- March 27, 2025
- Pankaj Kumar
- 4
In today’s rapidly evolving digital landscape, safeguarding identity systems is crucial for businesses of all sizes. Cyber threats are becoming more sophisticated, making identity protection a top priority. Microsoft Entra offers a comprehensive suite of identity and access management (IAM) solutions designed to enhance security and prevent unauthorized access.
This guide will explore the best practices for securing Microsoft Entra identities to help your organization stay resilient against cyber threats.
Understanding Microsoft Entra Identities
Microsoft Entra provides a robust IAM framework that helps organizations manage identities, control access, and protect sensitive data. Key components of Microsoft Entra include:
- Azure Active Directory (Azure AD) – Centralized identity management.
- Permissions Management – Controls and monitors permissions across the organization.
- Verified ID – Secure identity verification system.
- Conditional Access – Enforces security policies for users and devices.
Key Benefits of Microsoft Entra Identities
- Centralized identity management for easier access control.
- Multi-Factor Authentication (MFA) for enhanced security.
- Conditional Access policies to regulate access based on specific criteria.
- Advanced threat detection and response capabilities.
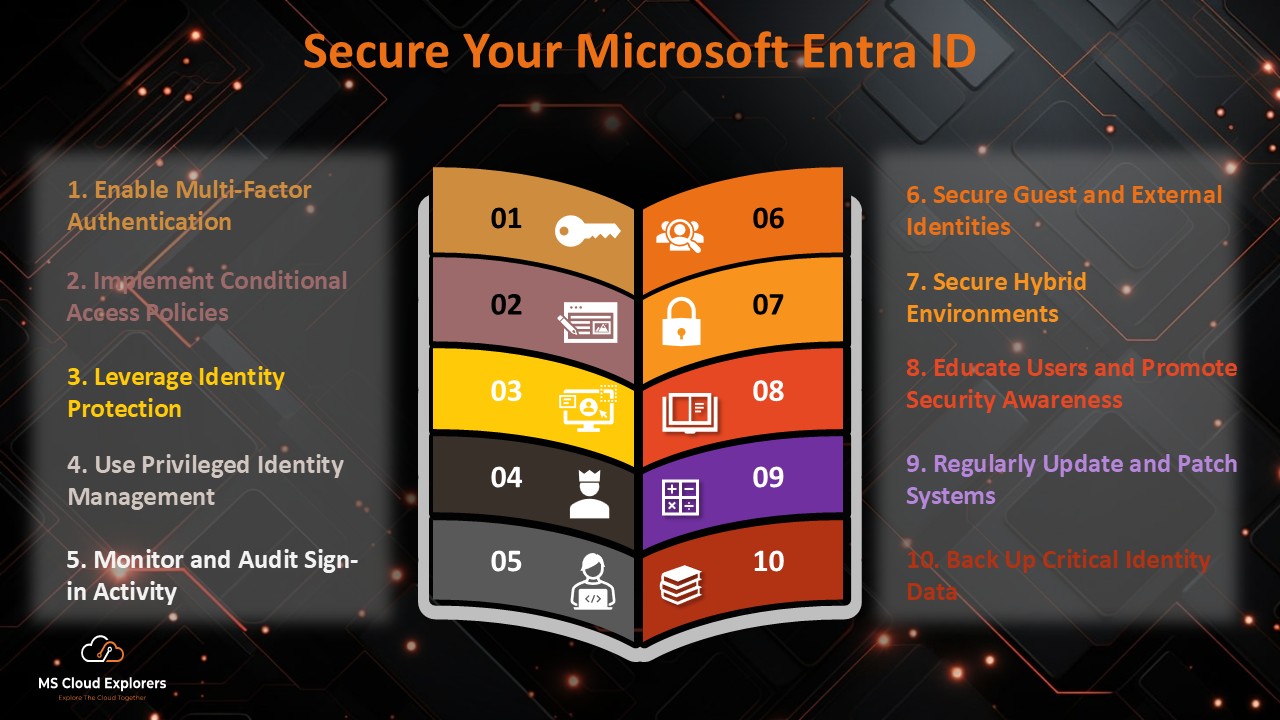
Best Practices for Securing Microsoft Entra Identities
1. Enable Multi-Factor Authentication (MFA)
Why it matters: MFA adds an extra layer of security by requiring users to verify their identity through multiple authentication methods (e.g., password + mobile app or biometrics).
Best practices:
- Enforce MFA for all users, especially administrators and high-risk accounts.
- Use Microsoft Authenticator for a seamless authentication experience.
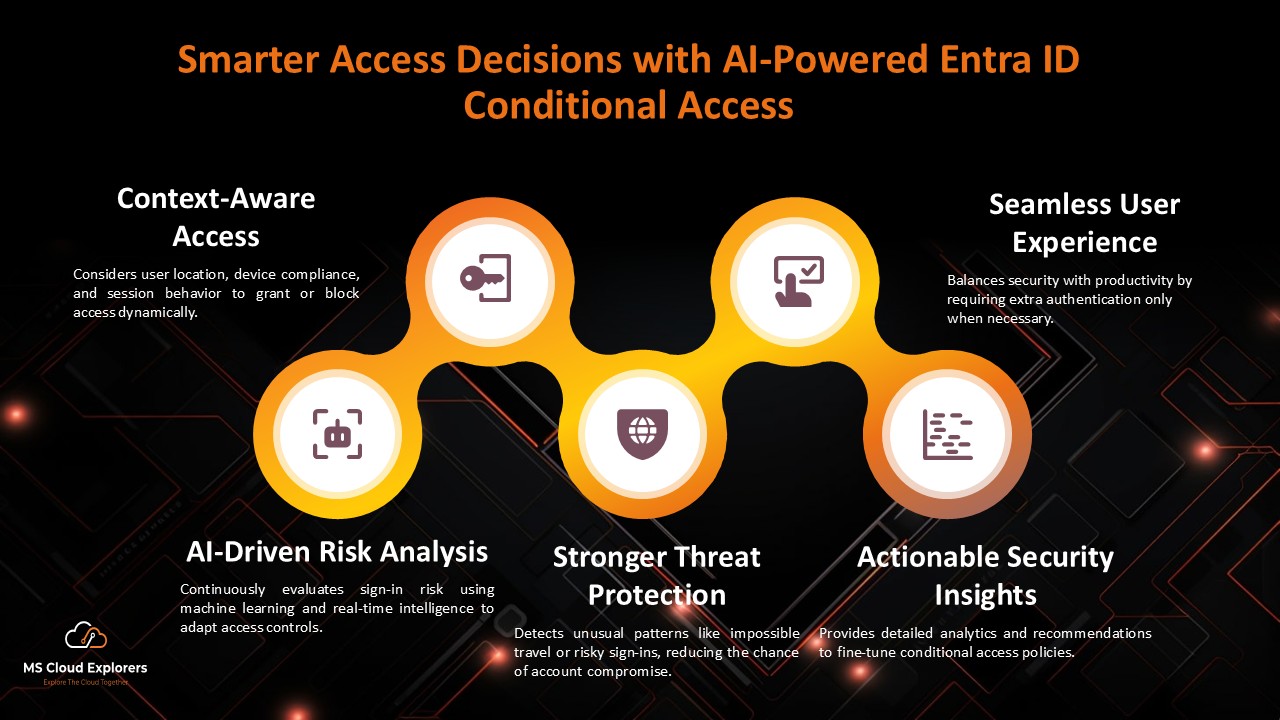
2. Implement Conditional Access Policies
Why it matters: Conditional Access policies allow you to define access rules based on conditions such as user location, device compliance, and risk level.
Best practices:
- Restrict access from untrusted locations.
- Require compliant devices for access.
- Block legacy authentication protocols.
Check out the complete guide on How Conditional Access in Azure AD works.
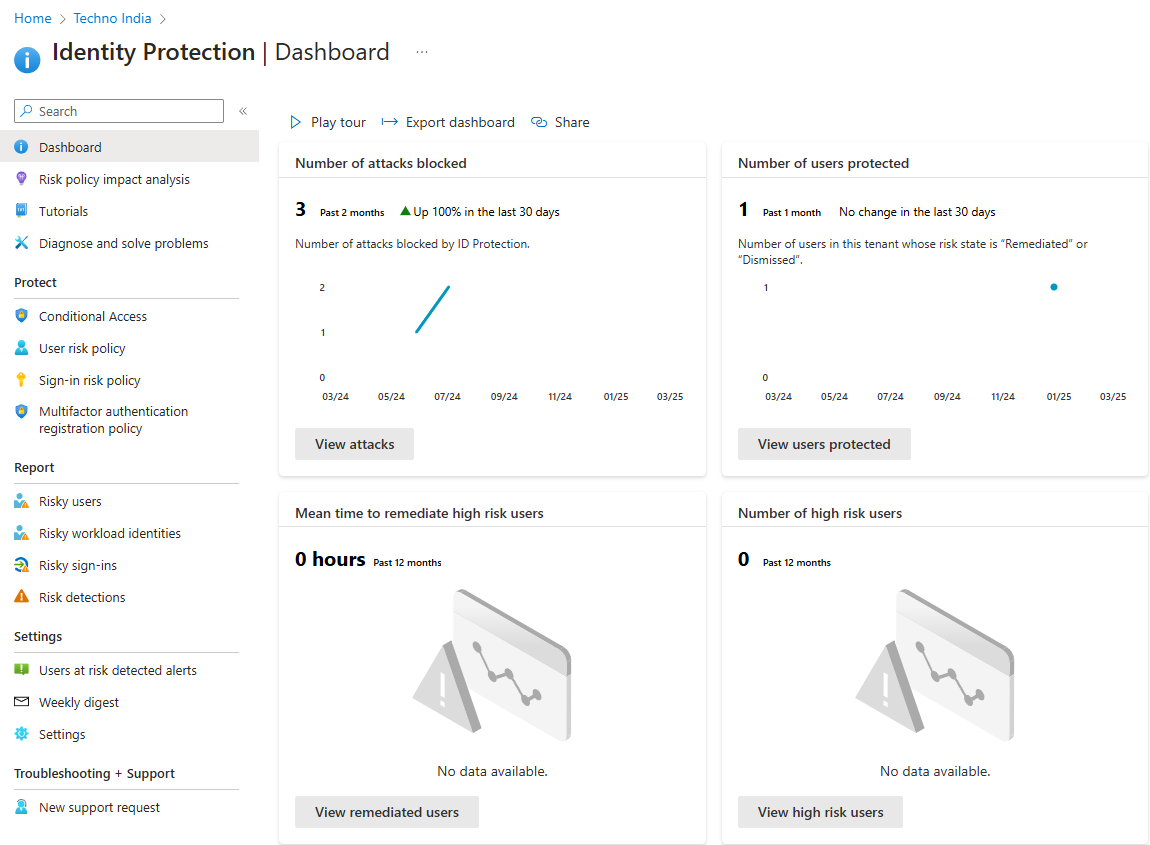
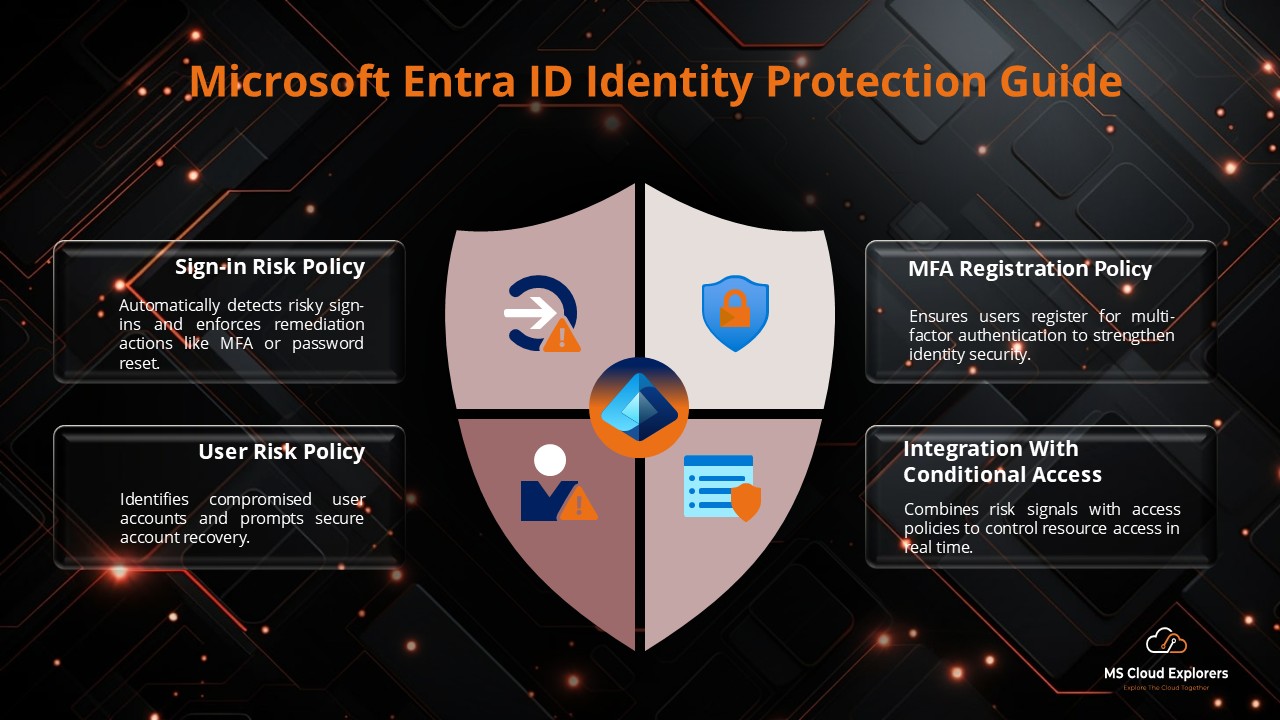
3. Leverage Identity Protection
Why it matters: Microsoft Entra Identity Protection uses AI to detect and respond to suspicious activities such as compromised accounts and high-risk sign-ins.
Best practices:
- Enable Identity Protection to detect and respond to high-risk sign-ins.
- Set up automated remediation actions (e.g., password reset or access blocks).
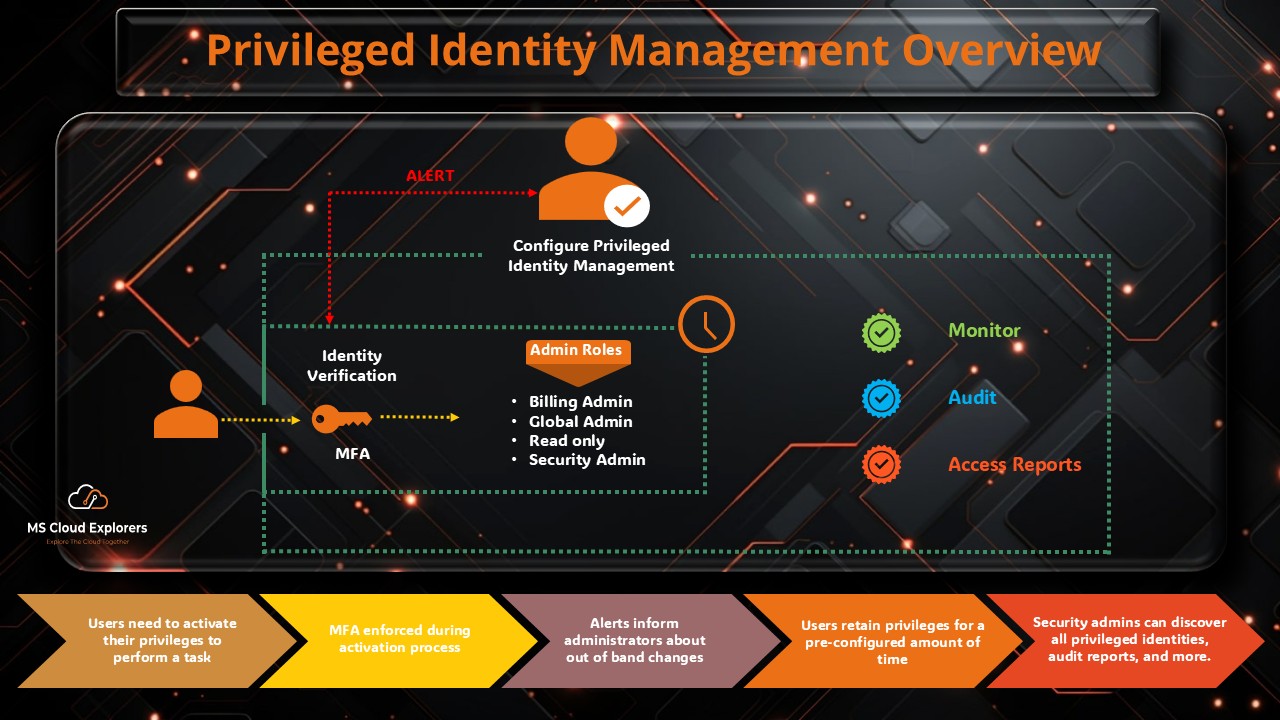
4. Use Privileged Identity Management (PIM)
Why it matters: PIM minimizes the risk of overprivileged accounts by providing just-in-time access to critical resources.
Best practices:
- Implement PIM to restrict elevated access to sensitive roles.
- Use approval workflows for additional security oversight.
Check out the step-by-step guide on Azure AD Privilege Identity Management
5. Monitor and Audit Sign-in Activity
Why it matters: Regularly monitoring sign-in activities can help detect security breaches.
Best practices:
- Use Azure AD Sign-in logs to track failed and successful login attempts.
- Set up alerts for unusual sign-in patterns (e.g., logins from unfamiliar locations).
6. Secure Guest and External Identities
Why it matters: External users increase the attack surface, requiring strict access controls.
Best practices:
- Use Access Reviews to periodically review and remove unnecessary guest access.
- Configure guest access policies to limit external user permissions.
- Apply Conditional Access policies for guest users.
7. Secure Hybrid Environments
Why it matters: Many organizations operate in hybrid environments, requiring secure integration between on-premises and cloud identities.
Best practices:
- Use Microsoft Entra ID Connect to sync on-premises identities with Entra ID.
- Enable Password Hash Synchronization to reduce reliance on on-premises infrastructure.
- Implement Hybrid Conditional Access to secure access across environments.
8. Educate Users and Promote Security Awareness
Why it matters: Human error remains one of the leading causes of security breaches.
Best practices:
- Conduct regular security training sessions.
- Educate users on phishing attacks and password best practices.
- Encourage employees to report suspicious activities.
9. Regularly Update and Patch Systems
Why it matters: Outdated software contains vulnerabilities that hackers exploit.
Best practices:
- Ensure all systems are updated with the latest patches.
- Use automated patch management tools for efficiency.
10. Back Up Critical Identity Data
Why it matters: A strong backup strategy ensures quick recovery in case of cyberattacks or data loss.
Best practices:
- Regularly back up identity-related data.
- Store backups in a secure, separate location.
Advanced Tools to Enhance Microsoft Entra Identities’ Security
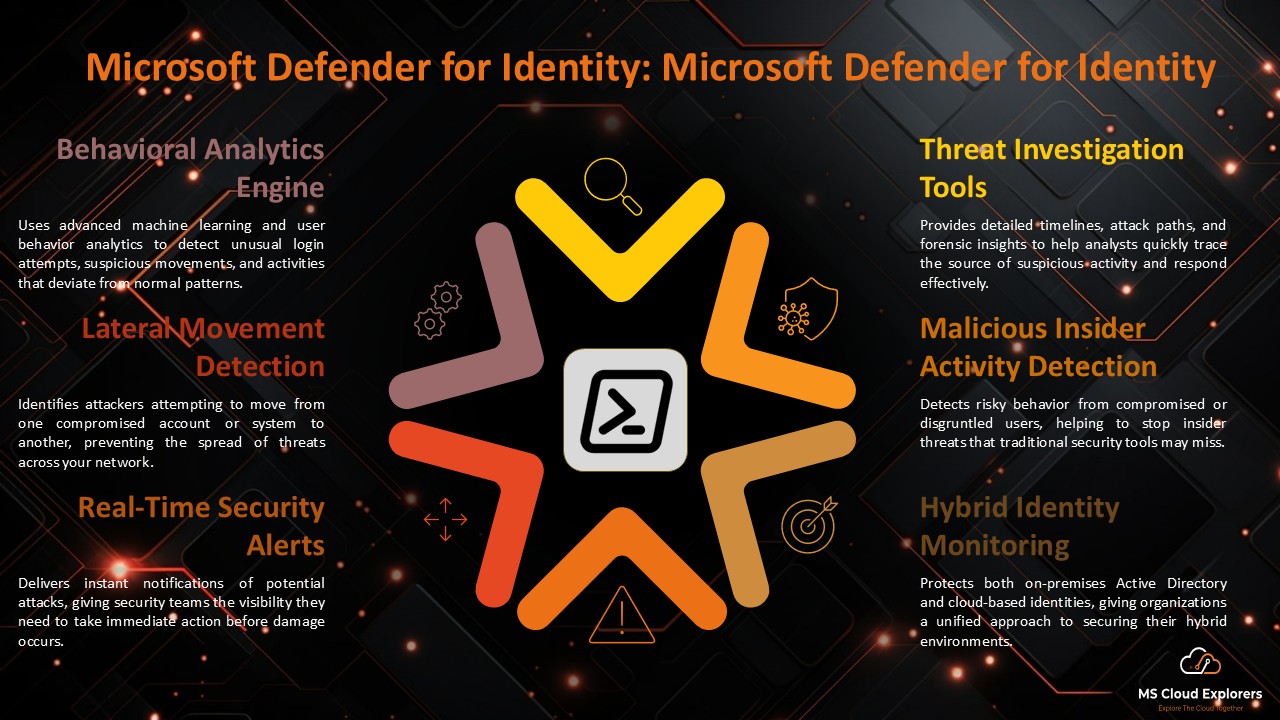
- Microsoft Defender for Identity – Monitors user behavior and detects threats.
- Azure AD Application Proxy – Enables secure access to on-premises applications.
- Verified ID – Decentralized identity solution for secure credential verification.
- Microsoft Secure Score – Provides security assessments and recommendations.
Conclusion
Securing Microsoft Entra identities is essential for maintaining a strong cybersecurity posture in an increasingly digital world. By implementing best practices such as Multi-Factor Authentication, Conditional Access, and Privileged Identity Management, organizations can significantly reduce security risks. Regular monitoring, user education, and advanced security tools further strengthen identity protection.
By taking a proactive approach to identity security, businesses can safeguard their assets, protect user data, and maintain compliance with industry regulations.
FAQs
- What are Conditional Access policies in Microsoft Entra?
Conditional Access policies allow organizations to enforce access control based on specific conditions like user location, device compliance, or sign-in risk. These policies help ensure only trusted users and devices can access organizational resources. - How does Microsoft Entra Identity Protection work?
Microsoft Entra Identity Protection uses machine learning to detect risky sign-ins and compromised accounts. It provides administrators with actionable insights and automated responses, such as blocking access or requiring a password reset. - What is Privileged Identity Management (PIM) in Microsoft Entra?
PIM is a feature in Microsoft Entra that minimizes the risks of overprivileged accounts by enabling just-in-time access to sensitive roles. It requires role activation and approval workflows, adding an extra layer of security for privileged accounts. - What is the difference between Password Hash Synchronization and Pass-through Authentication in a hybrid environment?
Password Hash Synchronization stores a hash of users’ on-premises passwords in Azure AD, enabling users to sign in without relying on on-premises infrastructure.
Pass-through Authentication validates passwords directly against the on-premises Active Directory, ensuring that credentials are not stored in the cloud. - How can I monitor suspicious sign-in activities in Microsoft Entra?
You can monitor suspicious sign-ins using the Sign-in logs in Azure AD. These logs provide detailed information about user activities and highlight anomalies, such as logins from unfamiliar locations or devices. Administrators can also configure alerts for high-risk sign-ins. - Can Microsoft Entra be integrated with third-party applications?
Yes, Microsoft Entra supports integration with thousands of third-party applications. Administrators can use pre-built connectors or configure custom integrations to ensure secure access to both cloud and on-premises apps.
Explore More from MS Cloud Explorers
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!


Really appreciate this in-depth guide on securing Entra identities! It breaks down critical steps like MFA, PIM, and access reviews clearly. One suggestion: adding a quick risk-level cheat sheet—for example, ‘Low: MFA only; Medium: add PIM; High: combine with privileged access workstations’—could help admins quickly triage threats. Great job!
“Great guide on securing Entra identities! The best practice tips—like MFA enforcement, Privileged Identity Management, and risk-based access—are clear and actionable. One suggestion: could you include a short matrix showing which features are available in different license tiers (P1 vs P2)? Thanks for the practical advice
Thank you! I’m glad you found the best practices helpful. That’s a smart suggestion—I’ll add a quick license comparison (P1 vs P2) to clarify feature availability. Appreciate your feedback!
Thanks for your insightful feedback! I’m glad the guide was clear and practical. I love the idea of a risk-level cheat sheet—it would be a fantastic quick-reference tool. I’ll add that section soon, outlining how to layer security based on risk scenarios. Thanks for helping make this resource even more actionable!