- January 9, 2026
- Pankaj Kumar
- 4
Privileged Identity Management (PIM) has never been more essential—and a recent security assessment for one of our customers made that clearer than ever. During the review, I noticed something that immediately raised a red flag: the tenant had 9 Global Administrators assigned.
Out of curiosity, I asked the IT team why so many users needed Global Admin access. Their response was honest—and familiar:
“We assigned Global Admin access because certain tasks couldn’t be completed with the existing role. Once the work was done, we simply forgot to remove it.”
This scenario is far more common than most organizations realize. While it often starts with good intentions, permanent privileged access quickly becomes a serious security risk. Microsoft recommends keeping the number of Global Administrators to a minimum—ideally fewer than five—to reduce your attack surface.
Leaving standing privileged access in place increases the blast radius of an account compromise and often creates compliance gaps.
The good news? Strong security doesn’t have to slow down productivity.
That’s exactly where Privileged Identity Management (PIM) comes in.
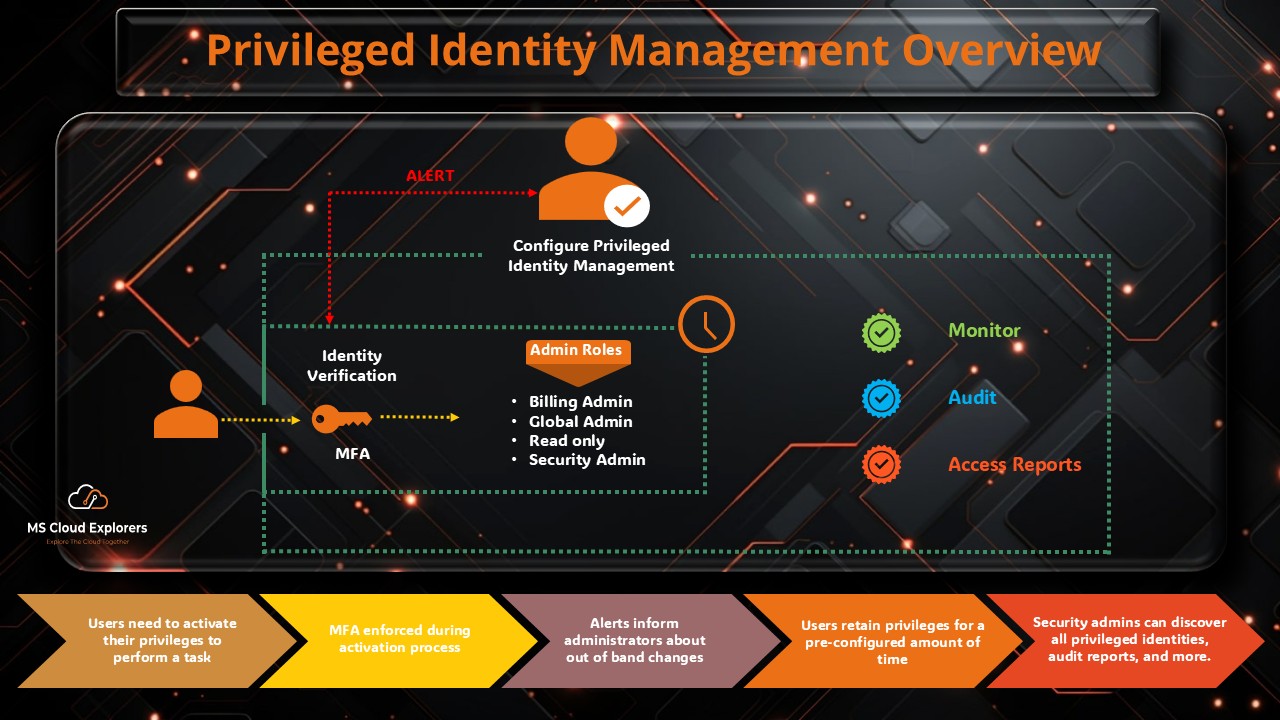
What Is Privileged Identity Management?
Privileged Identity Management (PIM) is a feature of Microsoft Entra ID designed to help organizations enforce the principle of least privilege.
In simple terms, Privileged Identity Management ensures users receive elevated permissions only when they need them—and only for a limited time. This significantly reduces the risks associated with always-on administrative access.
Why Privileged Identity Management Matters
In today’s digital workplace, privileged accounts are a primary target for attackers. Whether the threat is internal or external, unmanaged admin access can lead to:
- Data breaches
- Configuration drift
- Compliance violations
- Lateral movement across the tenant
Privileged Identity Management helps organizations control, monitor, and audit all privileged access in a centralized and secure way.
Key Features of Privileged Identity Management
- Just-in-Time (JIT) Access
Activate privileged roles only when required, reducing exposure windows. - Time-Bound Role Assignments
Define start and end times for access—ideal for projects or temporary work. - Approval-Based Role Activation
Require authorization before high-privilege roles are activated. - Multi-Factor Authentication (MFA)
Enforce MFA during role activation to verify user identity. - Access Reviews
Periodically review role assignments and remove unnecessary access. - Detailed Audit Logs
Track all role activations and changes for compliance and investigation.
License Requirements for Privileged Identity Management
Microsoft Entra ID P1 vs. P2
| Feature | Entra ID P1 | Entra ID P2 |
| Conditional Access | ✅ | ✅ |
| Multi-Factor Authentication | ✅ | ✅ |
| Identity Protection | ❌ | ✅ |
| Privileged Identity Management | ❌ | ✅ |
| Access Reviews | ❌ | ✅ |
| Just-in-Time Access | ❌ | ✅ |
To use Privileged Identity Management, you need Microsoft Entra ID P2.
Pro tip: You do not need to assign the P2 license to every user in the tenant—only to administrators who will use or manage PIM.
Privileged Identity Management Best Practices
- Always require MFA for role activation
- Use Conditional Access policies for additional protection
- Prefer Eligible assignments over permanent roles
- Run regular access reviews
- Monitor audit logs for suspicious activity
- Align activation duration with actual task requirements
Benefits of Implementing Privileged Identity Management
- Improved Security Posture – Reduced risk of credential misuse
- Regulatory Compliance – Supports PCI-DSS, HIPAA, SOX, and more
- Operational Efficiency – Automated approvals and removals
- Consistent Governance – Centralized control of privileged access
Step-by-Step: Configure Privileged Identity Management
Step 1: Enable PIM
- Sign in to the Azure portal or the Entra ID Portal.
- Search for Privileged Identity Management
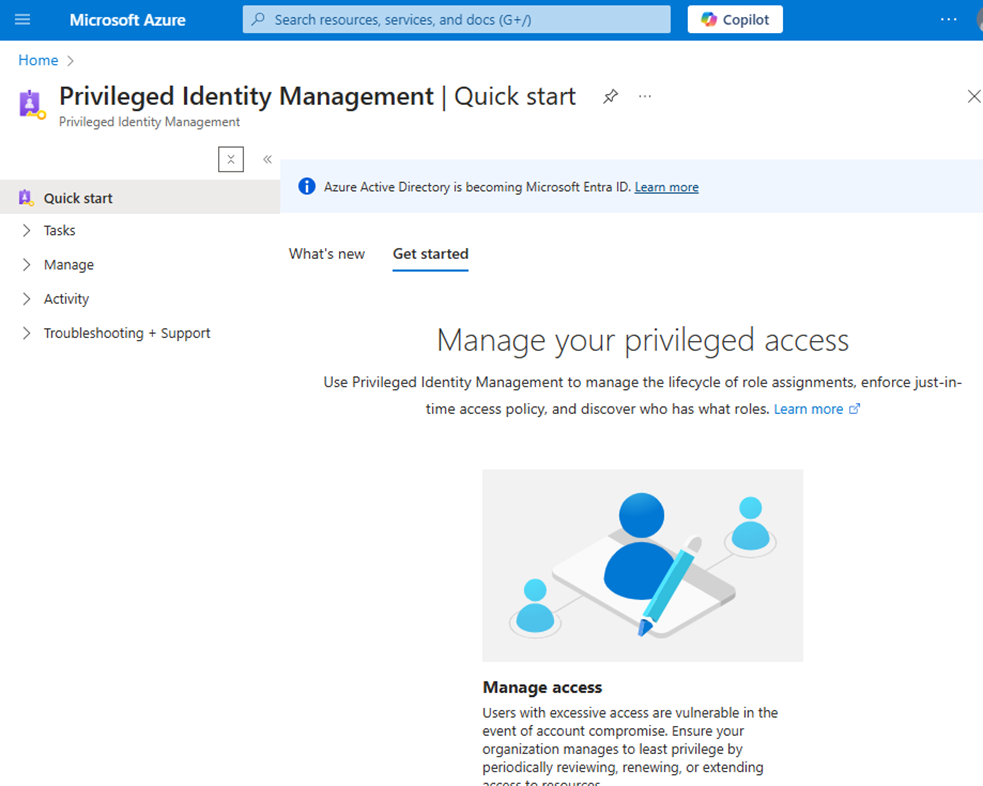
- Onboard your directory or subscription by following the prompts
Step 2: Assign Roles
- Go to PIM > Manage > Roles
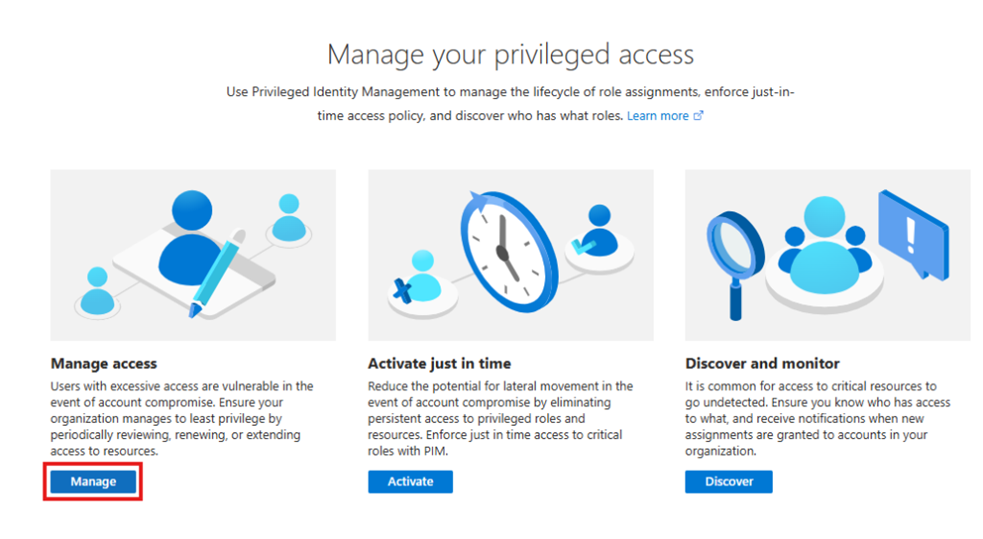
- Select the role you want to manage and click Add assignments.
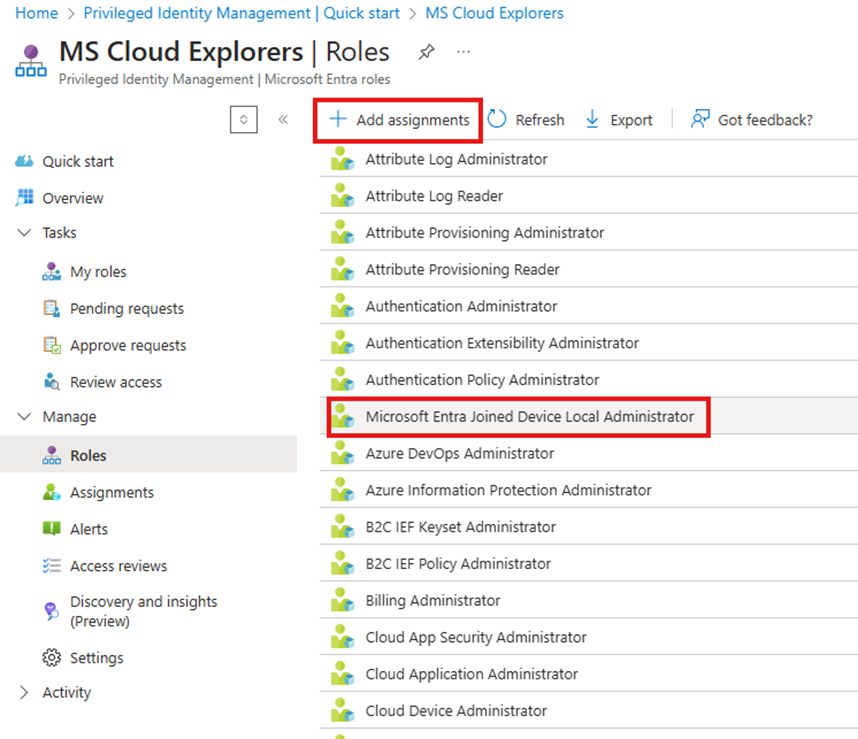
- Then Again Click on the + Add Assignments.
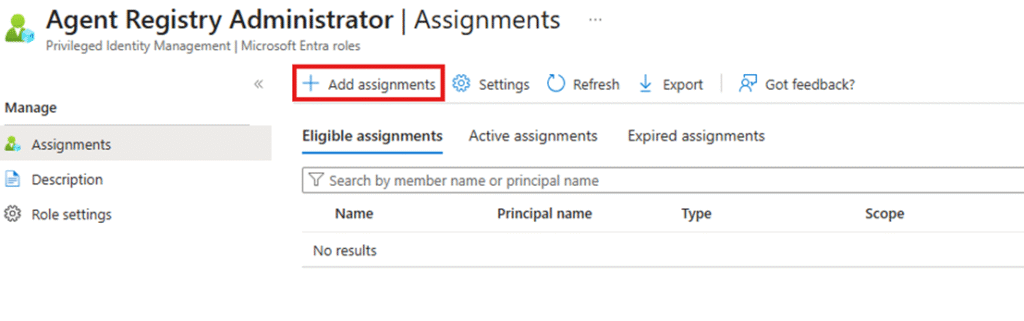
- Select the user or Group that you want to assign the Role.
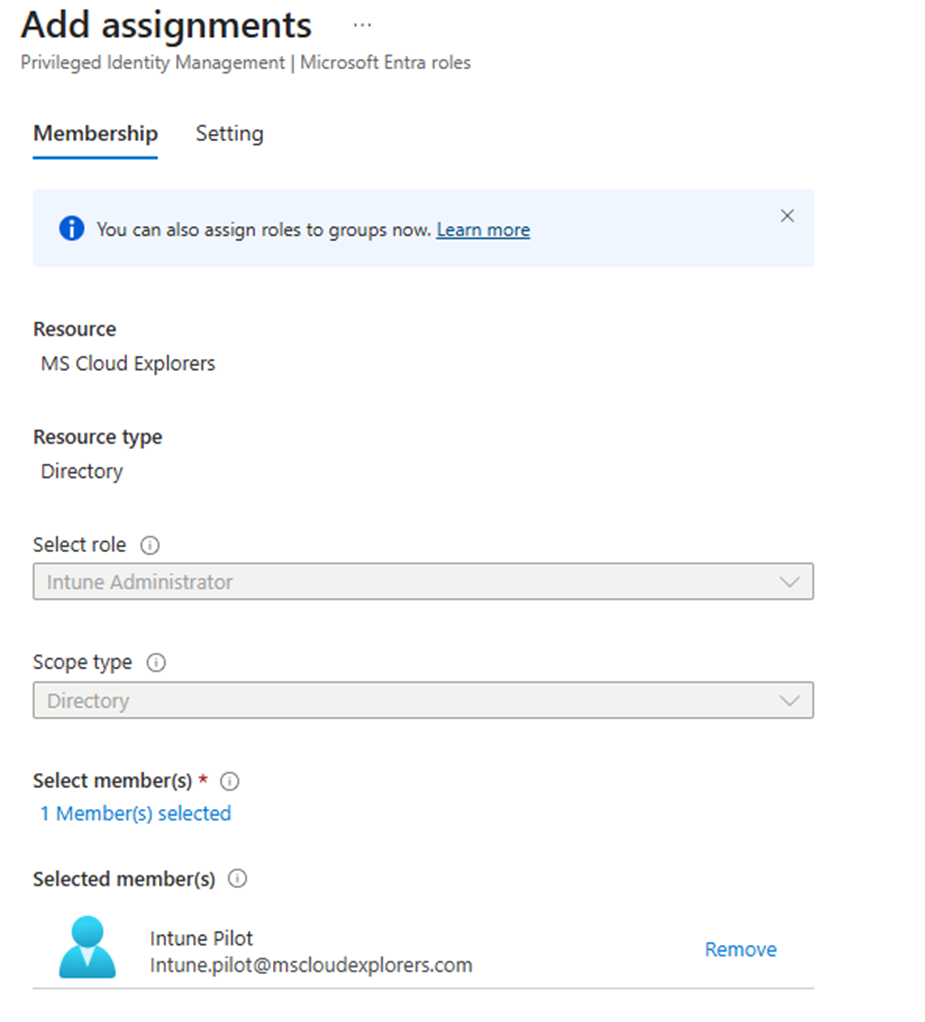
- Under the settings Choose Eligible or Active. (I have explained Briefly about Eligible Assignment below in this blog). So, I’m choosing here Active.
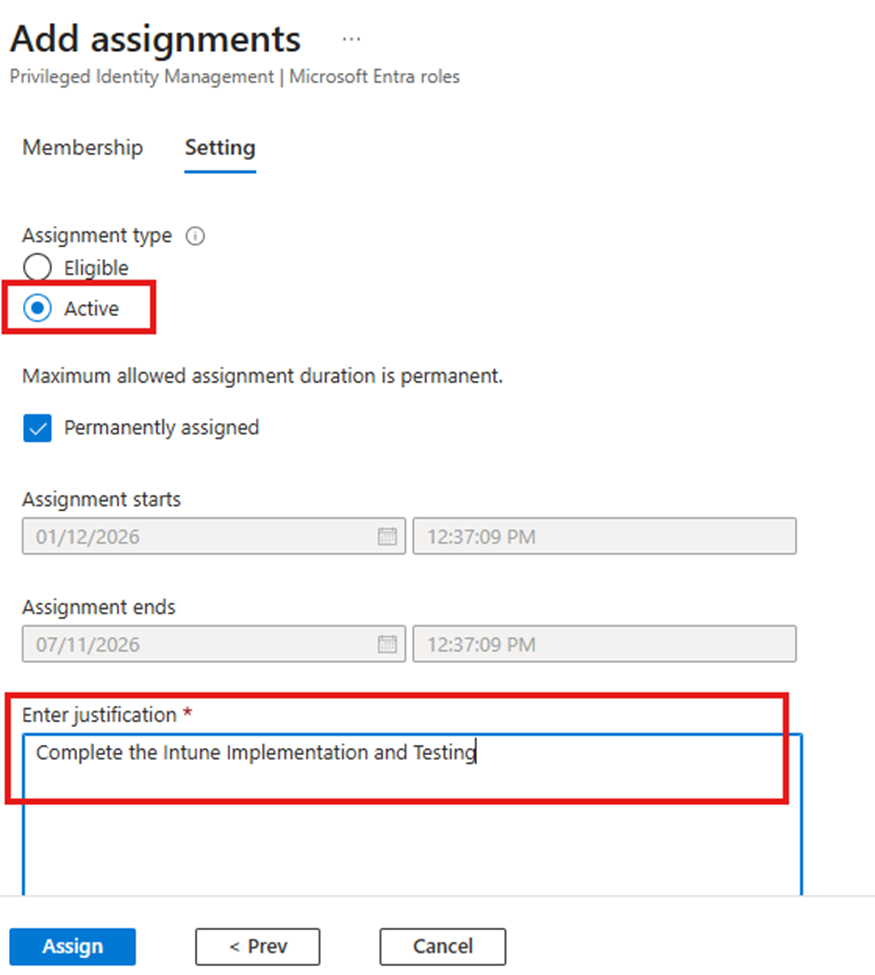
Once the Role is assigned Admin can access the respective Admin center as we as they can verify their Assignment under my Roles in Active Assignments.
Note: Active assignments grant permanent access and should be used only when absolutely necessary.
Modifying Role Settings for Eligible Assignments
You can assign roles using the steps above. During assignment, you will have access to Role Settings.
If a role is already assigned:
- Go to Manage > Assignments
- Select the role and open Settings
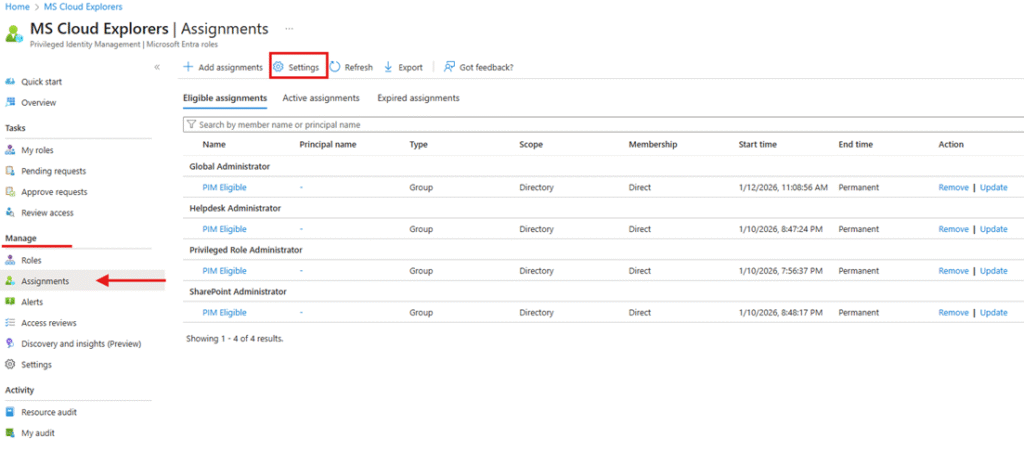
Step 3: Configure Role Settings
- Define activation requirements such as MFA, justification, and approval.
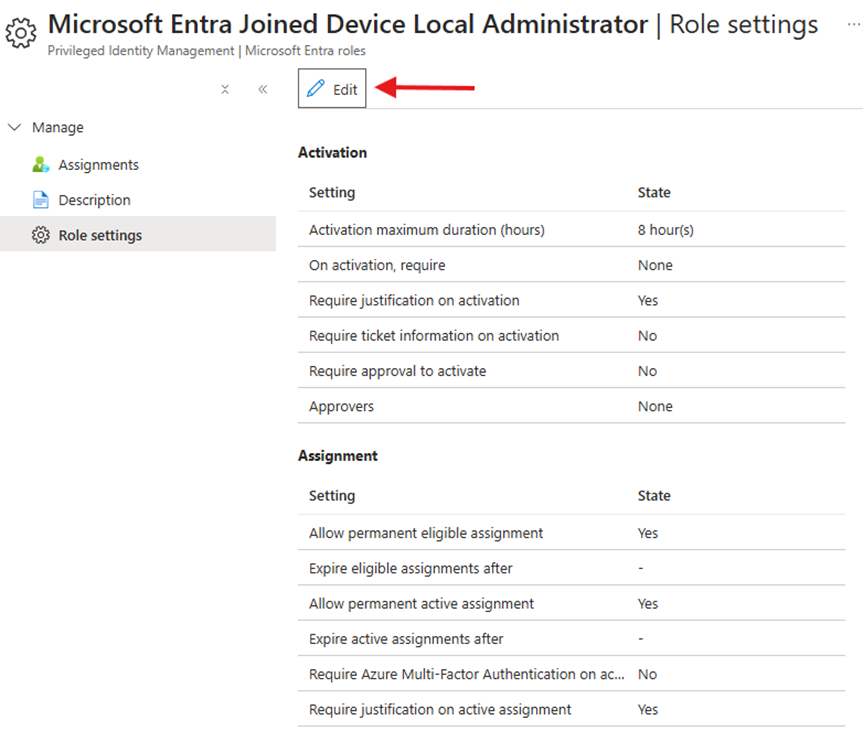
- Set the maximum activation duration to limit how long privileged access remains active.
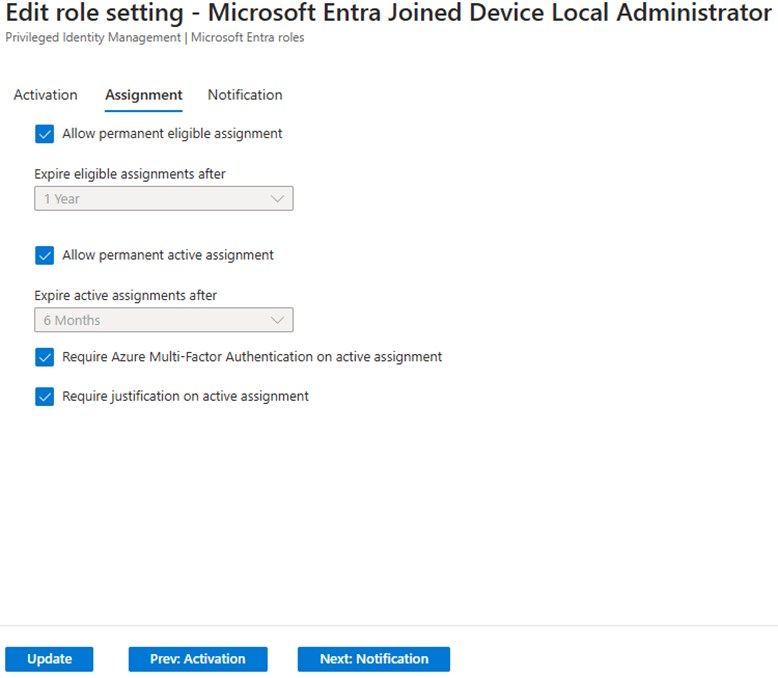
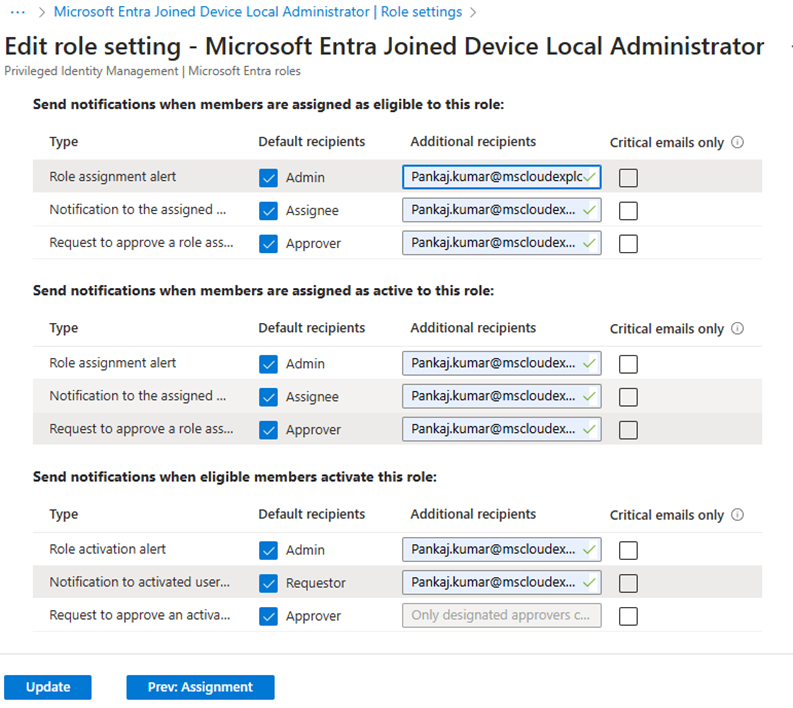
- Enable notifications to track role activations and changes.
For lower-privilege roles (Helpdesk, User Administrator, Exchange Admin):
- Set eligibility for up to 8 hours
- Require justification only
For high-privilege roles (Global Admin, SharePoint Admin):
- Require justification and approval
- Limit activation duration
- Assign approvers using a dedicated security or M365 group.
Using Entra ID security or M365 dynamic groups for admins and approvers makes PIM far easier to manage at scale.
How Eligible Assignments Work
For lower-privileged roles such as Helpdesk Administrator, User Administrator, or Exchange Administrator, you can assign users as Eligible with a maximum activation duration of up to 8 hours. These roles can typically be activated using justification only, without approval.
For high-privileged roles such as Global Administrator or SharePoint Administrator, you should configure activation to require approval. This ensures an additional security checkpoint before elevated access is granted.
In this guide, we will review the experience from:
- The requester’s perspective (admin requesting access)
- The approver’s perspective (approving or denying access)
Best Practice: Use Groups for Role Management
For better governance and scalability, create Entra ID Security Groups or Dynamic Groups.
In this tenant, two groups were created:
- One group for admins eligible for privileged roles
- Another group for PIM approvers and access reviewers
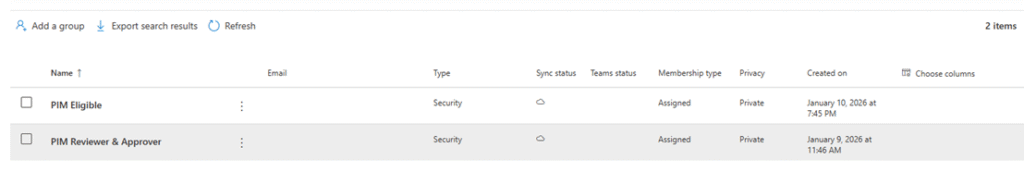
This approach simplifies role management and approval workflows.
Example Scenario
In this example:
- Users are eligible for Exchange Administrator, Privileged Role Administrator, and SharePoint Administrator roles with justification only.
- The Global Administrator role requires approval before activation.
Select the Global Administrator role (or any high-privilege role you want to restrict) and configure it accordingly.
Configure Activation Settings
- Under Activation settings, click the Edit (pencil) icon.
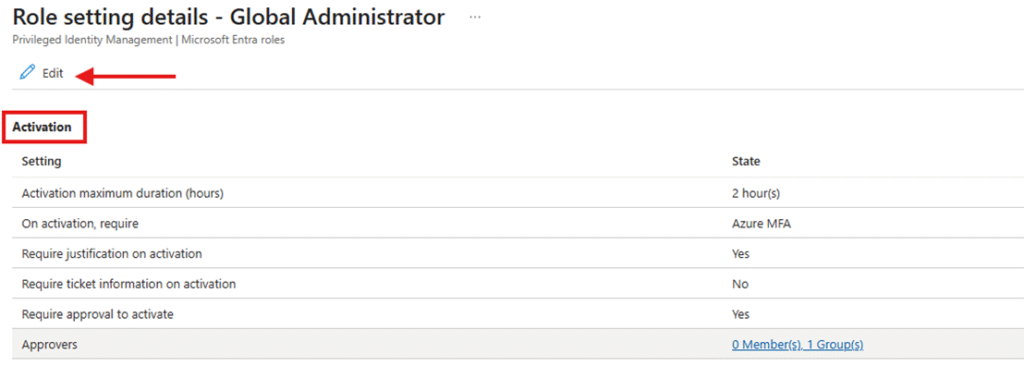
- Define how long admins can activate the Global Administrator role.
- Enable:
- Require justification on activation (for low-privilege roles)
- Require approval to activate (for high-privilege roles)
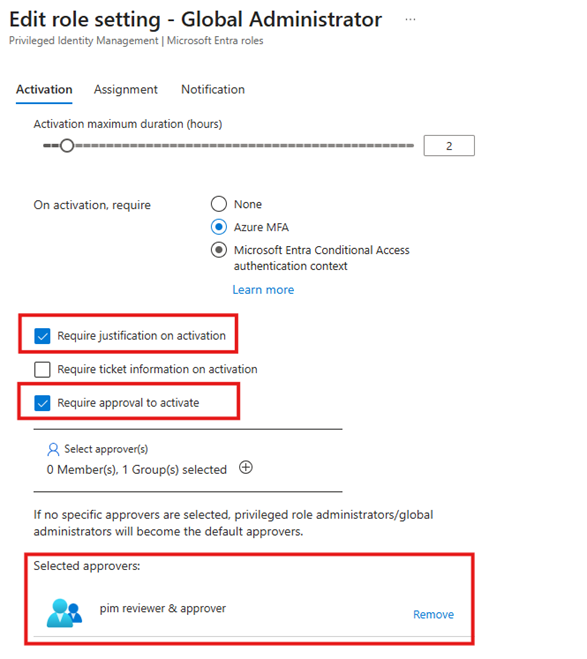
- If you use a ticketing system, enable Require ticket information on activation.
- Add the Approver Admins group and save the changes.
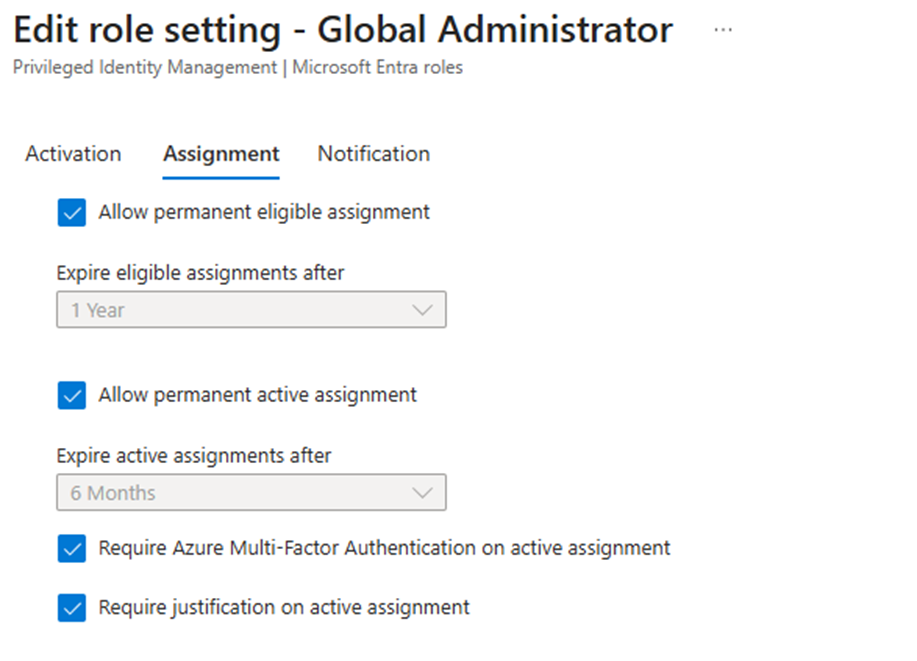
Under the Activation tab, you can also configure eligibility expiration and other related settings. Default values are sufficient for most environments, but you can adjust them to meet your requirements.
Notifications Configuration
By enabling notifications for role activations, you can track when privileged roles are activated. See the above Notifications management.
Best practice: Use Microsoft 365 groups for PIM approvers and eligible admins to simplify notification management.
How Admins Check Eligibility and Activate PIM Roles
- Sign in to entra.microsoft.com.
- Navigate to Privileged Identity Management under the ID Governance menu.
- Click My roles.
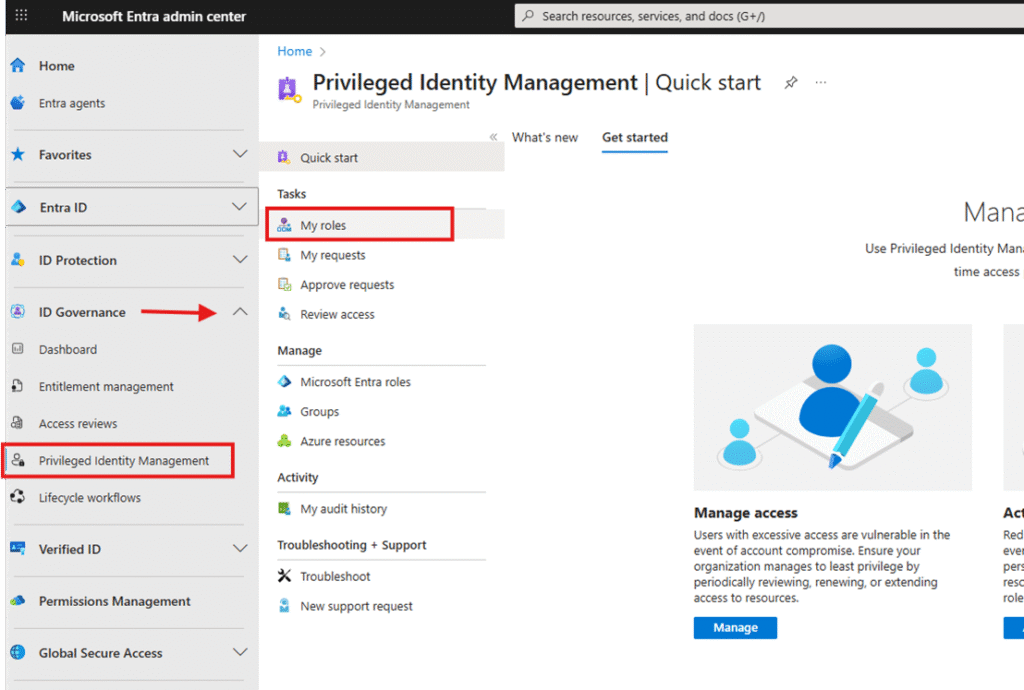
Under Eligible assignments, you will see the roles available for activation.
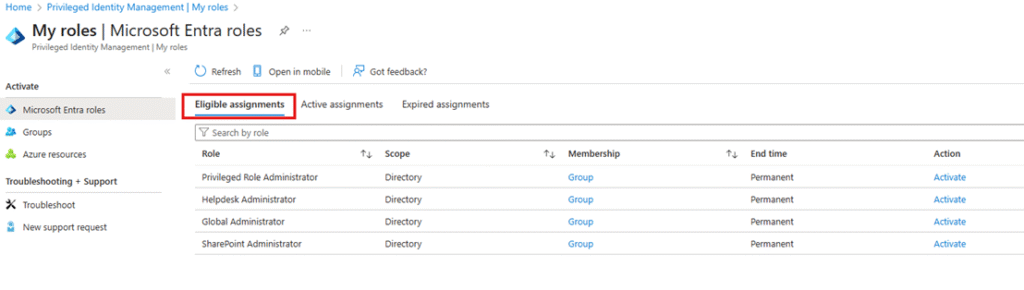
Activating a Role Without Approval
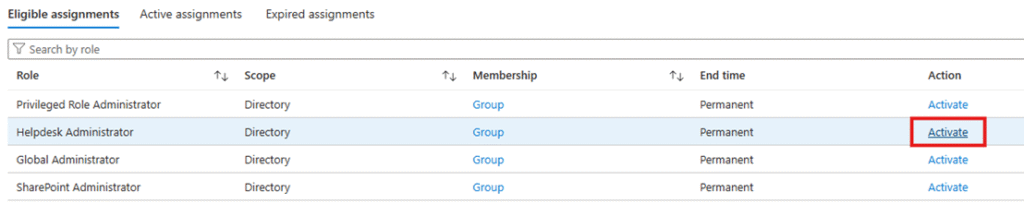
- Select Helpdesk Administrator.
- Click Activate on the right side.
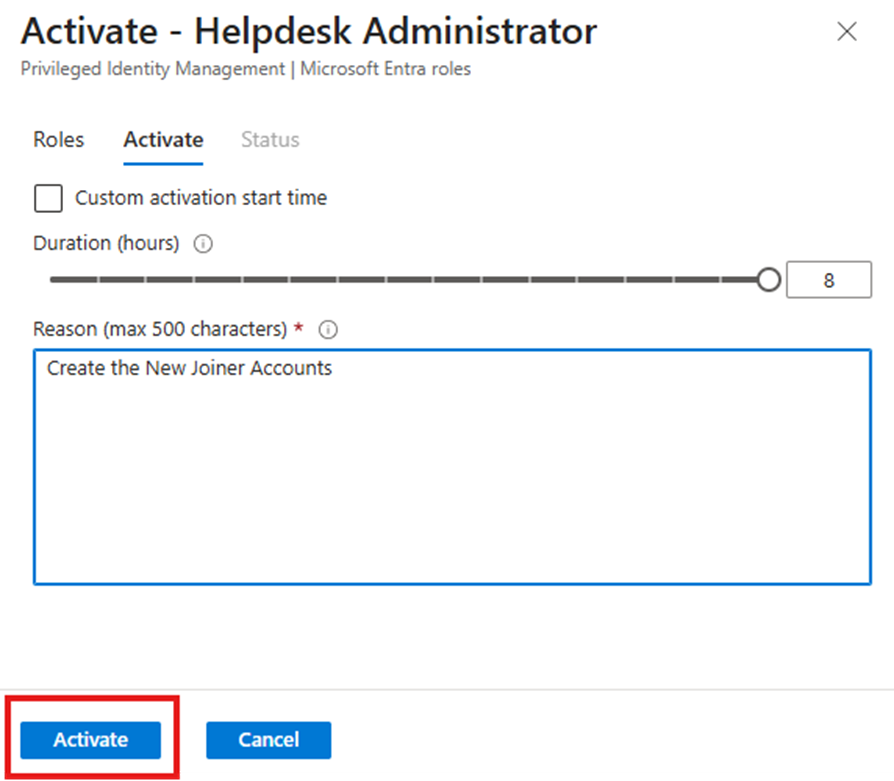
- In the activation window, provide a justification and click Activate.
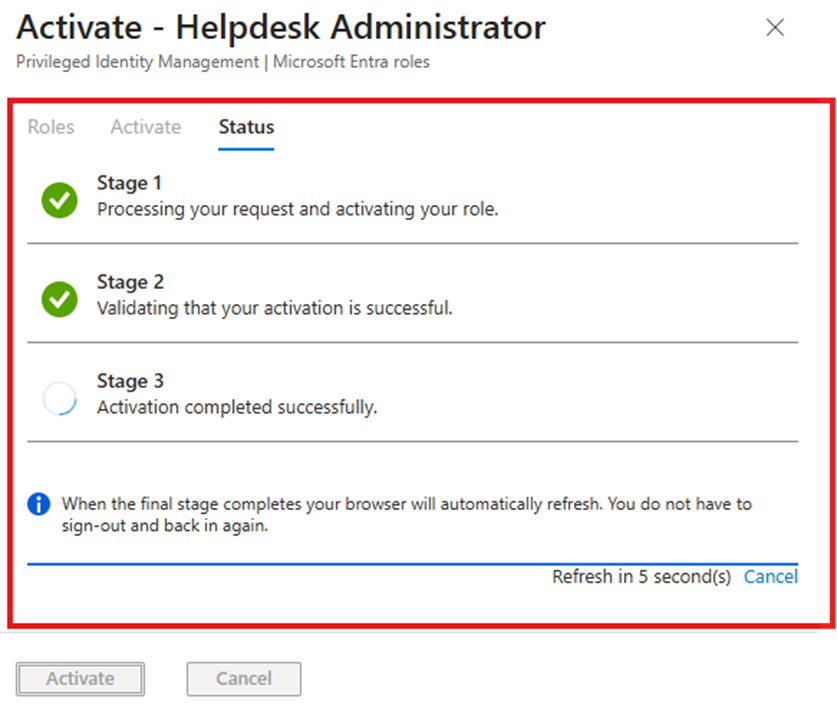
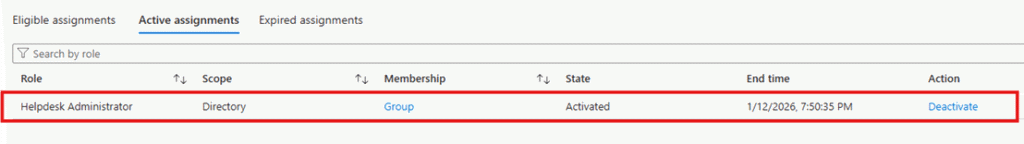
The activation process includes three automatic stages. Once completed:
- The role becomes active
- The browser refreshes automatically
- You can verify activation under the Active assignments tab
Activating a Role That Requires Approval
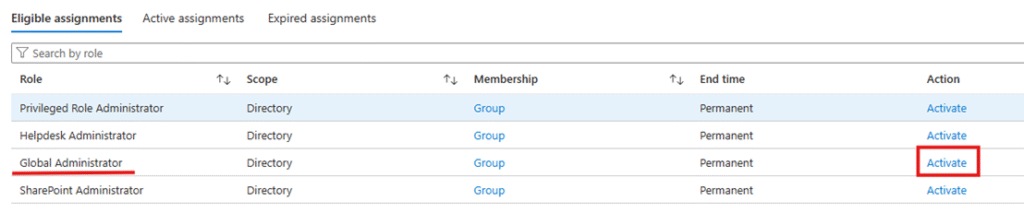
- Go to the Eligible assignments tab.
- Select the Global Administrator role.
- Click Activate and provide justification.
You will see similar activation stages, but instead of immediate access, a notification appears indicating the request is pending approval.
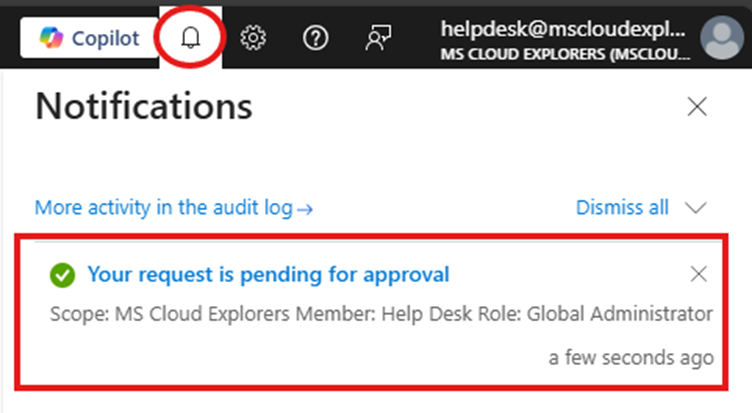
Approval Workflow (Approver Experience)
- All PIM approvers receive an email notification.
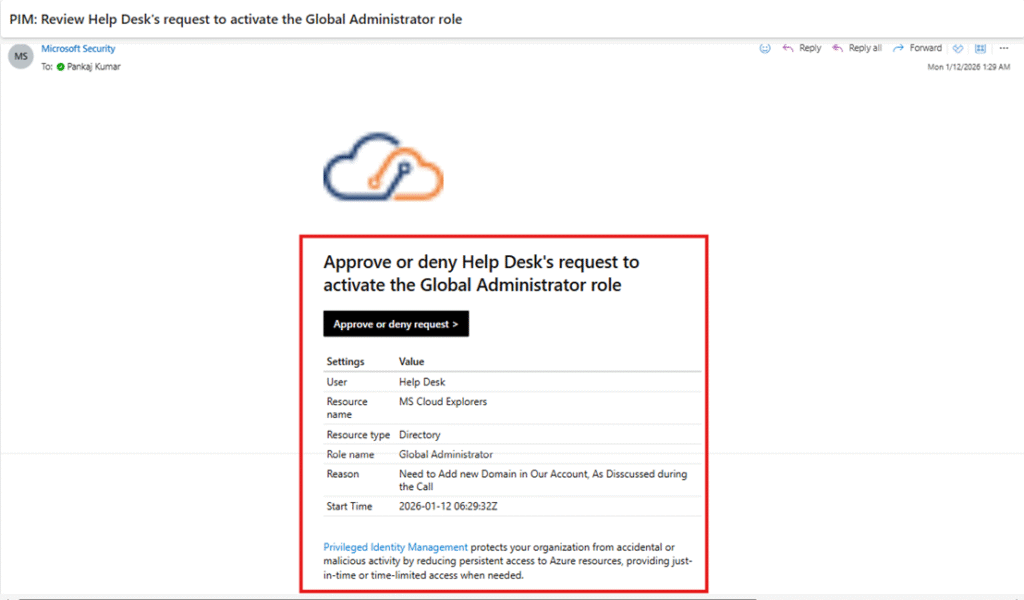
- Clicking Approve or Deny redirects them to the Entra Admin Portal – Approve Requests page.
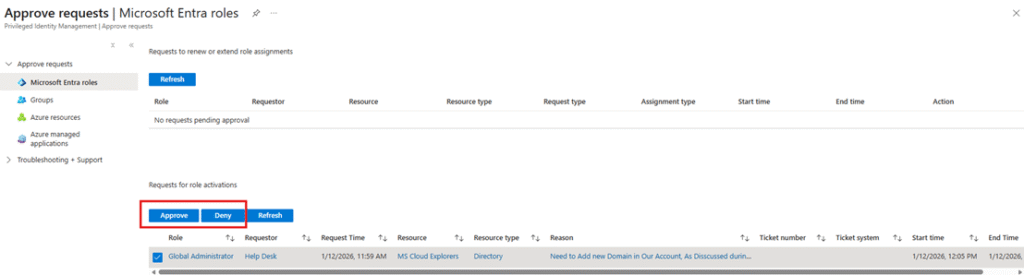
- Approvers must provide justification and confirm the action.
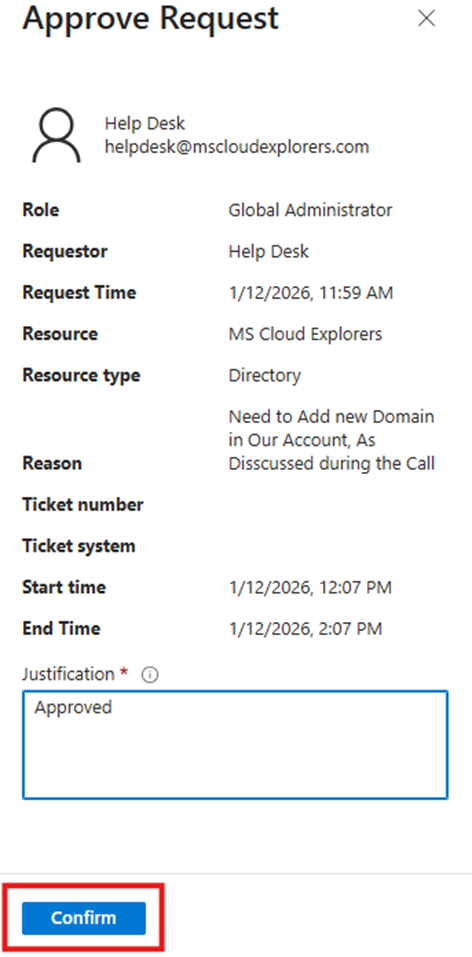
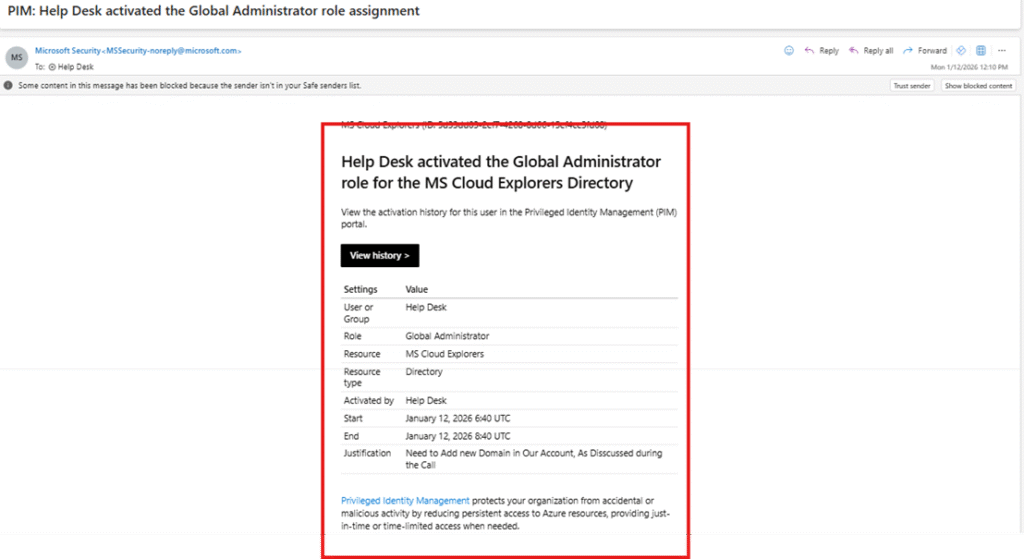
Once approved or denied:
- The requester receives an email notification
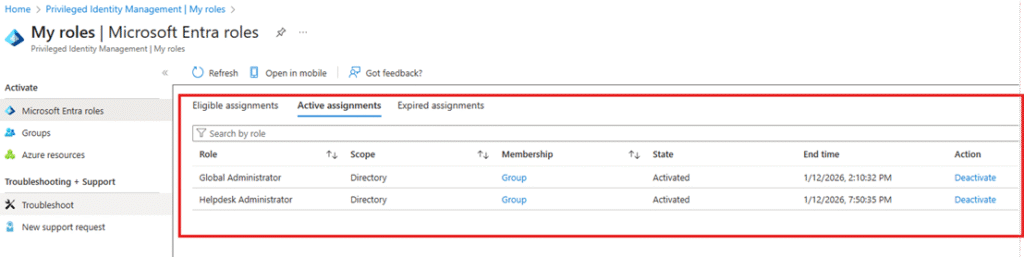
- The admin can verify role status under My roles > Active assignments
Step 5: Configure Access Reviews
- Go to PIM > Access Reviews
- Click New Access Review
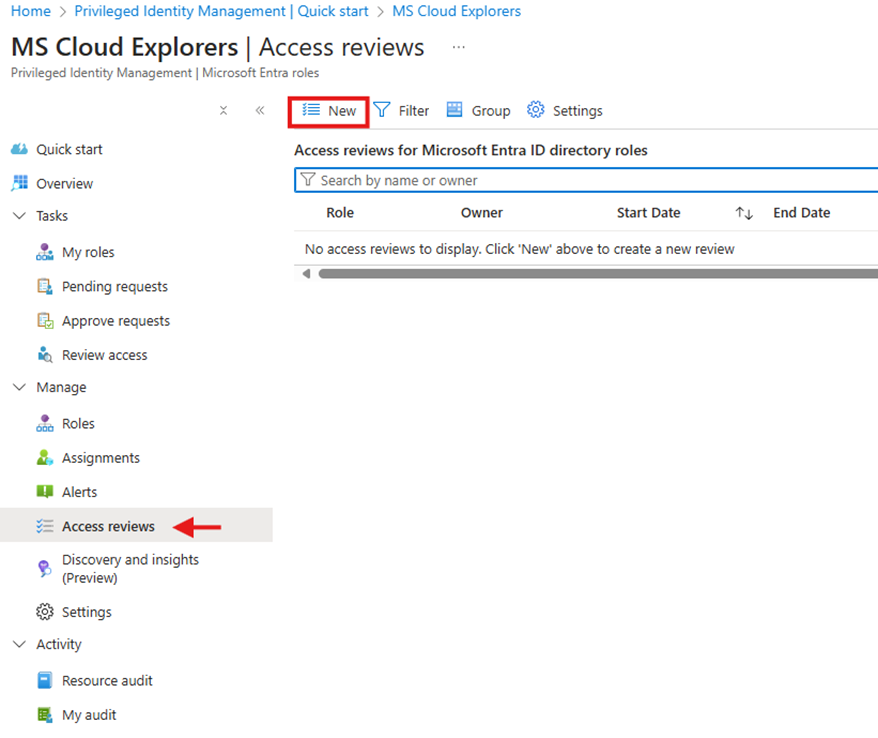
- Define reviewers and review frequency
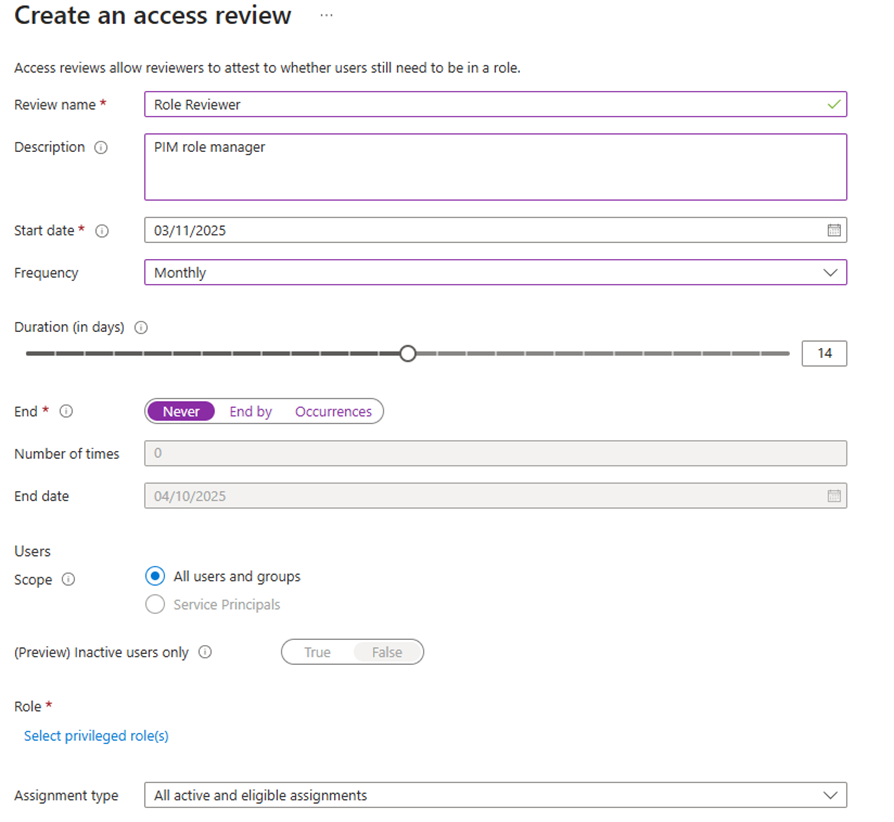
- Enable automatic removal for users who fail reviews
Access reviews ensure privileged access remains aligned with business needs.
Conclusion
Whether you call it Azure PIM, Microsoft PIM, or Privileged Identity Management, the goal is the same:
protect critical resources by tightly controlling privileged access.
By implementing just-in-time access, approval workflows, and regular access reviews, organizations can dramatically reduce security risks—without slowing down IT operations.
FAQs
What is Privileged Identity Management?
A Microsoft Entra ID feature that controls and monitors privileged roles.
Which license is required for PIM?
Microsoft Entra ID P2.
Can access reviews be automated?
Yes, PIM supports scheduled and automated access reviews.
Do all users need an Entra ID P2 license?
No—only administrators who use Privileged Identity Management.
Related Links:
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!

I’m not that much of a online reader to be honest but your sites really nice, keep
it up! I’ll go ahead and bookmark your site to come
back down the road. All the best
Thank you so much for the kind words—it really means a lot! 😊
We know there’s a lot out there online, so we truly appreciate you taking the time to check out our site and even bookmarking it. We’ll keep working hard to bring helpful, easy-to-digest content your way. See you again soon, and all the best to you too!
This guide is gold! I’ve been looking for a simplified explanation of PIM for ages. The just-in-time access concept makes so much sense now. Quick question—can we set up approval workflows for certain roles in PIM?
Yes, absolutely—you can configure approval workflows for eligible role assignments in PIM. This adds an extra layer of security by requiring designated approvers before access is granted.