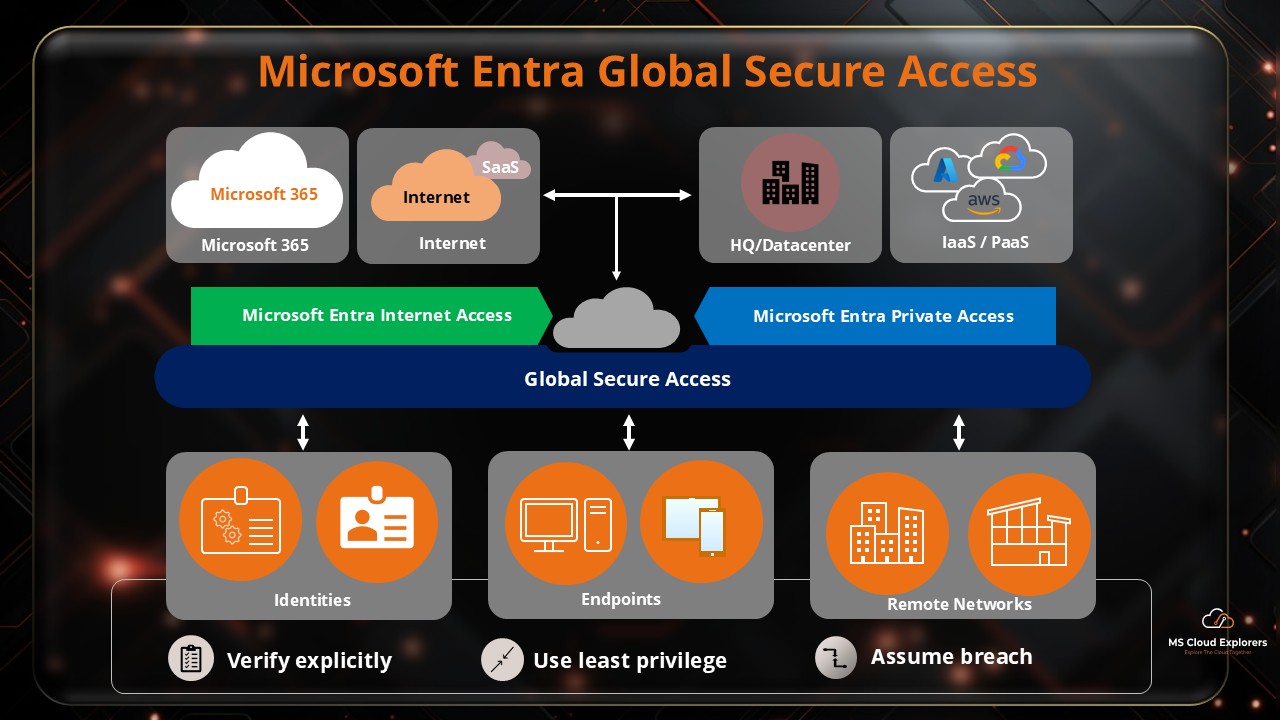
In today’s hybrid and cloud-first world, secure internet access has become more than just a firewall feature — it’s a mission-critical element of modern cybersecurity strategy. Enter Microsoft Global Secure Access — Microsoft’s latest innovation that combines identity-first security, global reach, and Zero Trust principles into one unified solution.
But what exactly is Entra Internet Access, and why should your organization care?
Let’s break it all down.
Understanding Microsoft Entra ID
What is Microsoft Entra?
Microsoft Entra is Microsoft’s unified identity and network access product family. It includes powerful tools like Entra ID (formerly Azure AD), Permissions Management, Verified ID, and now Internet and Private Access services.
Key Components of the Entra Family
- Microsoft Entra ID – Manages identities and access across environments.
- Entra Permissions Management – Controls and audits permissions at scale.
- Entra Verified ID – Provides verifiable credentials for digital identity.
- Entra Internet & Private Access – Redefines how users securely access apps and the internet.
Entra’s Role in Identity and Network Security
At its core, Entra protects access at every layer — from device to data — aligning with Microsoft’s Zero Trust model. With Entra Internet Access, this protection now extends directly to your users’ internet and SaaS app traffic.
What is Microsoft Global Secure Access?
Defining Global Secure Access
Global Secure Access (GSA) is the modern secure web gateway built into Microsoft’s ecosystem. It secures outbound internet traffic and cloud app access through identity-based policies.
Built on Zero Trust
GSA ensures that no access is trusted by default — it verifies the user, the device, the app, and the context every time.
Security Meets Simplicity
Instead of complex network routing and VPNs, GSA allows organizations to apply granular, identity-aware policies in real time. Think of it as a cloud-native, identity-first firewall for internet access.
Key Features of Microsoft Entra Internet Access
1. Internet Access Filtering and Control
Enforce rules for what types of websites or categories users can access based on identity, device, location, and risk level.
2. Identity-Centric Security
Unlike traditional network security tools, Entra uses user identity as the central decision-making factor.
3. Deep Integration with Microsoft 365
Protect tools like Exchange Online, SharePoint, and Teams without relying on third-party SWGs.
4. Risk-Based Conditional Access
Decisions are made using real-time signals like user behavior, session context, and sign-in risk.
5. Continuous Evaluation
Access isn’t just granted once — it’s continuously re-evaluated to respond to evolving threats instantly.
Architecture of Entra Internet Access
How It Works
Using Microsoft’s Global Secure Access service, user device traffic is routed through:
- Authenticates the identity
- Applies policy
- Routes or blocks access accordingly
Microsoft Edge Network Involvement
Entra leverages Microsoft’s massive global edge network, ensuring low latency and high performance, even during inline inspection.
Works Seamlessly with Entra Private Access
Together, Internet Access and Private Access offer full Secure Access Service Edge (SASE) coverage for public and private resources.
Benefits of Entra Internet Access
- No VPN Required: Truly modern and user-friendly experience.
- Comprehensive Protection: Secures both unmanaged and managed devices.
- Reduced Complexity: Native to Microsoft environments = easier deployment.
- Granular Insights: Integrated reporting and audit trails via Entra & Defender.
Use Cases
- Remote Worker Security: Protect users regardless of location or device.
- SaaS Protection: Monitor and secure traffic to apps like Google Workspace, Salesforce, etc.
- Shadow IT Control: Discover and block unauthorized SaaS usage.
- Data Exfiltration Prevention: Block risky uploads or unsanctioned data transfers.
Step-by-Step Configuration of Global Secure Access for Microsoft Traffic and Internet access Profiles
Prerequisites
- Microsoft Entra ID P1 or P2 for Microsoft Traffic
- Microsoft Entra Internet and Private Access required Microsoft Entra Suite
- Microsoft Defender for Cloud Apps (for deeper integration)
- Modern OS with Microsoft Global Secure Access Client
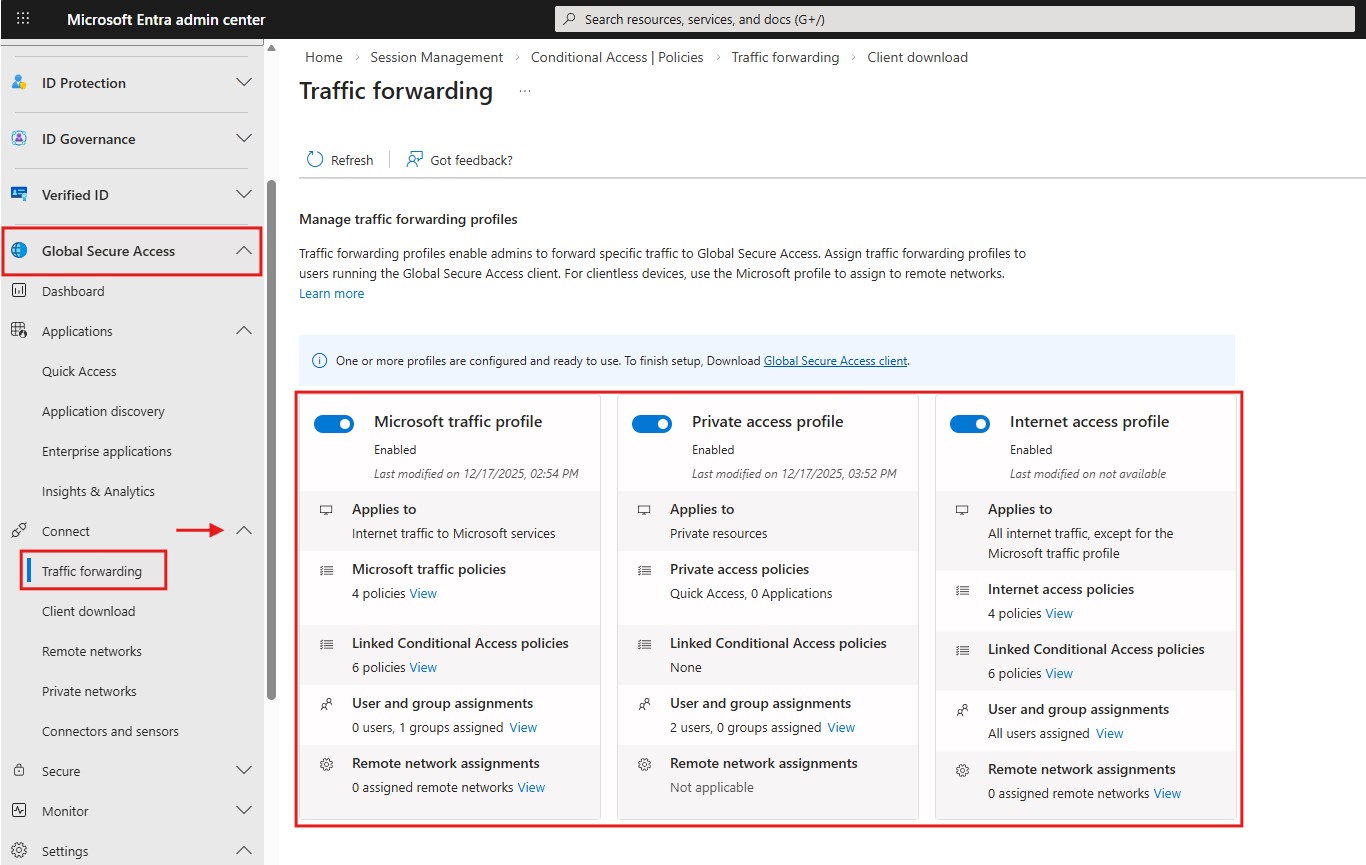
Enabling the Service
- Go to Microsoft Entra Admin Center
- Navigate to Global Secure Access
- Enable the Microsoft traffic profile and Internet access profile Under the Connect>Traffic forwarding.
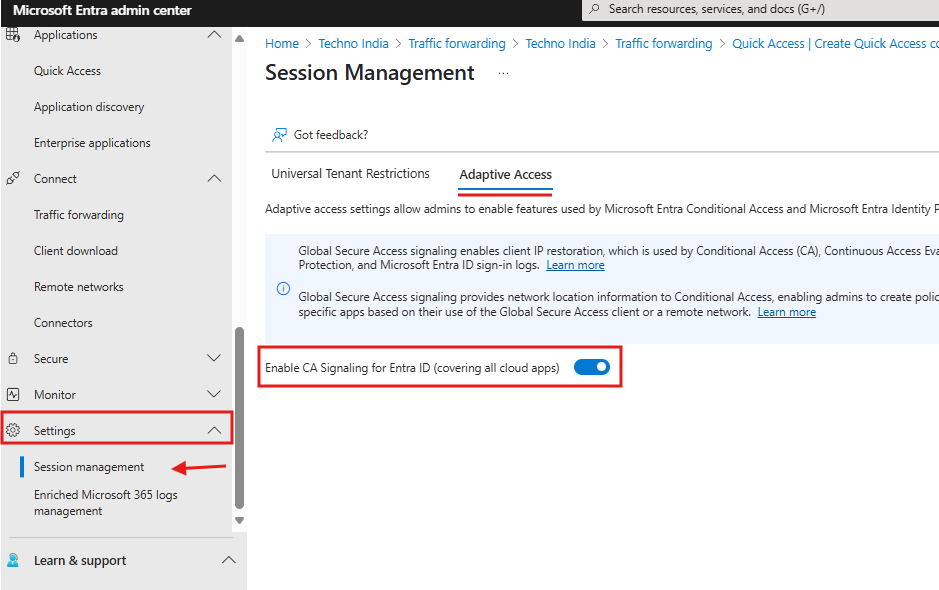
Setting Conditional Access
- Under the Settings Click on Session Management
- Under the Adaptive Access Tab Enable the CA Signaling settings
- Now you should see one more option in the Conditional Access Named Locations – All Compliant Network Locations.
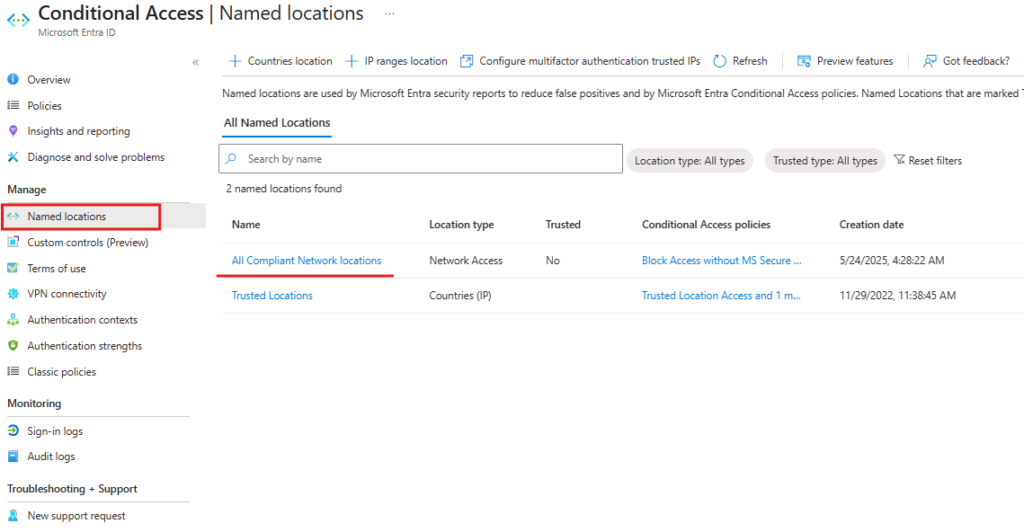
- Go to Policies and Create a new Policy.
- Users > Select the user or group whom you want to apply.
- Target resources > Select the all cloud apps or set the restriction only for Exchange and SharePoint Or All Cloud Apps.
- Conditions > Locations > Select to Any network or location and Exclude the All Compliant Network Locations,
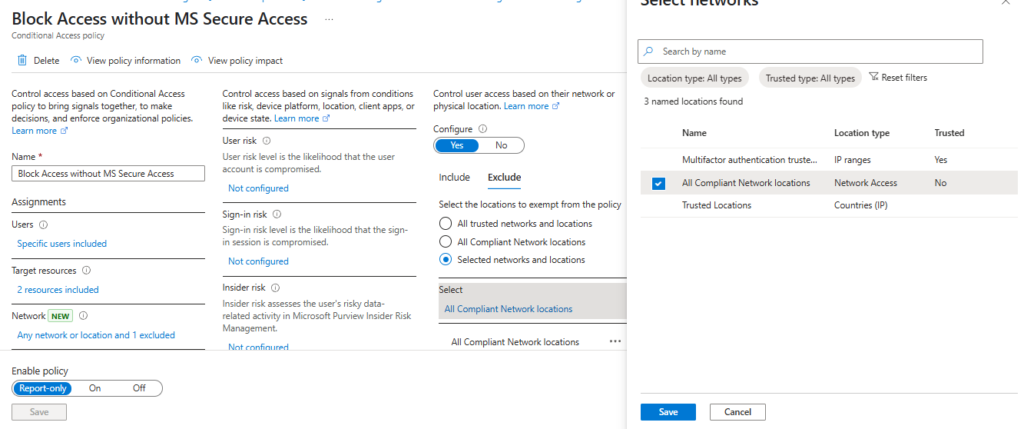
- Grant must be Block Access.
- Review the Policy and Turn on the Conditional Access Policy.
If you are interested to explore more about the conditional Access Policy please check out this blog – Top 7 Conditional Access Policies.
Step-by-Step Configuration of Global Secure Access for Microsoft
- Navigate to Global Secure Access
- Enable the Private Access Profile Under the Connect>Traffic forwarding. (Skip if you already enabled Previously)
- Click on the Connectors and Sensers Under the Connect.
- Under the Private Network Connectors Tab. Click on the Download Connector Service.
- Accept the terms and Download the connector on the Server.
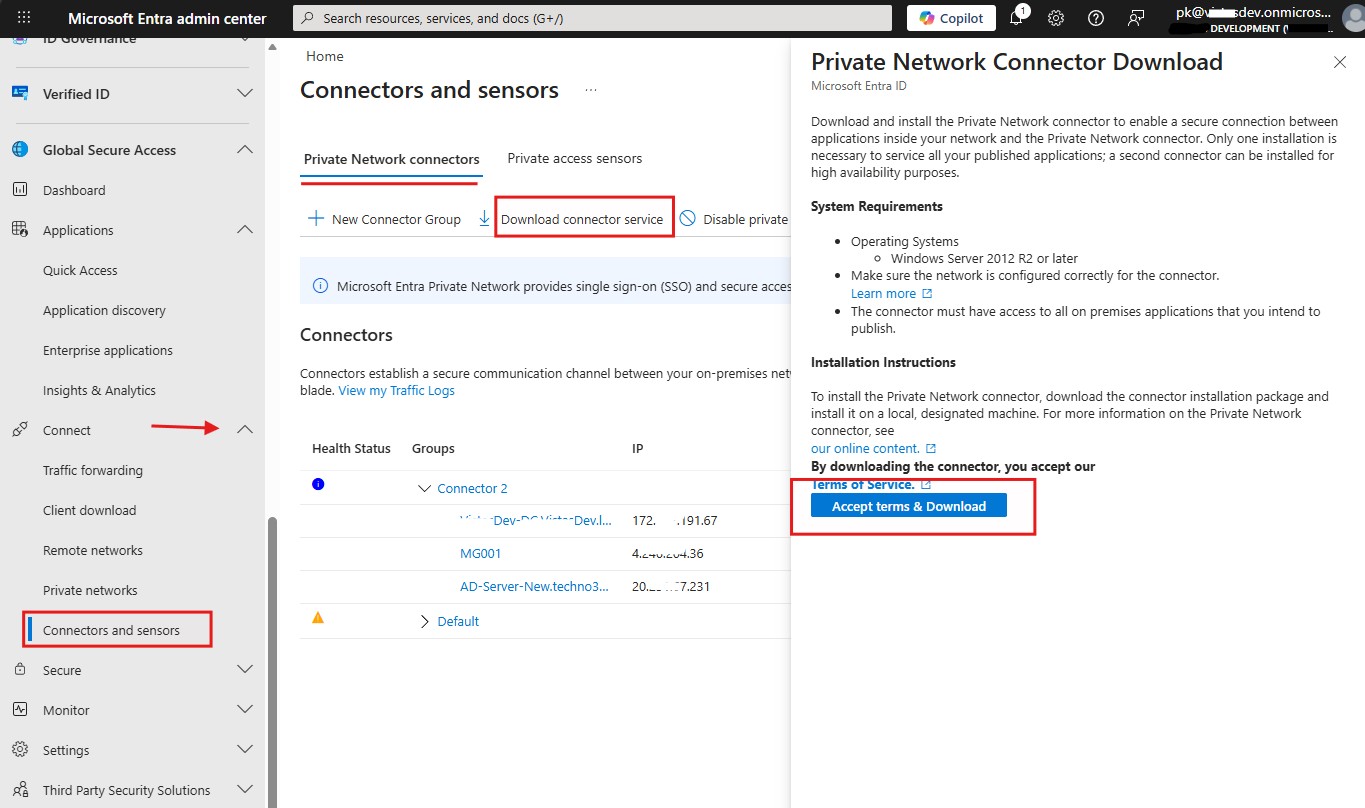
- Install the connector and Sign-in with Microsoft Global admin or Entra ID Admin.
- Once the Connector is installed you should see the Connector in Active state. Under the Connectors and Sensors section.
- You Can create new group connector or leave the default one.
- Create the Quick Access Group and Add the Connector group to it.
- Click on the Quick Access under the Applications.
- Select the Network Access Properties. Give the Name of Access group and Choose the Connector Group.
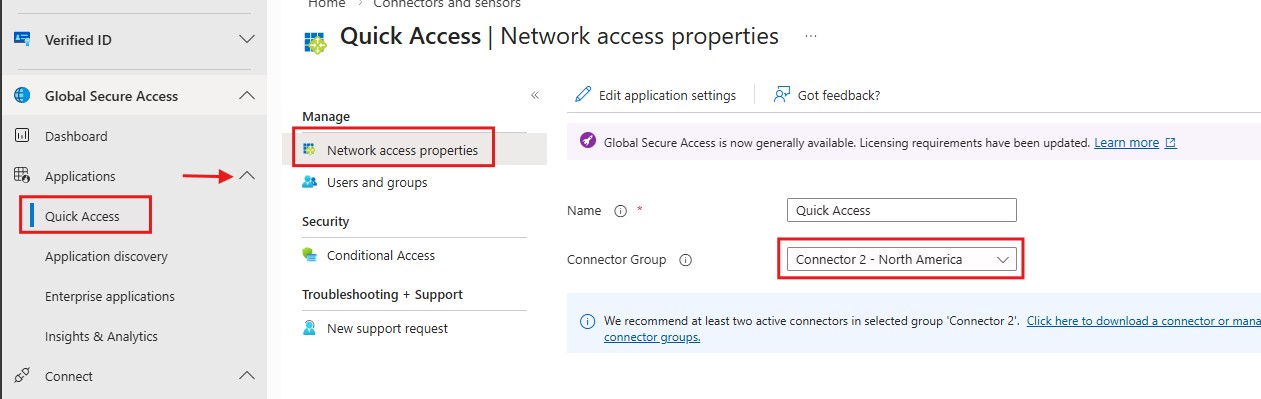 I have selected the Connector 2 in Your case might be different or Default.
I have selected the Connector 2 in Your case might be different or Default.- Now Create the App Segment. Click on the + Add Quick Access App. Side window will open to ask to create the segment.
For testing purposes I add the VM’s IP address, In your case might be Web Apps or Other resources.
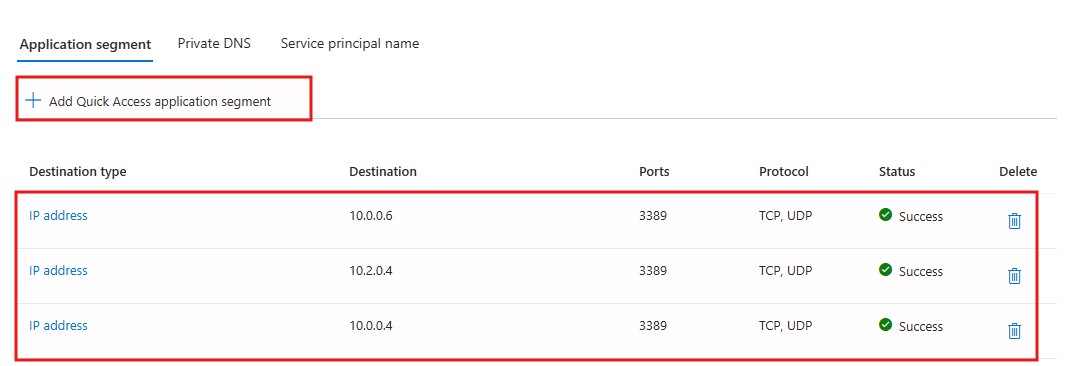
- This is completed, It;s Time to Add user or Group to the Entra Private Access.
- On the Same section Click on the Users and Group and choose the users that you want to test with them.
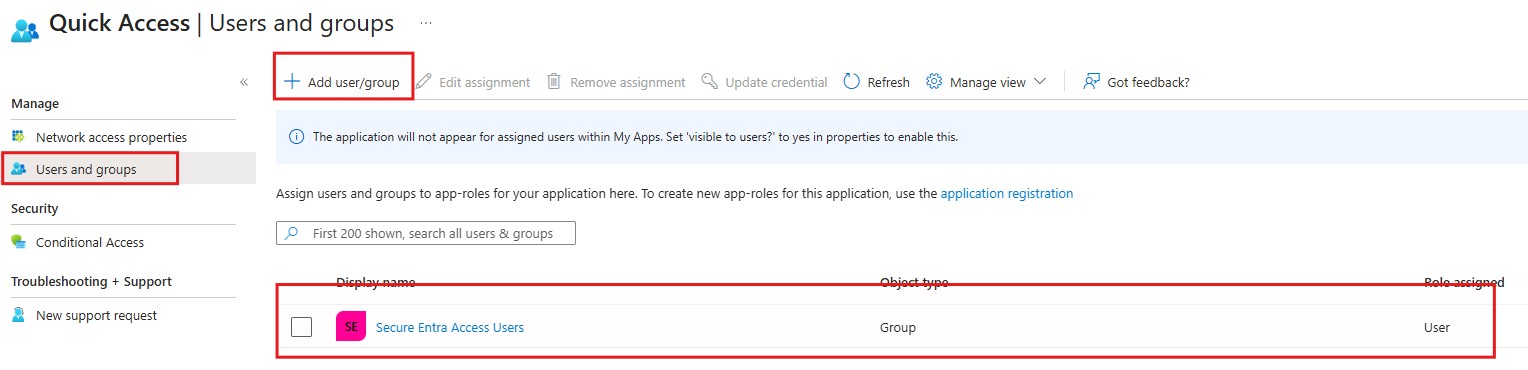
It’s Time to Check the End-user Behavior.
Download the Client and Install
- Click on the Client Download under the Connect.
- Select the Device type and Download the Client.
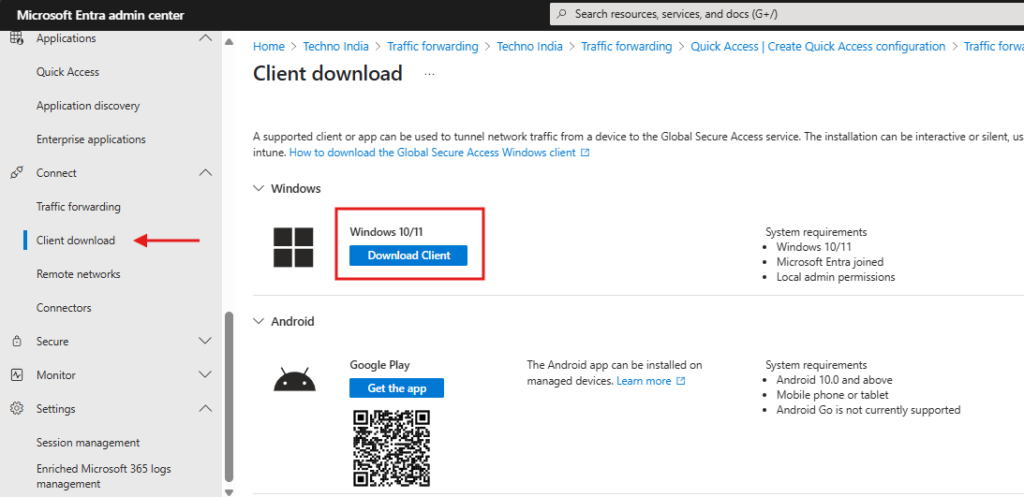
- Install the Client on the Microsoft Entra Joined Device. Make sure User has Local Admin access to install the client.
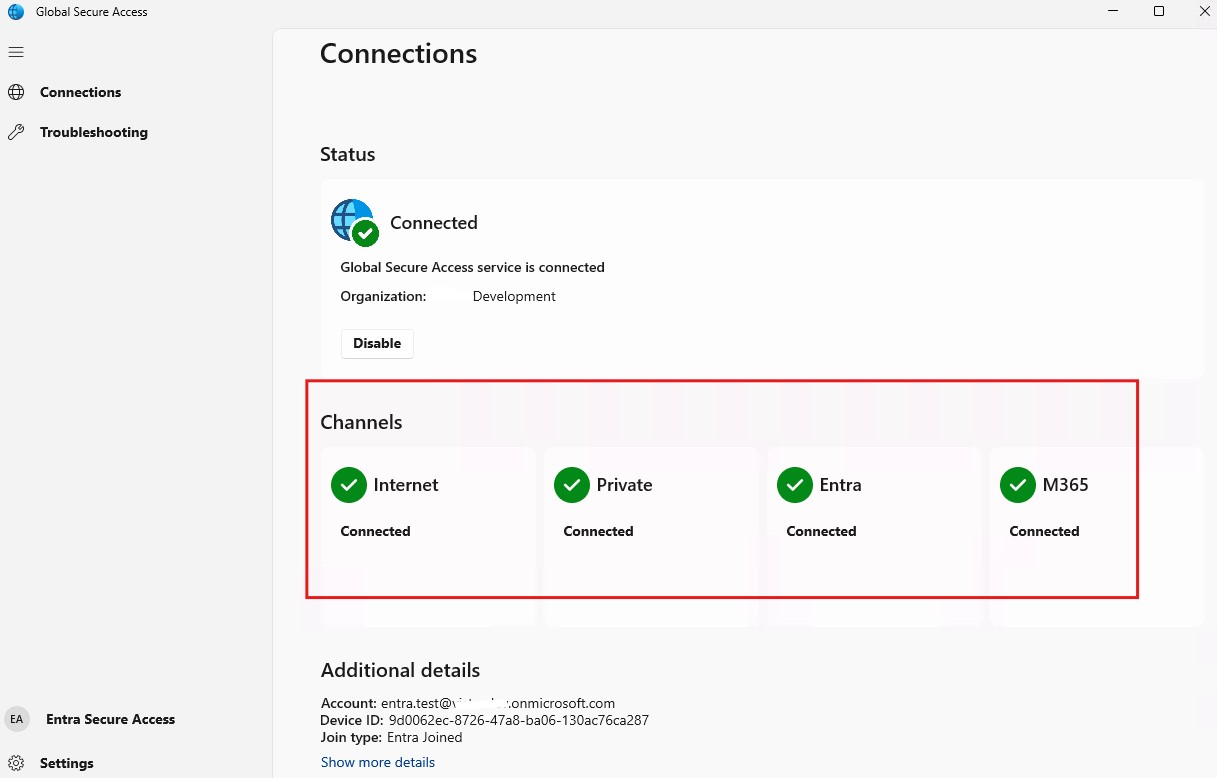
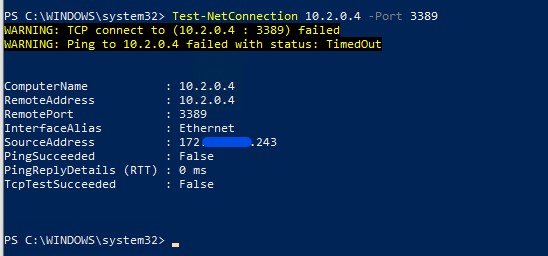
- Try connect you Microsoft 365 office apps and on-premises network Resources, For Me I added the VM. so I can take the RDP without any issue.
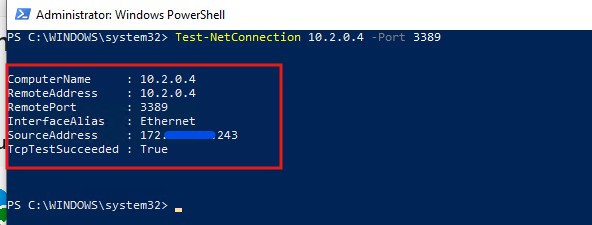
- Now you can try to Access your account on device without Connecting the Global Secure Access Connection.
- You will receive message You cannot access this right now similar below
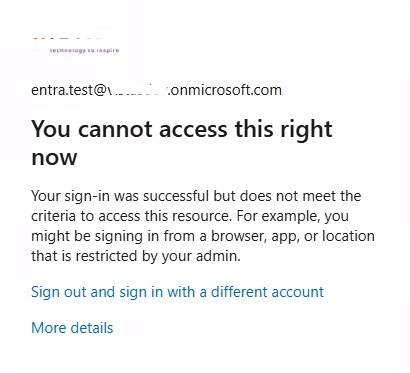
- Reconnect the Global Secure access client and you should see the difference and how it works.
Monitoring Traffic
- Use Monitor > Audit logs and Traffic logs for analytics
- Set up alerts for suspicious traffic
Traditional SWG vs. Entra Internet Access
| Feature | Traditional SWG | Entra Internet Access |
| Identity-Aware | ❌ | ✅ |
| Integrated with M365 | ❌ | ✅ |
| Zero Trust | Partial | ✅ |
| Real-Time Risk Signals | ❌ | ✅ |
| Cloud Native | ❌ | ✅ |
Integration with Microsoft Defender
By syncing with Microsoft Defender for Endpoint and Defender for Cloud Apps, Entra enables:
- Threat Detection
- Behavioral Risk Scoring
- Automated Incident Response
Final Thoughts
If you’re managing a hybrid or cloud-native environment, Microsoft Entra Internet Access is a no-brainer. It delivers secure, fast, and identity-driven internet access — all from a name you already trust. Say goodbye to complex web gateways and hello to modern security.
FAQs
1. What is the difference between Entra Internet Access and Entra Private Access?
Entra Internet Access secures traffic to public internet and SaaS apps, while Private Access protects access to internal resources like legacy apps or internal APIs.
2. Do I need Defender for Cloud Apps to use Entra Internet Access?
It’s not required but highly recommended for deep app visibility and risk detection.
3. How does Entra Internet Access support Zero Trust?
By verifying identity, device, and context before allowing access, and continuously monitoring sessions.
4. Can I use it with non-Microsoft SaaS apps?
Yes! Apps like Salesforce, Dropbox, and Google Workspace are supported through conditional access and Defender for Cloud Apps integration.
5. Is Entra Internet Access a replacement for VPN?
For internet and SaaS traffic — absolutely yes. For private network resources, combine it with Entra Private Access.
Explore More From MS Cloud Explorers
- Azure AD Free vs. Premium P1 & P2: Which Edition Is Right for Your Business?
- Microsoft Entra ID Identity Protection: A Complete Guide to Securing Your Environment
- Top 7 Conditional Access Policies Every Organization Should Implement
- A Complete Guide to Privileged Identity Management in Azure AD (PIM)
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!


Really helpful summary! Global Secure Access seems like a big step forward for securing hybrid work. Thanks for making it easy to understand.