Ever felt like your digital identity is being watched? Well, it probably is—and not just by IT security teams, but also by cybercriminals. That’s where Identity Protection comes in, and Microsoft has a solid solution in the form of Entra ID Identity Protection. This feature-rich tool helps you detect, investigate, and respond to identity-based threats automatically.
Understanding Identity Protection
Identity Protection is a built-in tool within Microsoft Entra ID that helps organizations detect potential vulnerabilities affecting identities, configure automated responses, and investigate incidents.
Why Identity Protection Matters
With the explosion of remote work and hybrid environments, attackers aren’t targeting firewalls—they’re going straight for identities. Why hack through layers of security when you can just steal a password?
Growing Threats in the Digital Landscape
Phishing, brute force, token replay, and credential stuffing attacks are more frequent than ever. Even experienced users can fall prey to convincing scams, making identity protection a necessity—not a luxury.
Core Components of Microsoft Entra ID Identity Protection
Risk Detection
Microsoft continuously monitors billions of signals to detect risky behaviors.
How Microsoft Detects Risky Users
Microsoft uses machine learning and global threat intelligence to flag unusual behavior, such as:
- Sign-ins from unusual locations
- Impossible travel (signing in in a couple of minutes from London and New York))
- Use of anonymous IP addresses
Risk Investigation
Knowing there’s a risk isn’t enough—you need context.
How to Analyze User Risk
Admins can deep-dive into a user’s sign-in history, location, device info, and activities.
Understanding Sign-in Risk vs User Risk
- Sign-in risk is about a specific login attempt.
- User risk is about the overall risk level for the user over time.
Risk Remediation
Automated Responses
You can configure automatic actions like password reset or MFA requirement if a risk is detected.
Manual Interventions
Admins can also manually confirm or dismiss risks based on investigation outcomes.
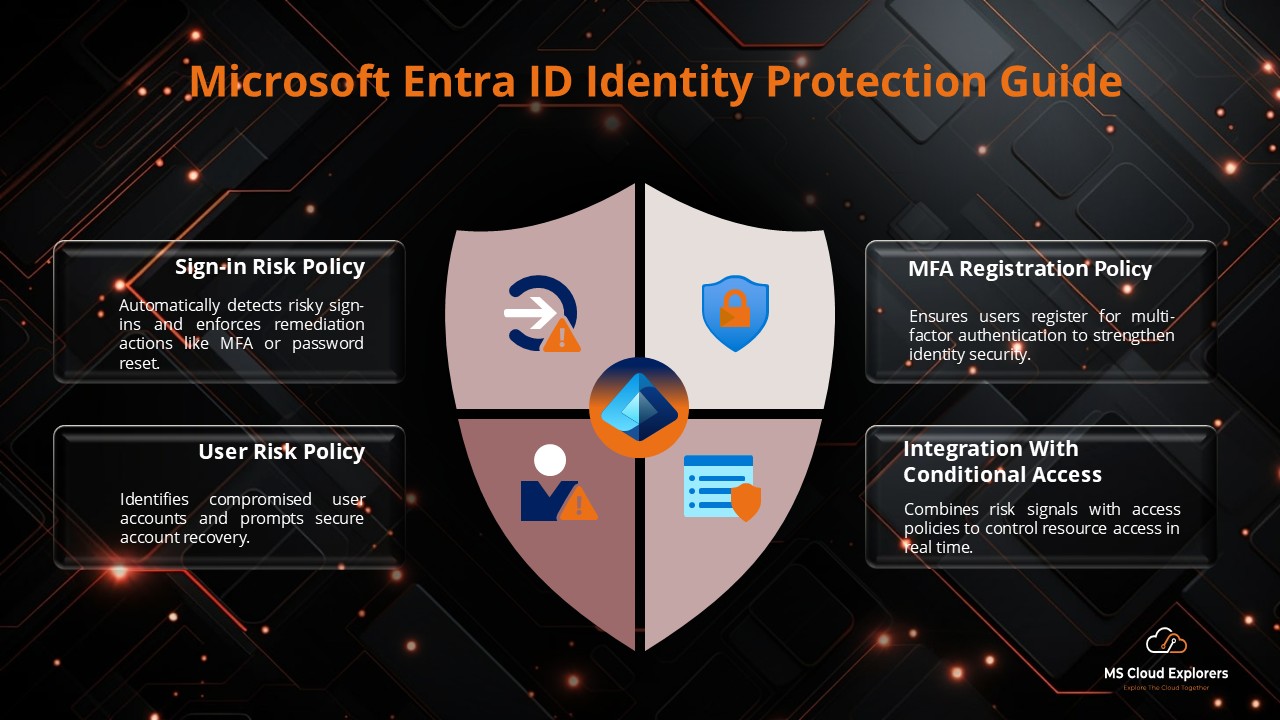
Key Features of Identity Protection in Microsoft Entra ID
Sign-in Risk Policies
Create conditions that block access or require MFA based on risk Factor.

User Risk Policies
Apply Automatically force a password reset when user risk hit a threshold.

MFA Registration Policy
Ensure users register for Multi-Factor Authentication before being granted access to sensitive resources.

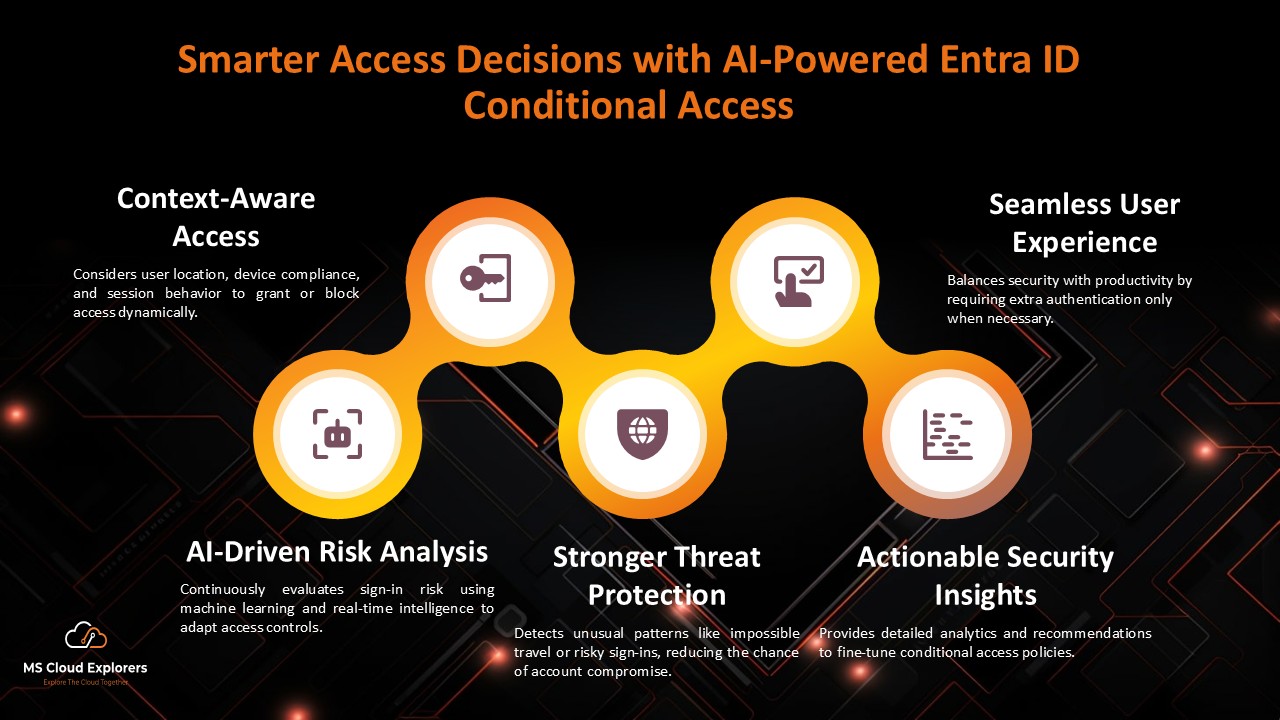
Integration with Conditional Access
Identity Protection works seamlessly with Conditional Access policies, giving you fine-tuned control over who gets in, when, and how.

Benefits of Microsoft Entra ID Identity Protection
Strengthening Your Zero Trust Strategy
Zero Trust assumes breach and verifies every request. Identity Protection fits perfectly by validating trustworthiness at each access point.
Reducing Attack Surface Automatically
With automation in place, risky behaviors can be cut off before they escalate into breaches.
Improving Compliance and Audit Readiness
Detailed logs and reports help meet regulatory requirements and simplify audits.
How to Configure Identity Protection
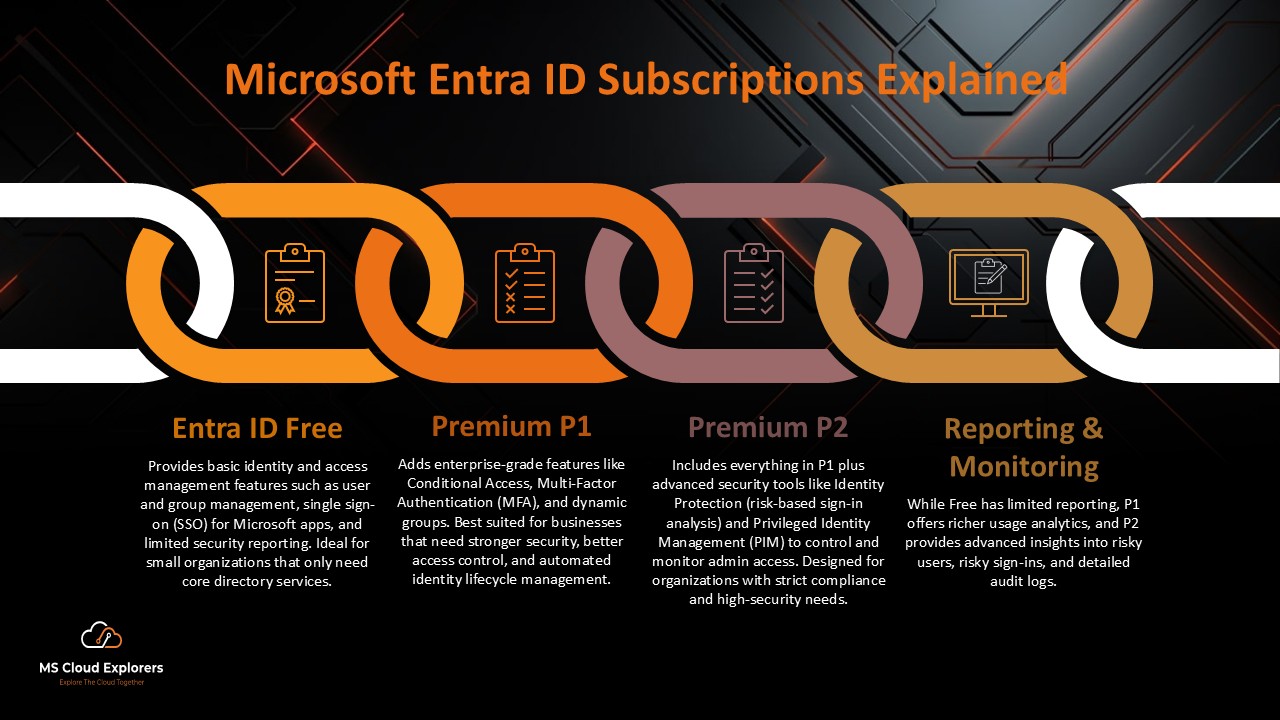
Licensing Requirements
You’ll need Microsoft Entra ID P2 (formerly Azure AD Premium P2) for full access to Identity Protection features.
Setting Up Risk Policies
You can create custom policies based on user roles, departments, or geographical location to tailor protection to your needs.
Monitoring and Responding to Alerts
Utilize the Entra ID’s Identity Protection dashboard to keep an eye on risks in real time and take swift action.
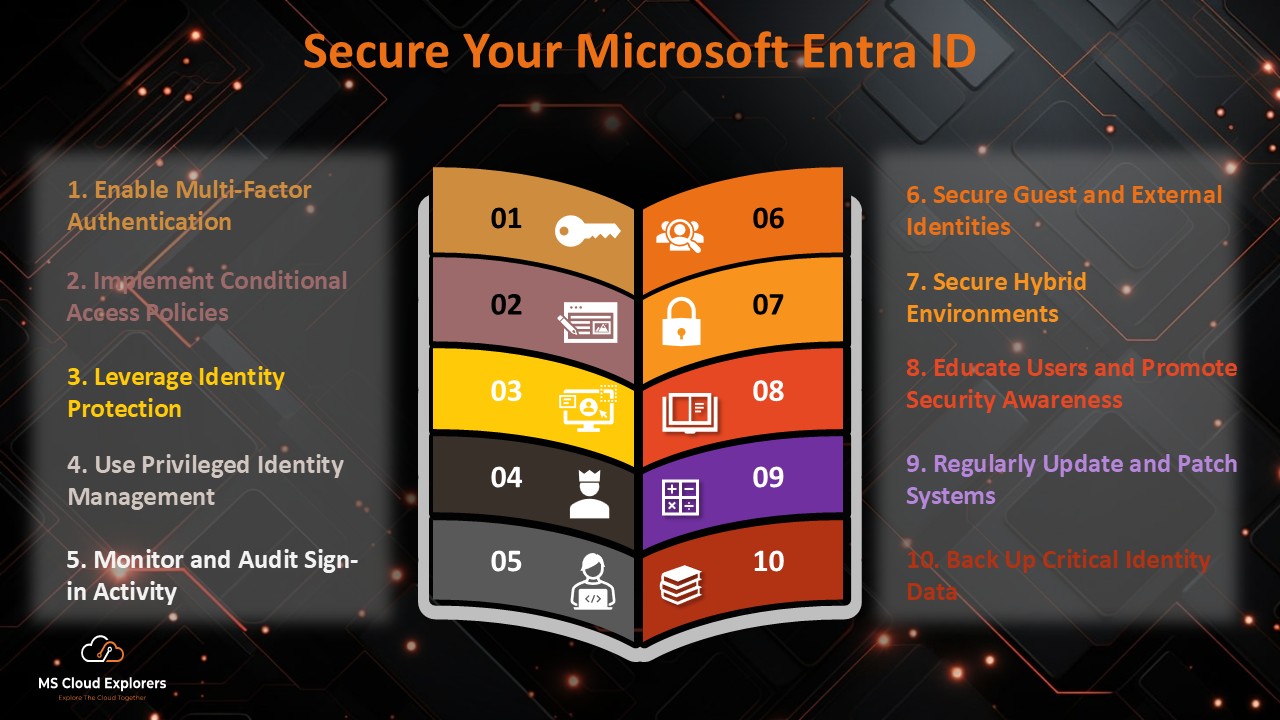
Best Practices for Maximizing Identity Protection
Review Risk Events Regularly
Don’t just set and forget. Reviewing alerts and user activity helps you catch things automation may miss.
Enable MFA for All Users
This is the bare minimum. MFA reduce over 99% of identity attacks.
Combine with Conditional Access Policies
Use both tools together for maximum coverage and control. Checkout the complete guide on Conditional Access Policy
Use Cases and Real-World Scenarios
Protecting Remote Workforces
Remote worker are often logging in from multiple devices and locations—prime targets for attacks. Identity Protection helps ensure only the right people get in.
Securing High-Privilege Accounts
Admins and executives are juicy targets. Major damage can be avoided with additional layers of protection.
Detecting Credential Stuffing Attacks
Multiple failed logins from different IPs? That’s a red flag, and Identity Protection spots it instantly.
Limitations and Considerations
What Identity Protection Doesn’t Cover
It doesn’t monitor endpoint behavior, email threats, or network-level anomalies. It’s focused strictly on identity signals.
Dependency on User Behavior Patterns
False positives can occur if a user legitimately changes their behavior—like traveling unexpectedly.
Conclusion
Having Microsoft Entra ID Identity Protection for your digital identities is similar to having an intelligent, watchful dog. In addition to identifying risks it also acts—automatically. In today’s threat landscape, relying solely on passwords is like locking your front door and leaving the windows wide open. With Identity Protection, you close those windows, too.
Whether you’re a small business or an enterprise, it’s time to take identity seriously—and Microsoft makes it easy to start.
FAQs
1. What license is required for Microsoft Entra ID Identity Protection?
You need a Microsoft Entra ID P2 (formerly Azure AD Premium P2) license.
2. Does Identity Protection work with on-premises users?
Yes, as long as they authenticate through Entra ID, protections will apply.
3. How does Microsoft calculate user risk?
It analyzes multiple signals like sign-in anomalies, leaked credentials, and device trustworthiness.
4. Can I customize the risk response policies?
Absolutely. You can configure actions based on low, medium, or high-risk levels.
5. What happens if a legitimate user is flagged as risky?
They can be prompted for MFA or a password reset, or admins can review and dismiss the alert manually.
Explore More From MS Cloud Explorers
- A Complete Guide to Privileged Identity Management in Azure AD (PIM)
- Microsoft Entra ID: The Gateway to Microsoft’s Identity and Access Management
- Top 7 Conditional Access Policies Every Organization Should Implement
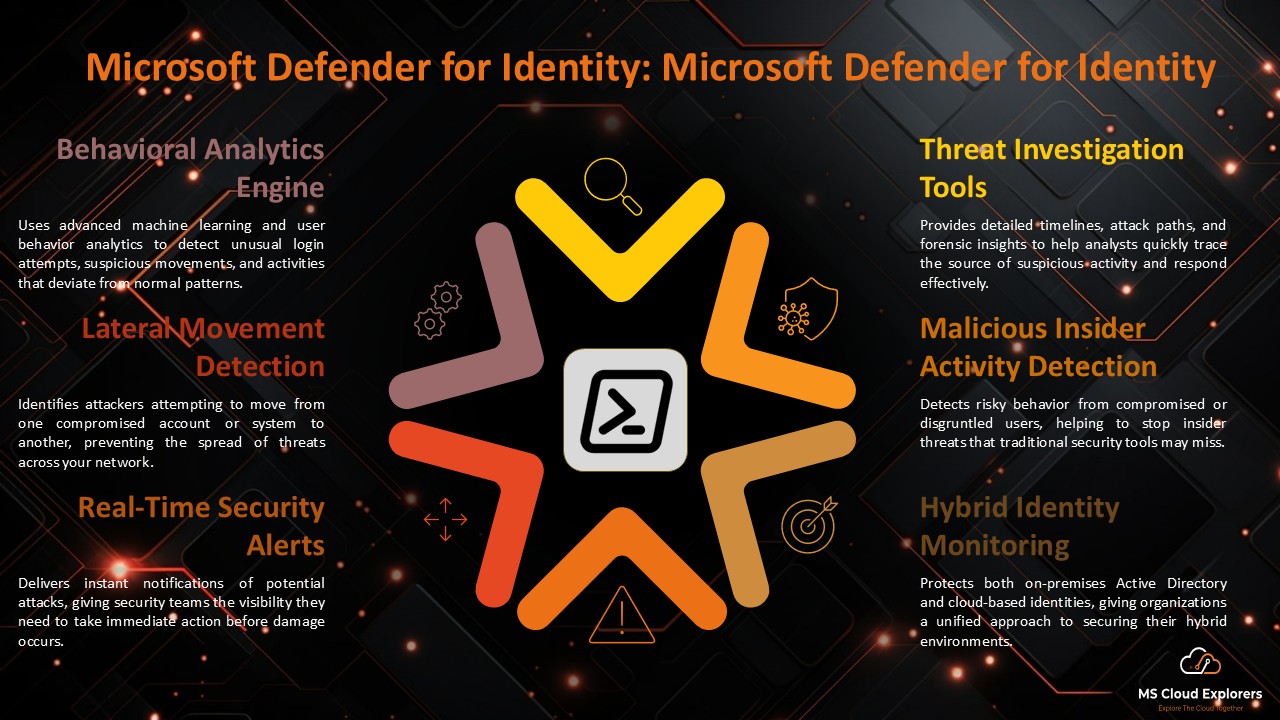
- Microsoft Defender for Identity: Modern Threat Detection and Identity Protection
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!


Excellent deep dive into Entra ID Identity Protection! Your step-by-step setup and explanations of risk policies, alerts, and remediation actions make complex security tools approachable. It’d be even more helpful to include a comparison of Identity Protection features under different licenses (P2 vs P2 with Compliance add‑on) or versus Azure AD Identity Protection. Keep up the amazing content!
Thank you so much for your thoughtful feedback! I’m glad the detailed walkthrough resonated with you. That’s a fantastic suggestion—I’ll update the article with a license comparison section highlighting which Identity Protection capabilities are available under P2 alone vs bundled compliance plans, and clarify how it differs from Azure AD’s version. Your input helps make the guide even more valuable!