- January 16, 2026
- Pankaj Kumar
- 0
In today’s hybrid, cloud-first business environment, identity is the new security perimeter. The days of relying solely on firewalls and passwords are gone. Now, organizations must verify who is accessing what, from where, and on what device—and take action accordingly.
This powerful identity-driven policy engine allows you to enforce security decisions in real-time based on signals like user location, device compliance, risk levels, and more. Whether you’re managing access to Microsoft 365, Teams, SharePoint, or third-party SaaS apps, these policies are key to Zero Trust security.
In this guide, we break down the top Conditional Access policies every admin should implement—and how to configure them using Microsoft’s Entra ID built-in templates.
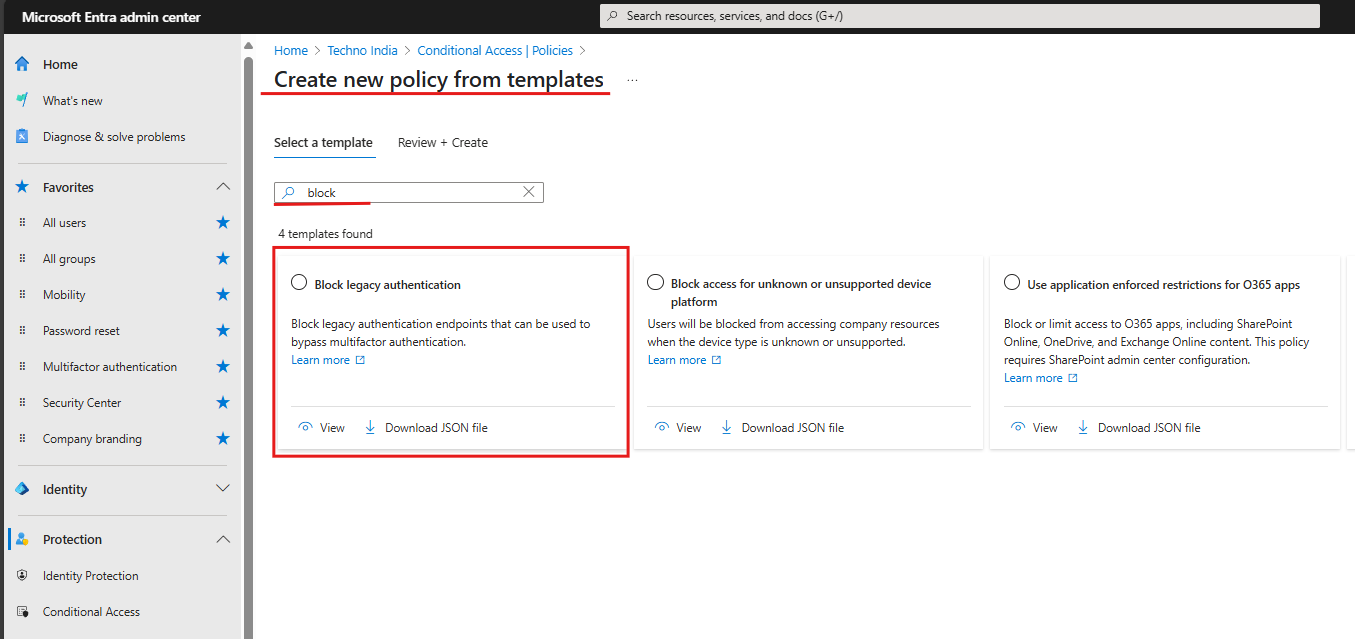 💡 Tip: If you’re new to Entra ID, it’s recommended to create policies using the “+ New policy from template” option. Make sure to set the policy to Report-only mode during creation. You can modify the settings after the policy is created. Also, ensure that you exclude any break-glass accounts from Conditional Access to avoid being locked out.
💡 Tip: If you’re new to Entra ID, it’s recommended to create policies using the “+ New policy from template” option. Make sure to set the policy to Report-only mode during creation. You can modify the settings after the policy is created. Also, ensure that you exclude any break-glass accounts from Conditional Access to avoid being locked out.
 💡 Customize: Add risky regions or anonymous IP detections for tighter control.
💡 Customize: Add risky regions or anonymous IP detections for tighter control.
 💡 Customize: When creating a Conditional Access policy from a template, make sure the policy state is set to Report-only or Off. Once the policy is created, you can modify it, exclude the break-glass account, and then enable the policy.
💡 Customize: When creating a Conditional Access policy from a template, make sure the policy state is set to Report-only or Off. Once the policy is created, you can modify it, exclude the break-glass account, and then enable the policy.
 💡 Customize: You can tailor compliance policies per platform (Windows, iOS, Android, macOS).
💡 Customize: You can tailor compliance policies per platform (Windows, iOS, Android, macOS).
 💡 Customize: Combine with limited web access or block download controls for even more protection.
💡 Customize: Combine with limited web access or block download controls for even more protection.
🔒 1. Block Legacy Authentication
Why it matters: Legacy protocols like POP, IMAP, and SMTP don’t support MFA and are often targeted in brute-force and password spray attacks. What it does: Blocks sign-ins using outdated, insecure protocols. How to implement:- Go to Entra ID > Protection > Conditional Access > New Policy
- Name: “Block Legacy Authentication”
- Users: All Users
- Target Resources: All resources
- Conditions > Client apps: Select legacy authentication clients (Exchange ActiveSync Clients and Other Clients)
- Access controls > Grant: Block access
 💡 Tip: If you’re new to Entra ID, it’s recommended to create policies using the “+ New policy from template” option. Make sure to set the policy to Report-only mode during creation. You can modify the settings after the policy is created. Also, ensure that you exclude any break-glass accounts from Conditional Access to avoid being locked out.
💡 Tip: If you’re new to Entra ID, it’s recommended to create policies using the “+ New policy from template” option. Make sure to set the policy to Report-only mode during creation. You can modify the settings after the policy is created. Also, ensure that you exclude any break-glass accounts from Conditional Access to avoid being locked out.
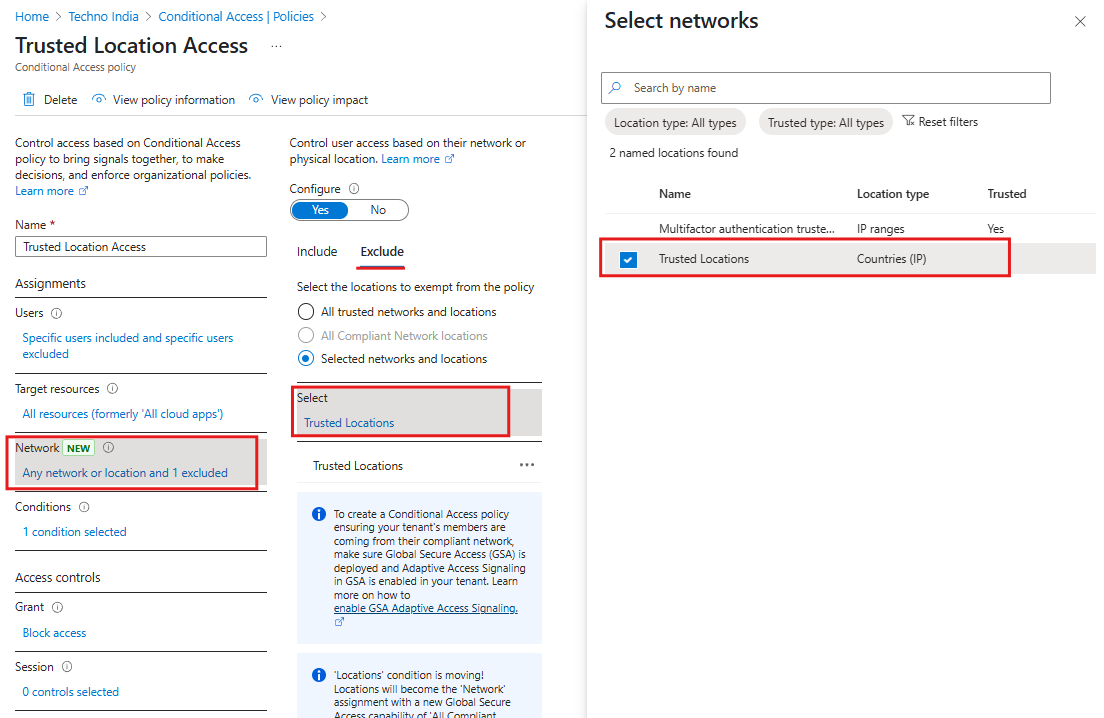
🌍 2. Location-Based Access
Why it matters: Limiting access from untrusted locations reduces the attack surface, especially for global teams or remote workers. What it does: Blocks or allows access based on country or IP range. How to implement:- Go to Named Locations in Entra ID and define IP ranges or Locations(e.g., office Location)
- Select the Countries Locations or IP ranges location.
- Name: Trusted Locations or Office Locations. Choose the Locations and Create.
- Create a new policy: “Block Access from Non-Trusted Locations”
- Users: All Users (Exclude the Break-Glass Account)
- Target Resources: All resources
- Network> Include: Any network or location, Exclude: Select the network and locations and add the Trusted locations.
- Access controls > Grant: Block access
- Grant: Block access.
 💡 Customize: Add risky regions or anonymous IP detections for tighter control.
💡 Customize: Add risky regions or anonymous IP detections for tighter control.
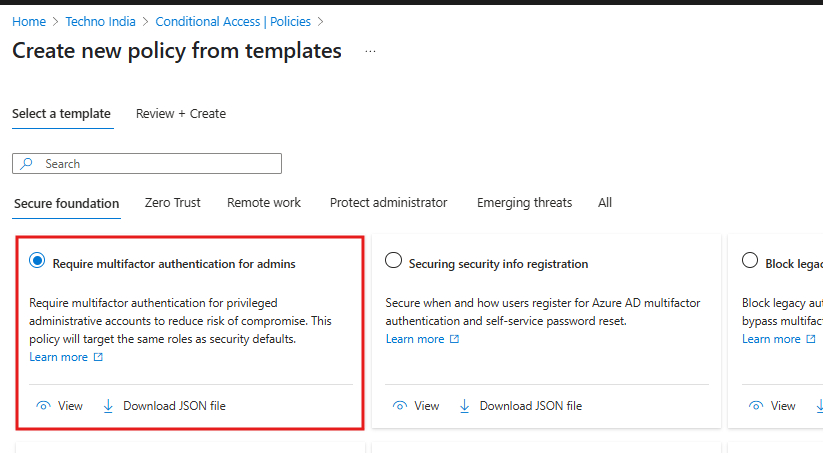
🛡️ 3. MFA for All Admin Accounts
Why it matters: Admin accounts have elevated privileges and are top targets for cyber attackers. A single compromised global admin could lead to a full-blown breach. What it does: Forces MFA for all users in privileged roles (like Global Administrator, Exchange Admin, SharePoint Admin, etc.). How to implement:- Use built-in “Require MFA for Admins” template
- Navigate to Conditional Access > Policies > New Policy from Template
- Select the template and apply it to Directory roles
 💡 Customize: When creating a Conditional Access policy from a template, make sure the policy state is set to Report-only or Off. Once the policy is created, you can modify it, exclude the break-glass account, and then enable the policy.
💡 Customize: When creating a Conditional Access policy from a template, make sure the policy state is set to Report-only or Off. Once the policy is created, you can modify it, exclude the break-glass account, and then enable the policy.
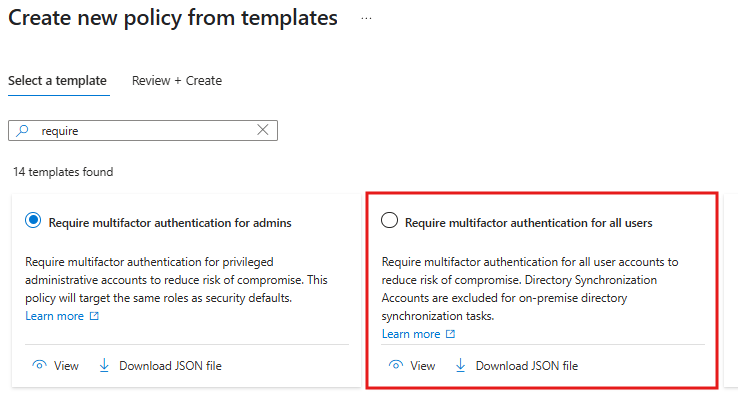
🔐 4. MFA for All Users
Why it matters: Passwords alone are no longer enough. MFA is a must for securing everyday user access. What it does: Requires users to verify their identity with something they have (like a phone or security key) after entering their password. How to implement:- Policy Name: “Require MFA for All Users”
- Navigate to Conditional Access > Policies > New Policy from Template
- Choose the Require MFA for all Users.

- Review the template and click on Create.
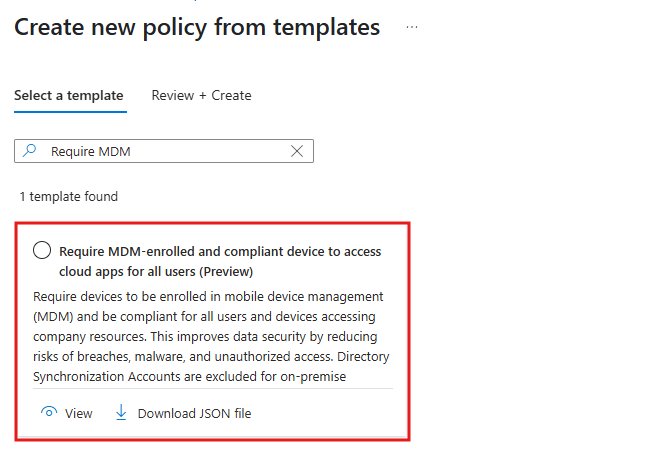
📱 5. Compliant Device Access for Intune-Managed Devices
Why it matters: Only allowing Intune-compliant devices helps ensure users are logging in from secure, managed endpoints. What it does: Blocks access from devices that aren’t enrolled in Intune or not compliant with your security standards. How to implement:- Go to Intune > Devices > Compliance policies and define compliance rules (antivirus, encryption, OS version, etc.)
- Create Conditional Access policy:
- Navigate to Conditional Access > Policies > New Policy from Template
- Users: Intune User Group or Compliant device group
- Cloud apps: All
- Grant: Require device to be marked as compliant
 💡 Customize: You can tailor compliance policies per platform (Windows, iOS, Android, macOS).
💡 Customize: You can tailor compliance policies per platform (Windows, iOS, Android, macOS).
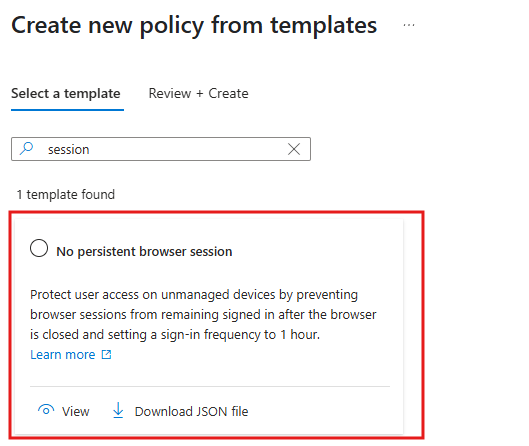
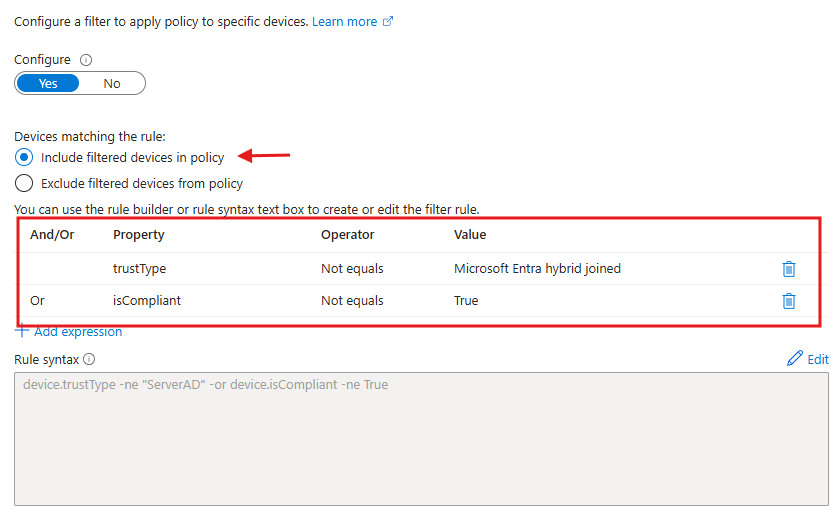
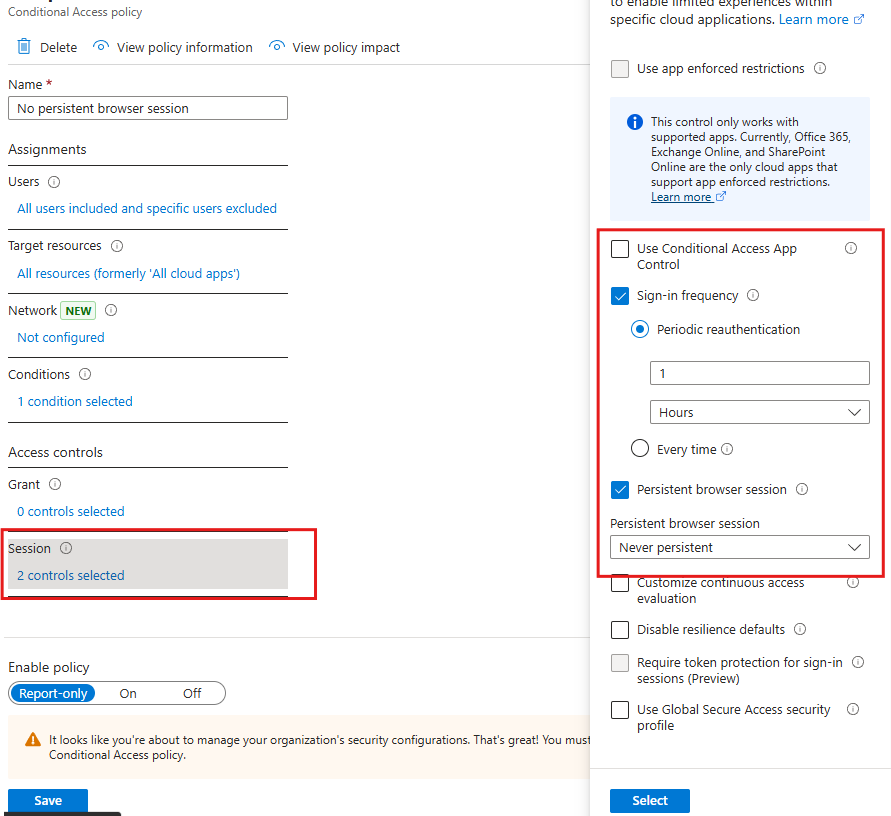
🕒 6. Session Timeout for Unmanaged Devices
Why it matters: Unmanaged or personal devices often lack endpoint protection. Limiting session length on these devices reduces risk exposure. What it does: Sets session controls to timeout access or sign out users after a specified time when using non-compliant/unmanaged devices. How to implement:- Navigate to Conditional Access > Policies > New Policy from Template

- Assign to All Users
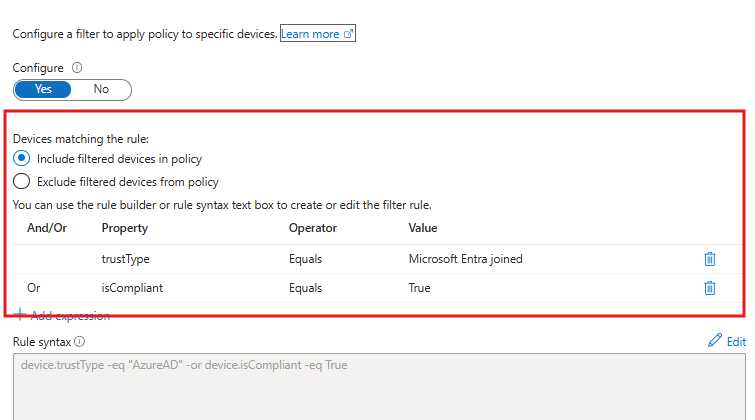
- Conditions > Filter for Devices: Select “Device not marked as compliant”

- Session controls: Sign-in frequency (e.g., 1 hour)
 💡 Customize: Combine with limited web access or block download controls for even more protection.
💡 Customize: Combine with limited web access or block download controls for even more protection.
✅ 7. Bypass MFA on Intune Compliant Devices
Why it matters: Too many MFA prompts annoy users. If a device is already trusted and compliant, you can skip MFA to improve the user experience. What it does: Allows seamless sign-ins on enrolled and compliant devices while keeping MFA for untrusted ones. How to implement:- Policy Name: “Bypass MFA on Compliant Devices”
- Users: Intune User group
- Conditions > Device State: Include “Compliant”

- Grant: Require device to be marked as compliant.
⚠️ Bonus: Require Password Change for High-Risk Users
Why it matters: If Entra Identity Protection detects a high user risk (e.g., leaked credentials, strange sign-ins), it can force a password reset immediately. What it does: Automates remediation by requiring high-risk users to reset their password before they can continue accessing resources. How to create it:- Go to Entra ID > Identity Protection
- User risk policy > Create policy
- Assign to all users
- Action: Require password change
🔧 How to Use Conditional Access policies Templates
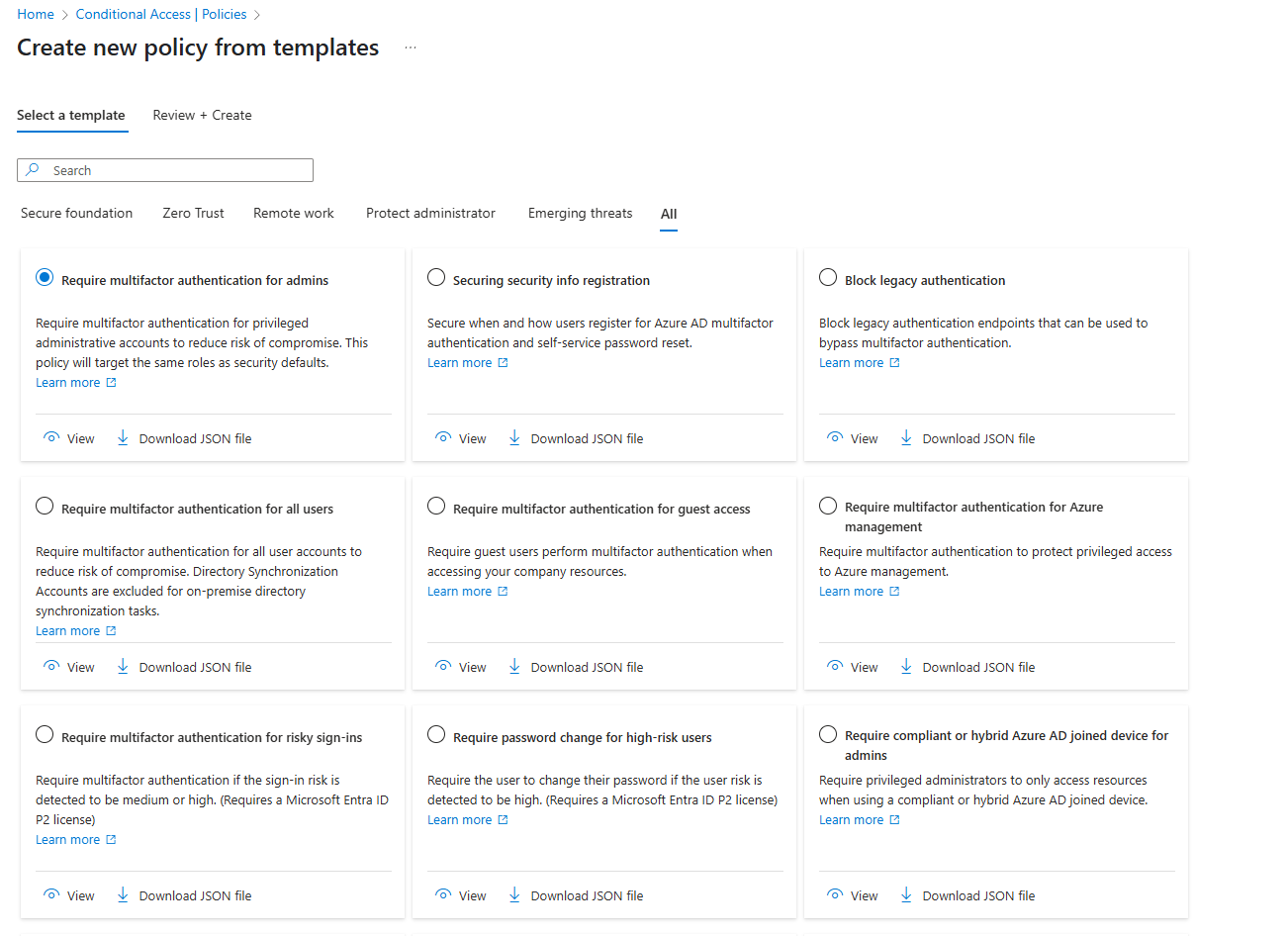
Skip building policies from scratch! Microsoft offers dozens of best-practice templates for common scenarios like Zero Trust, secure remote work, and identity protection: How to use them:- Navigate to Entra ID > Security > Conditional Access > Policies
- Click “+ New policy from template (Preview)”
- Choose from categories like Zero Trust, Identity Protection, Remote work, etc.
- Select the templates you want (e.g., Require MFA for Admins, Block Legacy Auth)
- Review, customize, and enable
- User groups
- App targets
- Grant controls
- Session controls

✅ Best Practices for Conditional Access Policies
- 🧪 Start in report-only mode before enforcing live.
- 🔒 Always exclude break-glass accounts and monitor them closely.
- 🧾 Document policy intent and logic.
- 🔁 Review policies quarterly—especially after org changes.
🔚 Conclusion
Conditional Access isn’t just a Microsoft buzzword—it’s one of the most powerful tools in your security toolkit. By implementing these top 7 Conditional Access policies, your organization builds a strong identity perimeter that adapts to modern threats while still offering a smooth experience for your users. Start with built-in templates, then refine and tailor them to your unique needs. And remember—security isn’t one-and-done. Review and evolve your policies regularly to stay one step ahead.❓FAQs
- What is Conditional Access in Microsoft Entra ID? Conditional Access lets you control access to apps and data based on signals like user location, device state, risk level, and more.
- Is MFA required for all users by default? Not unless you enable it via Conditional Access or Security Defaults. It’s highly recommended for everyone.
- What’s the difference between compliant and non-compliant devices? Compliant devices meet your Intune policies (like encryption, antivirus, etc.), while non-compliant devices don’t and are considered higher risk.
- Can I test Conditional Access policies before enforcing them? Yes! Use report-only mode to simulate policies and analyze their impact without blocking access.
- How often should I review my Conditional Access policies? Quarterly reviews are ideal. Also, revisit them after major changes like new app rollouts or user onboarding.
Explore More from MS Cloud Explorers
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!