
Microsoft recently announced its new Zero Trust Assessment tool, a major addition designed to help organizations evaluate and strengthen their security posture. In this blog, we’ll break down what the tool does, why it matters, and how you can run it in your own tenant. You’ll learn what the tool analyzes, which insights it provides, and how it identifies hidden configuration gaps that may be putting your Microsoft 365 environment at risk.
This update is especially valuable for small and mid-sized organizations that may not have large security teams—and often assume that enabling MFA alone is enough. With the Zero Trust Assessment, you’ll get a clear view of your current security weaknesses along with practical, prioritized recommendations to help you move toward a true Zero Trust posture.
What is Zero Trust?
Zero Trust is a modern cybersecurity framework built on the principle that no user, device, or network request should be trusted by default—regardless of where it comes from. It is guided by three core principles:
- Verify Explicitly
Every access request must be validated using signals such as identity, device health, location, risk level, and user behavior.
- Enforce Least Privilege Access
Users and workloads should receive only the permissions they need, using approaches like:
- Just-in-Time (JIT) access
- Just-Enough-Access (JEA)
- Role-Based Access Control (RBAC)
- Adaptive Conditional Access policies
- Assume Breach
Continuously monitor the environment and operate as though a threat may already exist. This helps limit lateral movement, reduce impact, and strengthen threat detection and response.
Why Zero Trust Is Important Today
Traditional perimeter-based security models cannot support modern environments. Zero Trust is essential due to:
- Hybrid and remote work
- Increased SaaS adoption
- Rising supply-chain and identity-based attacks
- Compliance and regulatory requirements
- Cloud-first modernization
Zero Trust helps organizations reduce misconfigurations, strengthen governance, and align with standards such as NIST, CISA, and CIS frameworks.
Introducing Microsoft’s Zero Trust Assessment
Microsoft’s Zero Trust Assessment is a free, PowerShell-based tool that evaluates your tenant against Microsoft’s Zero Trust principles. It highlights risks, identifies gaps, and provides clear, prioritized remediation steps.
Key facts about the tool:
- Currently in public preview
- Focuses on the Identity and Device pillars
- Additional pillars (Apps, Data, Network, Infrastructure, SOC) will be added later
- Every finding includes a direct link to the admin portal to fix the issue quickly
This makes it one of the most practical tools for IT admins who want to benchmark their Zero Trust maturity.
What the Zero Trust Assessment Report Includes
The tool generates a detailed, interactive report that highlights:
- Tests performed
- Pass/Fail status
- Risk severity
- User impact
- Implementation effort
- Remediation recommendations
- Links to admin portal pages for immediate action
These tests are aligned with Microsoft baselines, NIST/CISA/CIS guidance, and real-world security scenarios.
Prerequisites and Requirements
Before running the tool, ensure the following:
- Tenant Permissions
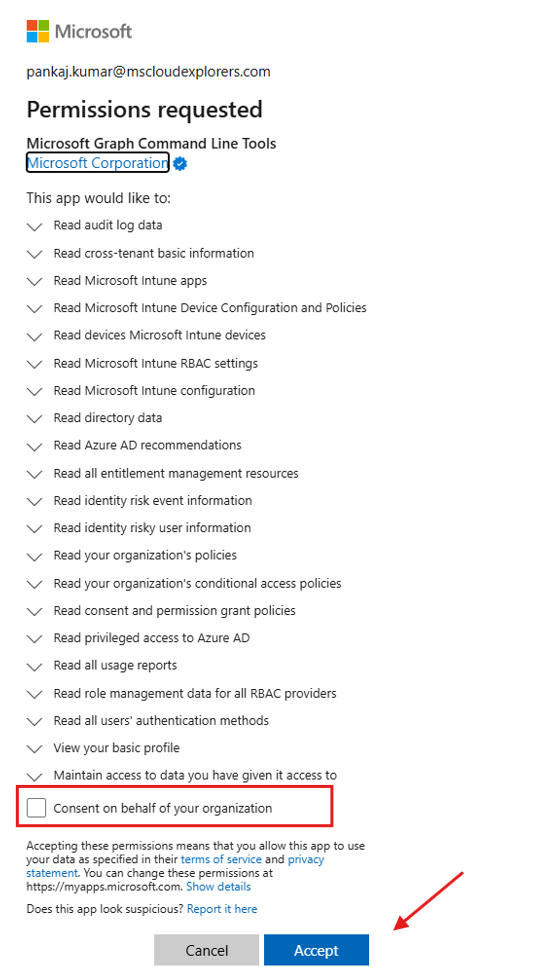
Global Admin to require accept the Consent
- PowerShell Environment
A machine with:
- PowerShell 7+ (recommended)
- Permission to install modules
How to Run the Zero Trust Assessment (Step-by-Step)
Running the assessment is straightforward and requires only three commands:
Step 1: Install the Module
PowerShell
Install-Module ZeroTrustAssessment -Scope CurrentUserStep 2: Connect to Your Tenant
PowerShell
Connect-ZtAssessmentAccept the Consent for all apps and follow the sign-in prompts for Microsoft Graph and Azure.
Step 3: Run the Assessment
PowerShell
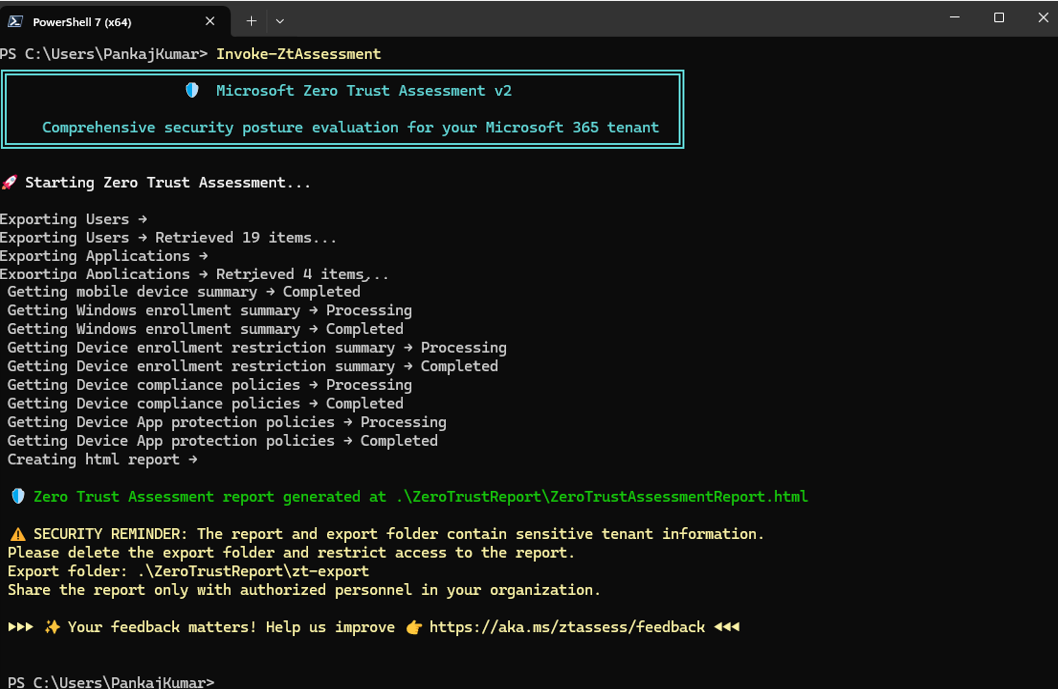
Invoke-ZtAssessmentFor large tenants, expect the scan to take several hours.
After completion, an interactive report will be displayed with all findings and recommendations.
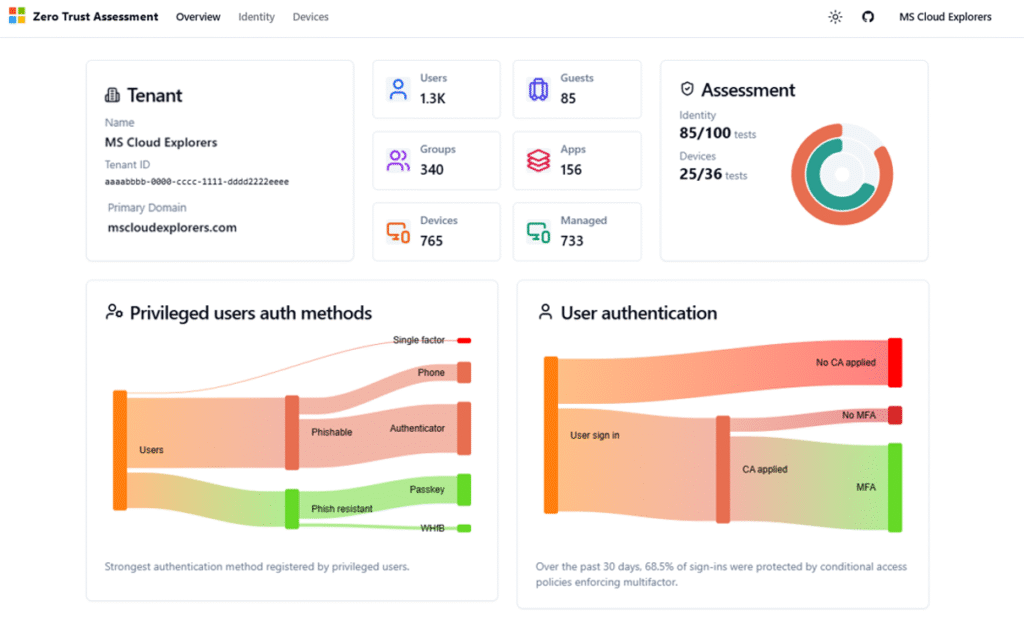
How to Interpret the Zero Trust Assessment Results
When reviewing the report, prioritize findings based on:
- Risk Level – Address high-risk items that directly affect identity and device security.
- User Impact – Focus on improvements that strengthen security without causing major disruption.
- Implementation Effort – Target quick, high-value fixes such as:
Identity & Devices
This Zero Trust Assessment Report provides a detailed overview of your organization’s Zero Trust posture based on Microsoft Entra and Intune security best practices. You can review the identified risks and plan the necessary changes to improve your overall security posture.
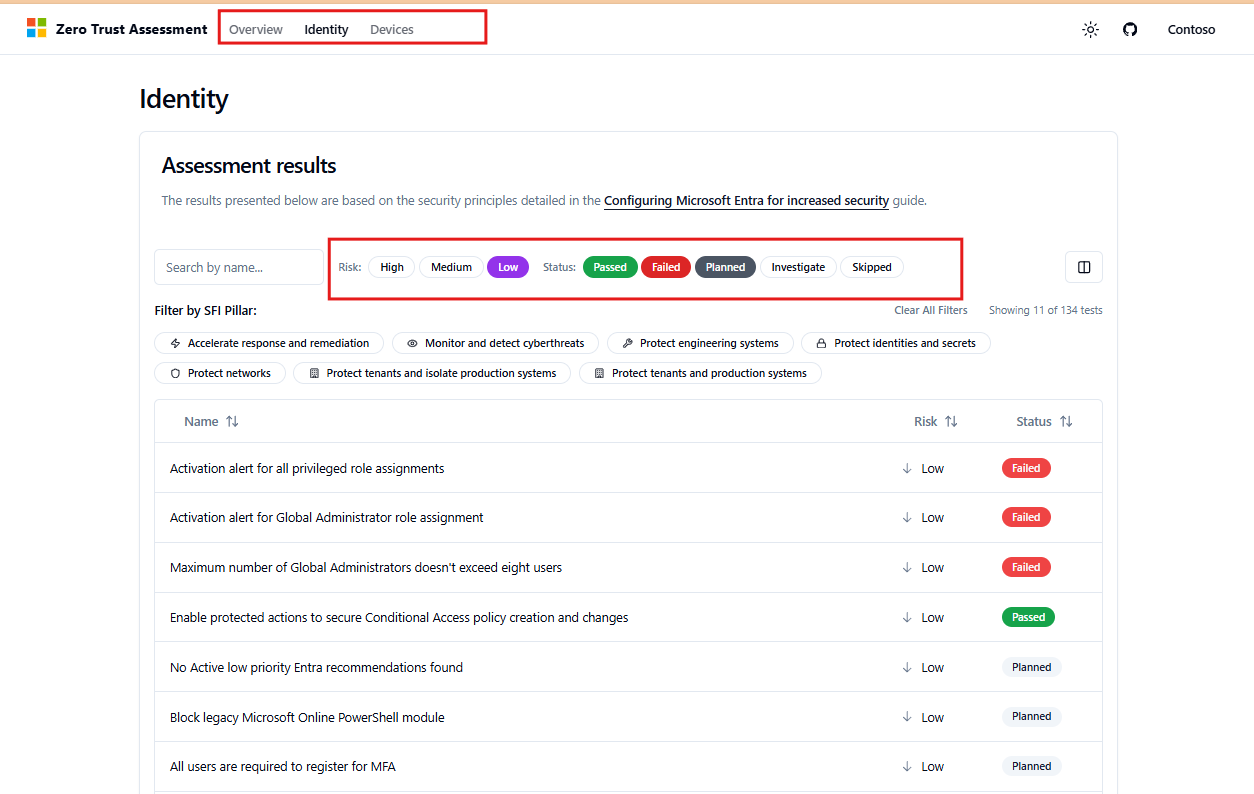
When you click on a risk item, a window will appear that provides more information about the issue, along with the configuration steps needed to resolve it.
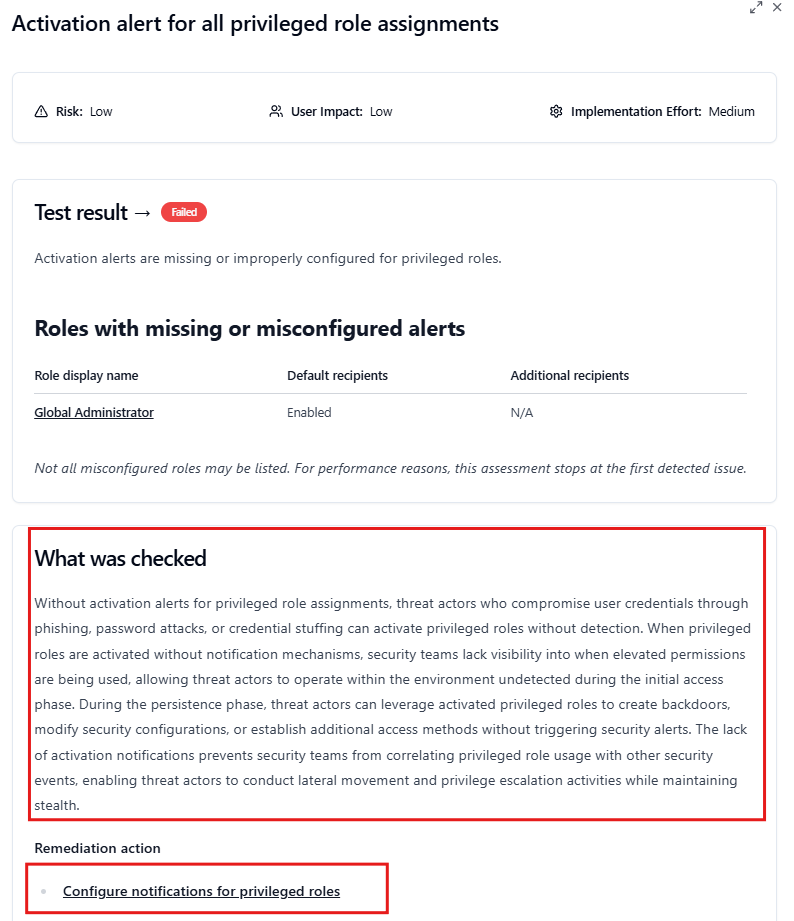
Governance and Ongoing Progress Tracking
To maintain a strong Zero Trust posture:
- Run the Zero Trust Assessment every quarter
- Use findings to guide your security roadmap
- Share measurable improvements with leadership
- Align operations with Microsoft’s seven Zero Trust pillars
- Integrate assessment outcomes into your governance lifecycle
Conclusion
Microsoft’s Zero Trust Assessment is a powerful and easy-to-use tool that helps IT teams uncover security gaps and strengthen their Microsoft 365 environment. Whether your organization is early in its Zero Trust journey or has limited security resources, this tool provides clear, actionable steps to improve identity, device, and access security. Running the assessment regularly ensures continuous improvement and moves you closer to a resilient, modern Zero Trust security model.
FAQs
- What is the Zero Trust Assessment tool?
A free Microsoft tool that scans your tenant and identifies security gaps based on Zero Trust best practices. - Why should I run it?
To uncover misconfigurations, assess risks, and receive actionable recommendations to strengthen your Microsoft 365 security posture. - Does it modify my tenant?
No. The tool is read-only and does not make any changes. - What pillars does it assess?
The current preview evaluates the Identity and Device pillars, with more pillars coming soon. - How often should I run it?
Run it quarterly or after major configuration changes.
Related Links:
- Top 7 Microsoft Entra ID Conditional Access Policies
- Complete Guide of Microsoft Entra Privileged Identity Management
- Microsoft 365 Security Audit Guide with Complete information
- The Ultimate Guide to Manage and Improve Microsoft Secure Score
Enjoyed the article?
We’d love to hear your thoughts—share your comments below!
For more insights, guides, and updates from the Microsoft ecosystem, be sure to subscribe to our newsletter and follow us on LinkedIn. Stay connected and never miss out on the latest tips and news!


















8 comments on “Microsoft Zero Trust Assessment: A Step-by-Step Guide for IT Admins”