features like:
- Proactive blocking before sign-in
- Cross-platform behavioral correlation
- AI-generated policy recommendations
Conclusion
Artificial Intelligence in Entra ID Conditional Access transforms how we secure identities. It doesn’t just respond to threats—it anticipates them. With dynamic, data-driven access control, organizations can stay ahead of attackers while improving usability for legitimate users.
FAQs
1. What is AI in Microsoft Entra Conditional Access?
AI enhances Entra Conditional Access by detecting risks in real time and enforcing dynamic policies based on user behavior, location, and sign-in history.
2. How does Entra ID use machine learning?
Machine learning analyzes millions of signals to calculate risk levels for each user or sign-in event, influencing access decisions.
3. Do I need Entra ID P2 for AI features?
Yes, advanced AI capabilities like Identity Protection and risk-based policies require the Microsoft Entra ID Premium P2 license.
4. Can AI reduce false positives in Conditional Access?
Absolutely. AI uses behavioral baselines and context to differentiate real threats from normal deviations.
5. How do I monitor AI-driven access decisions? You can monitor through Entra’s sign-in logs, Identity Protection reports, and custom dashboards in Microsoft Sentinel.
Explore More from MS Cloud Explorers
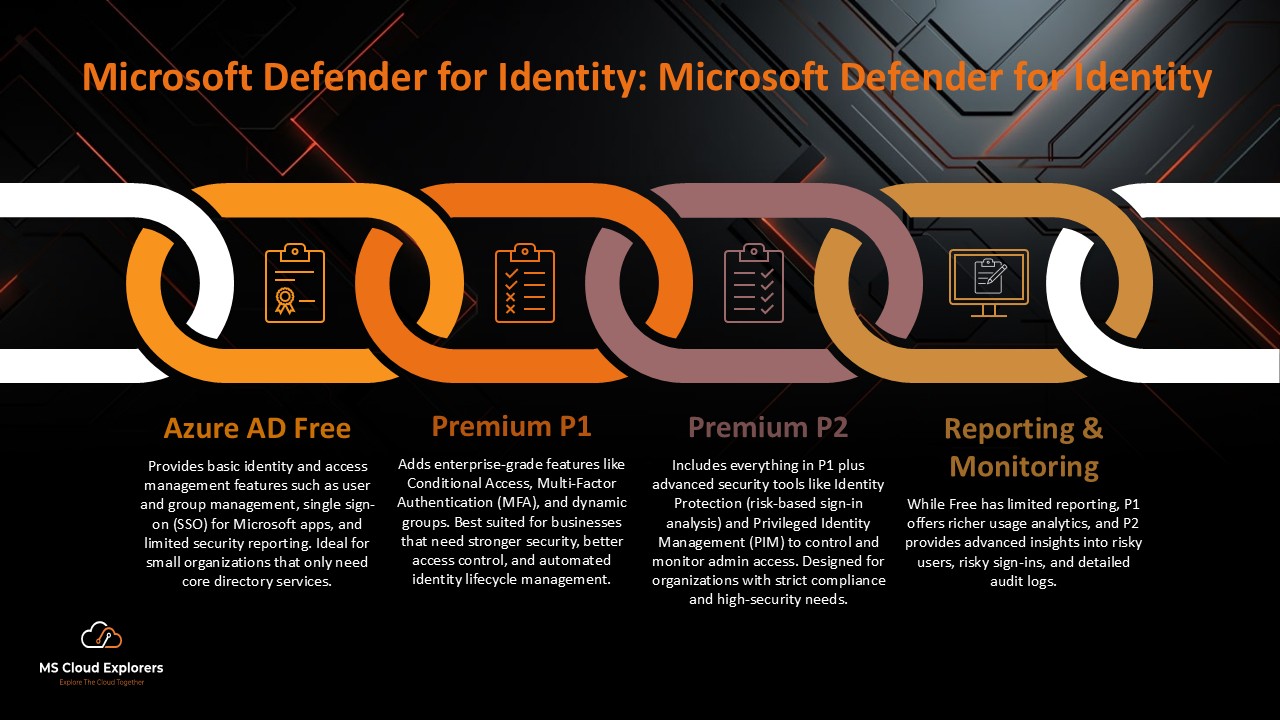
- Azure AD Free vs. Premium P1 & P2: Which Edition Is Right for Your Business?
- Microsoft Entra ID Identity Protection: A Complete Guide to Securing Your Environment
- Top 7 Conditional Access Policies Every Organization Should Implement
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!

Solid overview of using AI controls in Entra ID Conditional Access! The step-by-step setup for AI-based access policies is clear and actionable. It’d be helpful to see a quick comparison with traditional Conditional Access rules to highlight when AI control adds value. Thanks for sharing
Thanks for the feedback—I’m glad you found the AI controls guide helpful! That’s a great idea. I’ll add a section comparing AI-powered policies with standard Conditional Access rules to clarify their distinct benefits. Appreciate your suggestion!